At Request of U.S., Russia Rounds Up 14 REvil Ransomware Affiliates
The Russian government said today it arrested 14 people accused of working for “REvil,” a particularly aggressive ransomware group that has extorted hundreds of millions of dollars from victim organizations. The Russian Federal Security Service (FSB) said the actions were taken in response to a request from U.S. officials, but many experts believe the crackdown is part of an effort to reduce tensions over Russian President Vladimir Putin’s decision to station 100,000 troops along the nation’s border with Ukraine.

The FSB headquarters at Lubyanka Square, Moscow. Image: Wikipedia.
The FSB said it arrested 14 REvil ransomware members, and searched more than two dozen addresses in Moscow, St. Petersburg, Leningrad and Lipetsk. As part of the raids, the FSB seized more than $600,000 US dollars, 426 million rubles (~$USD 5.5 million), 500,000 euros, and 20 “premium cars” purchased with funds obtained from cybercrime.
“The search activities were based on the appeal of the US authorities, who reported on the leader of the criminal community and his involvement in encroaching on the information resources of foreign high-tech companies by introducing malicious software, encrypting information and extorting money for its decryption,” the FSB said. “Representatives of the US competent authorities have been informed about the results of the operation.”
The FSB did not release the names of any of the individuals arrested, although a report from the Russian news agency TASS mentions two defendants: Roman Gennadyevich Muromsky, and Andrey Sergeevich Bessonov. Russian media outlet RIA Novosti released video footage from some of the raids:
REvil is widely thought to be a reincarnation of GandCrab, a Russian-language ransomware affiliate program that bragged of stealing more than $2 billion when it closed up shop in the summer of 2019. For roughly the next two years, REvil’s “Happy Blog” would churn out press releases naming and shaming dozens of new victims each week. A February 2021 analysis from researchers at IBM found the REvil gang earned more than $120 million in 2020 alone.
But all that changed last summer, when REvil associates working with another ransomware group — DarkSide — attacked Colonial Pipeline, causing fuel shortages and price spikes across the United States. Just months later, a multi-country law enforcement operation allowed investigators to hack into the REvil gang’s operations and force the group offline.
In November 2021, Europol announced it arrested seven REvil affliates who collectively made more than $230 million worth of ransom demands since 2019. At the same time, U.S. authorities unsealed two indictments against a pair of accused REvil cybercriminals, which referred to the men as “REvil Affiliate #22” and “REvil Affiliate #23.”
It is clear that U.S. authorities have known for some time the real names of REvil’s top captains and moneymakers. Last fall, President Biden told Putin that he expects Russia to act when the United States shares information on specific Russians involved in ransomware activity.
So why now? Russia has amassed approximately 100,000 troops along its southern border with Ukraine, and diplomatic efforts to defuse the situation have reportedly broken down. The Washington Post and other media outlets today report that the Biden administration has accused Moscow of sending saboteurs into Eastern Ukraine to stage an incident that could give Putin a pretext for ordering an invasion.
“The most interesting thing about these arrests is the timing,” said Kevin Breen, director of threat research at Immersive Labs. “For years, Russian Government policy on cybercriminals has been less than proactive to say the least. With Russia and the US currently at the diplomatic table, these arrests are likely part of a far wider, multi-layered, political negotiation.”
President Biden has warned that Russia can expect severe sanctions should it choose to invade Ukraine. But Putin in turn has said such sanctions could cause a complete break in diplomatic relations between the two countries.
Dmitri Alperovitch, co-founder of and former chief technology officer for the security firm CrowdStrike, called the REvil arrests in Russia “ransomware diplomacy.”
“This is Russian ransomware diplomacy,” Alperovitch said on Twitter. “It is a signal to the United States — if you don’t enact severe sanctions against us for invasion of Ukraine, we will continue to cooperate with you on ransomware investigations.”
The REvil arrests were announced as many government websites in Ukraine were defaced by hackers with an ominous message warning Ukrainians that their personal data was being uploaded to the Internet. “Be afraid and expect the worst,” the message warned.
Experts say there is good reason for Ukraine to be afraid. Ukraine has long been used as the testing grounds for Russian offensive hacking capabilities. State-backed Russian hackers have been blamed for the Dec. 23, 2015 cyberattack on Ukraine’s power grid that left 230,000 customers shivering in the dark.
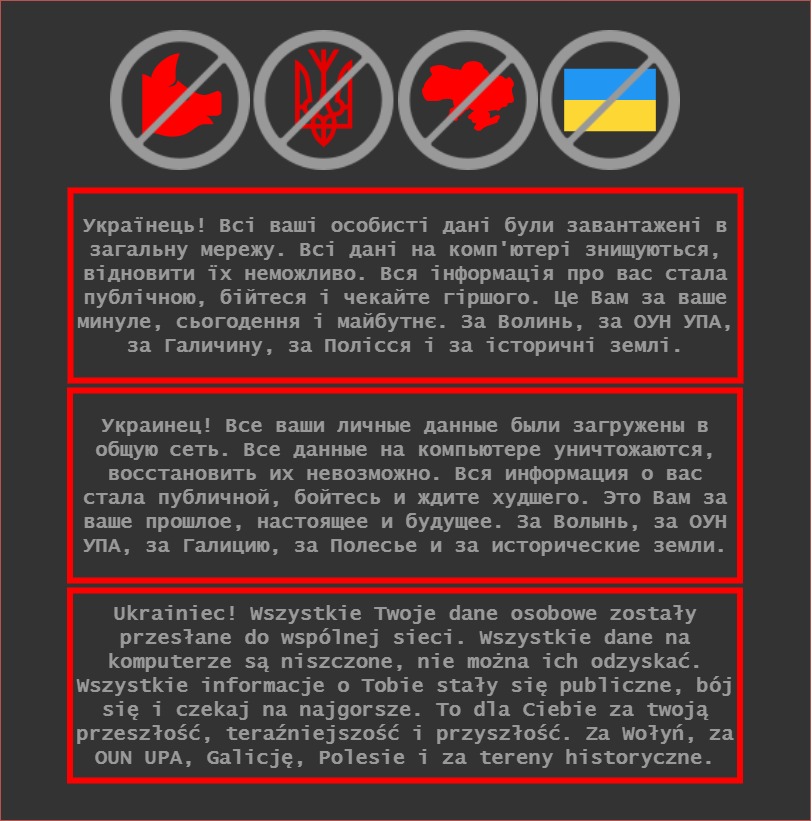
The warning left behind on Ukrainian government websites that were defaced in the last 24 hours. The same statement is written in Ukrainian, Russian and Polish.
Russia also has been suspected of releasing NotPetya, a large-scale cyberattack initially aimed at Ukrainian businesses that ended up creating an extremely disruptive and expensive global malware outbreak.
Although there has been no clear attribution of these latest attacks to Russia, there is reason to suspect Russia’s hand, said David Salvo, deputy director of The Alliance for Securing Democracy.
“These are tried and true Russian tactics. Russia used cyber operations and information operations in the run-up to its invasion of Georgia in 2008. It has long waged massive cyberattacks against Ukrainian infrastructure, as well as information operations targeting Ukrainian soldiers and Ukrainian citizens. And it is completely unsurprising that it would use these tactics now when it is clear Moscow is looking for any pretext to invade Ukraine again and cast blame on the West in its typical cynical fashion.”
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






