Who is the Network Access Broker ‘Wazawaka?’
In a great many ransomware attacks, the criminals who pillage the victim’s network are not the same crooks who gained the initial access to the victim organization. More commonly, the infected PC or stolen VPN credentials the gang used to break in were purchased from a cybercriminal middleman known as an initial access broker. This post examines some of the clues left behind by “Wazawaka,” the hacker handle chosen by a major access broker in the Russian-speaking cybercrime scene.

Wazawaka has been a highly active member of multiple cybercrime forums over the past decade, but his favorite is the Russian-language community Exploit. Wazawaka spent his early days on Exploit and other forums selling distributed denial-of-service (DDoS) attacks that could knock websites offline for about USD $80 a day. But in more recent years, Wazawaka has focused on peddling access to organizations and to databases stolen from hacked companies.
“Come, rob, and get dough!,” reads a thread started by Wazawaka on Exploit in March 2020, in which he sold access to a Chinese company with more than $10 billion in annual revenues. “Show them who is boss.”
According to their posts on Exploit, Wazawaka has worked with at least two different ransomware affiliate programs, including LockBit. Wazawaka said LockBit had paid him roughly $500,000 in commissions for the six months leading up to September 2020.
Wazawaka also said he’d teamed up with DarkSide, the ransomware affiliate group responsible for the six-day outage at Colonial Pipeline last year that caused nationwide fuel shortages and price spikes. The U.S. Department of State has since offered a $5 million reward for information leading to the arrest and conviction of any DarkSide affiliates.
Wazawaka seems to have adopted the uniquely communitarian view that when organizations being held for ransom decline to cooperate or pay up, any data stolen from the victim should be published on the Russian cybercrime forums for all to plunder — not privately sold to the highest bidder. In thread after thread on the crime forum XSS, Wazawaka’s alias “Uhodiransomwar” can be seen posting download links to databases from companies that have refused to negotiate after five days.
“The only and the main principle of ransomware is: the information that you steal should never be sold,” Uhodiransomwar wrote in August 2020. “The community needs to receive it absolutely free of charge if the ransom isn’t paid by the side that this information is stolen from.”
Wazawaka hasn’t always been so friendly to other cybercrooks. Over the past ten years, his contact information has been used to register numerous phishing domains intended to siphon credentials from people trying to transact on various dark web marketplaces. In 2018, Wazawaka registered a slew of domains spoofing the real domain for the Hydra dark web market. In 2014, Wazawaka confided to another crime forum member via private message that he made good money stealing accounts from drug dealers on these marketplaces.
“I used to steal their QIWI accounts with up to $500k in them,” Wazawaka recalled. “A dealer would never go to the cops and tell them he was selling stuff online and someone stole his money.”
WHO IS WAZAWAKA?
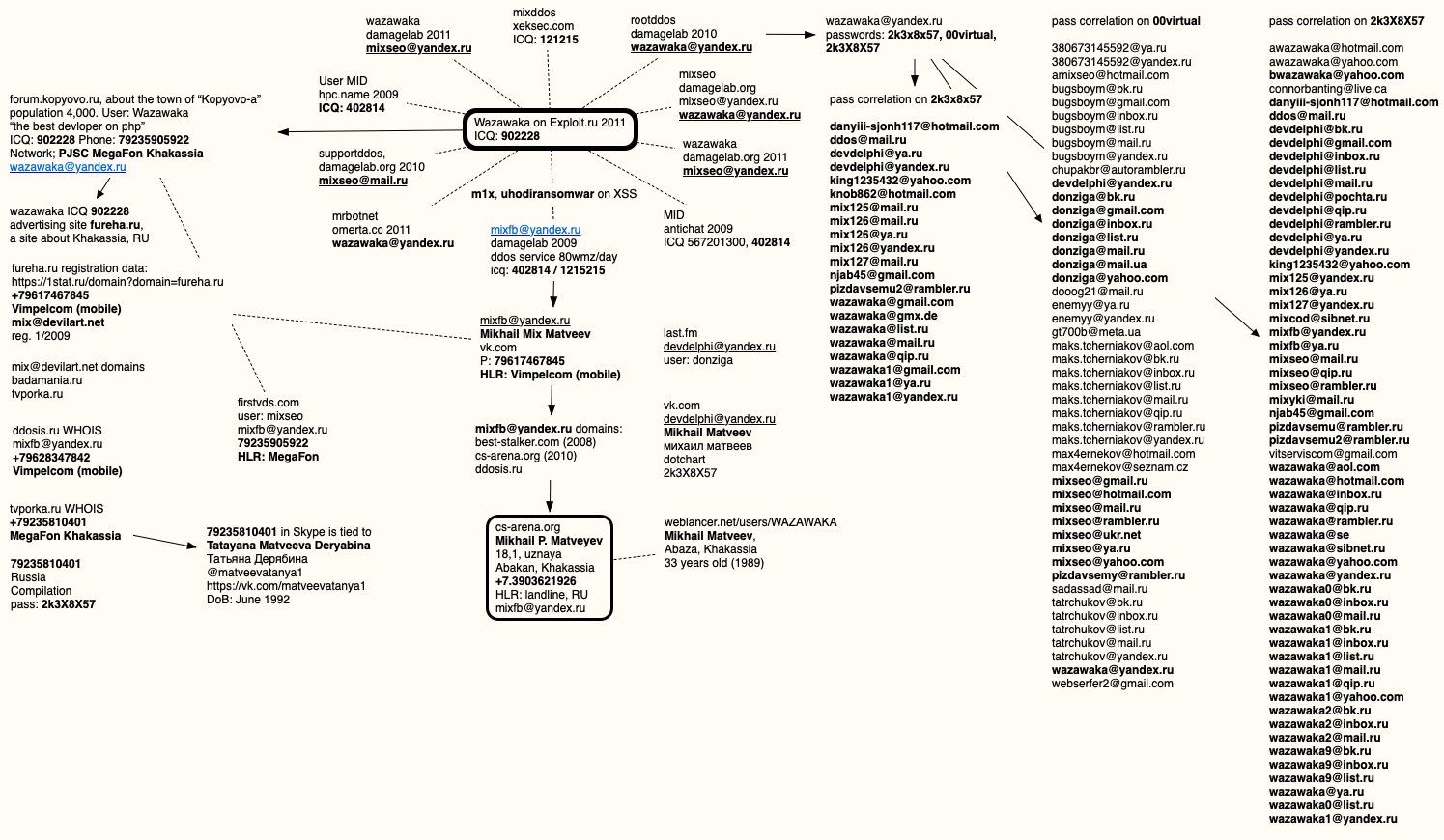
Wazawaka used multiple email addresses and nicknames on several Russian crime forums, but data collected by cybersecurity firm Constella Intelligence show that Wazawaka’s alter egos always used one of three fairly unique passwords: 2k3x8x57, 2k3X8X57, and 00virtual.
Those three passwords were used by one or all of Wazawaka’s email addresses on the crime forums over the years, including
That last email address was used almost a decade ago to register a Vkontakte (Russian version of Facebook) account under the name Mikhail “Mix” Matveev. The phone number tied to that Vkontakte account — 7617467845 — was assigned by the Russian telephony provider MegaFon to a resident in Khakassia, situated in the southwestern part of Eastern Siberia.
DomainTools.com [an advertiser on this site] reports
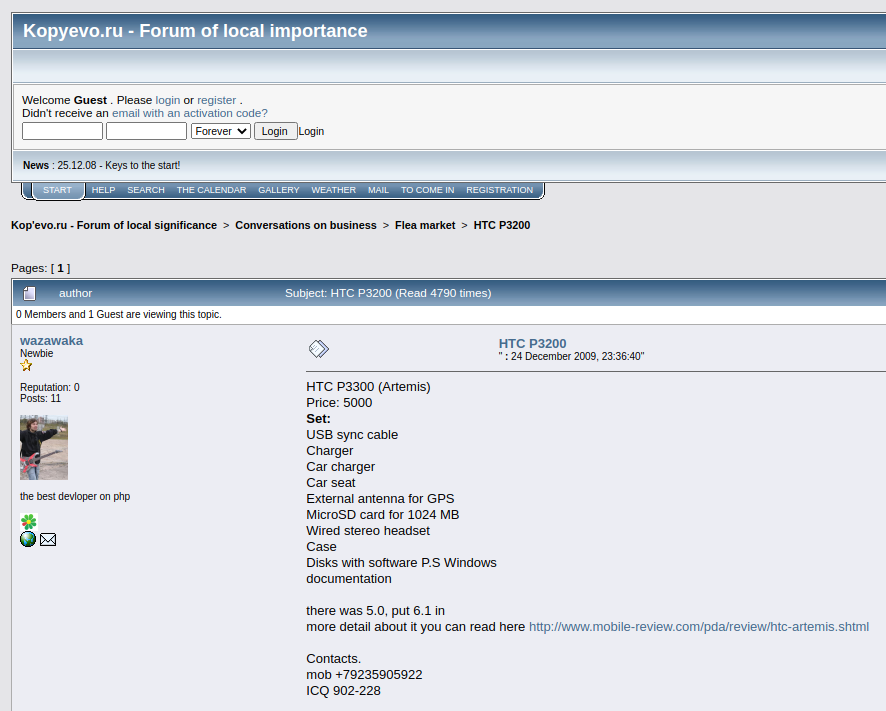
Mikhail Matveev is not the most unusual name in Russia, but other clues help narrow things down quite a bit. For example, early in his postings to Exploit, Wazawaka can be seen telling members that he can be contacted via the ICQ instant message account 902228.
An Internet search for Wazawaka’s ICQ number brings up a 2009 account for a Wazawaka on a now defunct discussion forum about Kopyovo-a, a town of roughly 4,400 souls in the Russian republic of Khakassia:
MIKHAIL’S MIX
Also around 2009, someone using the nickname Wazawaka and the 902228 ICQ address started posting to Russian social media networks trying to convince locals to frequent the website “fureha.ru,” which was billed as another website catering to residents of Khakassia.
According to the Russian domain watcher 1stat.ru, fureha.ru was registered in January 2009 to the email address
DomainTools.com says the
A search in Skype for that number shows that it was associated more than a decade ago with the username “matveevatanya1.” It was registered to a now 29-year-old Tatayana Matveeva Deryabina, whose Vkontakte profile says she currently resides in Krasnoyarsk, the largest city that is closest to Abakan and Abaza.
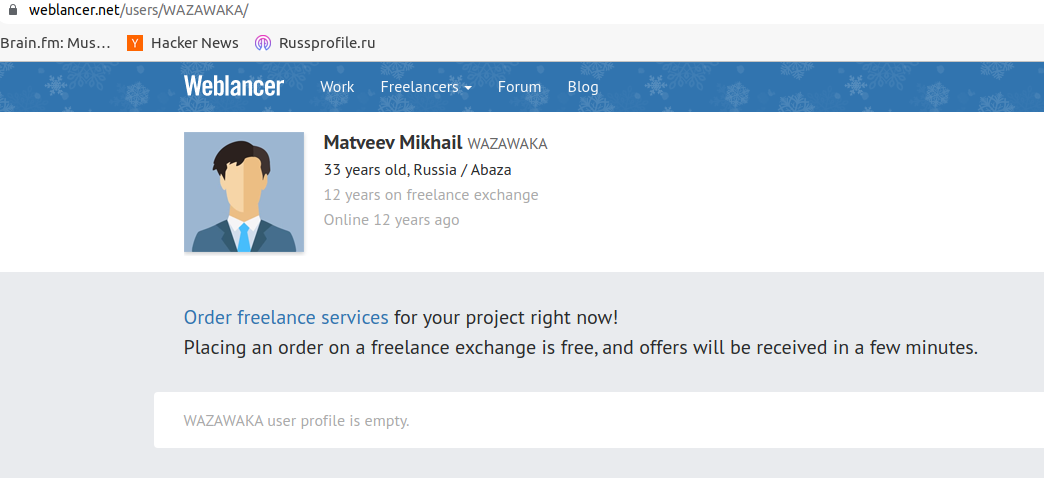
It seems likely that Tatayana is a relative of Mikhail Matveev, perhaps even his sister. Neither responded to requests for comment. In 2009, a Mikhail Matveev from Abaza, Khakassia registered the username Wazawaka on weblancer.net, a freelance job exchange for Russian IT professionals. The Weblancer account says Wazawaka is currently 33 years old.
In March 2019, Wazawaka explained a lengthy absence on Exploit by saying he’d fathered a child. “I will answer everyone in a week or two,” the crime actor wrote. “Became a dad — went on vacation for a couple of weeks.”
One of the many email addresses Wazawaka used was
Analysts with cyber intelligence firm Flashpoint say Wazawaka’s postings on various Russian crime forums show he is proficient in many specializations, including botnet operations, keylogger malware, spam botnets, credential harvesting, Google Analytics manipulation, selling databases for spam operations, and launching DDoS attacks.
Flashpoint says it is likely Wazawaka/Mix/M1x has shared cybercriminal identities and accounts with multiple other forum members, most of whom appear to have been partners in his DDoS-for-hire business a decade ago. For example, Flashpoint points to an Antichat forum thread from 2009 where members said M1x worked on his DDoS service with a hacker by the nickname “Vedd,” who was reputedly also a resident of Abakan.
STAY TRUE, & MOTHER RUSSIA WILL HELP YOU
All of this is academic, of course, provided Mr. Wazawaka chooses to a) never leave Russia and b) avoid cybercrime activities that target Russian citizens. In a January 2021 thread on Exploit regarding the arrest of an affiliate for the NetWalker ransomware program and its subsequent demise, Wazawaka seems already resigned those limitations.
“Don’t shit where you live, travel local, and don’t go abroad,” Wazawaka said of his own personal mantra.
Which might explain why Wazawaka is so lackadaisical about hiding and protecting his cybercriminal identities: Incredibly, Wazawaka’s alter ego on the forum XSS — Uhodiransomware — still uses the same password on the forum that he used for his Vkontakte account 10 years ago. Lucky for him, XSS also demands a one-time code from his mobile authentication app.
Wazawaka said NetWalker’s closure was the result of its administrator (a.k.a. “Bugatti”) getting greedy, and then he proceeds to preach about the need to periodically re-brand one’s cybercriminal identity.
“I’ve had some business with Bugatti,” Wazawaka said. “The guy got too rich and began recruiting Americans as affiliate partners. What happened now is the result. That’s okay, though. I wish Bugatti to do some rebranding and start from the beginning  As for the servers that were seized, they should’ve hosted their admin panels in Russia to avoid getting their servers seized by INTERPOL, the FBI, or whatever.”
As for the servers that were seized, they should’ve hosted their admin panels in Russia to avoid getting their servers seized by INTERPOL, the FBI, or whatever.”
“Mother Russia will help you,” Wazawaka concluded. “Love your country, and you will always get away with everything.”
If you liked this post, you may also enjoy Who Is the Network Access Broker “Babam”?
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.