Rise of Darknet Stokes Fear of The Insider
With the proliferation of shadowy black markets on the so-called “darknet” — hidden crime bazaars that can only be accessed through special software that obscures one’s true location online — it has never been easier for disgruntled employees to harm their current or former employer. At least, this is the fear driving a growing stable of companies seeking technical solutions to detect would-be insiders.
Avivah Litan, a fraud analyst with Gartner Inc., says she’s been inundated recently with calls from organizations asking what they can do to counter the following scenario: A disaffected or disgruntled employee creates a persona on a darknet market and offers to sell his company’s intellectual property or access to his employer’s network.
Litan said a year ago she might have received one such inquiry a month; now Litan says she’s getting multiple calls a week, often from companies that are in a panic.
“I’m getting calls from lots of big companies, including manufacturers, banks, pharmaceutical firms and retailers,” she said. “A year ago, no one wanted to say whether they had or were seriously worried about insiders, but that’s changing.”
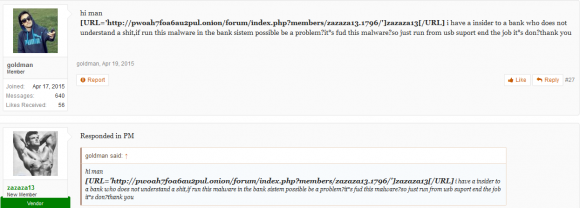
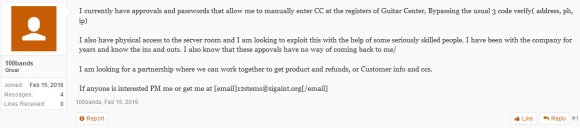
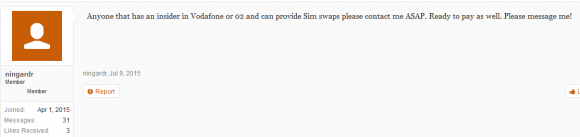
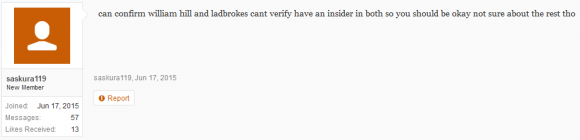
Insiders don’t have to be smart or sophisticated to be dangerous, as this darknet forum discussion thread illustrates.
Some companies with tremendous investments in intellectual property — particularly pharmaceutical and healthcare firms — are working with law enforcement or paying security firms to monitor and track actors on the darknet that promise access to specific data or organizations, Litan said.
“One pharma guy I talked to recently said he meets with [federal agents] once a week to see if his employees are active on the darknet,” she said. “Turns out there are a lot of disgruntled employees who want to harm their employers. Before, it wasn’t always clear how to go about doing that, but now they just need to create a free account on some darknet site.”
Statistics and figures only go so far in illustrating the size of the problem. A Sept. 2015 report from Intel found that internal actors were responsible for 43 percent of data loss — but only about half of that was intended to harm the employer.
Likewise, the 2016 Data Breach Investigation Report (DBIR), an annual survey of data breaches from Verizon Enterprise, found insiders and/or the misuse of employee privileges were present in a majority of incident. Yet it also concluded that much of this was not malicious but instead appeared related to employees mailing sensitive information or loading it to a file-sharing service online.
Perhaps one reason insiders are so feared is that the malicious ones very often can operate for years undetected, doing major damage to employers in the process. Indeed, Verizon’s DBIR found that insider breaches usually takes months or years to discover.
Noam Jolles, a senior intelligence expert at Diskin Advanced Technologies, studies darknet communities. I interviewed her last year in “Bidding for Breaches,” a story about a secretive darknet forum called Enigma where members could be hired to launch targeted phishing attacks at companies. Some Enigma members routinely solicited bids regarding names of people at targeted corporations that could serve as insiders, as well as lists of people who might be susceptible to being recruited or extorted.
Jolles said the proliferation of darkweb communities has lowered the barriers to entry for insiders, and provided even the least sophisticated would-be insiders with ample opportunities to betray their employer’s trust.
“I’m not sure everyone is aware of how simple and practical this phenomena looks from adversary eyes and how far it is from the notion of an insider as a sophisticated disgruntled employee,” Jolles said. “The damage from the insider is not necessarily due to his position, but rather to the sophistication of the threat actors that put their hands on him.”
Who is the typical insider? According to Verizon’s DBIR, almost one third of insiders at breaches in 2015 were found to be end users who had access to sensitive data as a requirement to do their jobs.
“Only a small percentage (14%) are in leadership roles (executive or other management), or in roles with elevated access privilege jobs such as system administrators or developers (14%),” Verizon wrote, noting that insiders were most commonly found in administrative, healthcare and public sector jobs. “The moral of this story is to worry less about job titles and more about the level of access that every Joe or Jane has (and your ability to monitor them). At the end of the day, keep up a healthy level of suspicion toward all employees.”
If tech industry analysts like Litan are getting pinged left and right about the insider threat these days, it might have something to do with how easy it is to find company proprietary information or access on offer in darknet forums — many of which allow virtually anyone to register and join.
The other reason may be that there are a lot more companies looking for this information and actively notifying affected organizations. These notifications invariably become sales pitches for “dark web monitoring” or “threat intelligence services,” and a lot of companies probably aren’t sure what to make of this still-nascent industry.
How can organizations better detect insiders before the damage is done? Gartner’s Litan emphasized continuous monitoring and screening for trusted insiders with high privileges. Beyond that, Litan says there are a wide range of data-driven insider threat technology solutions. On the one end of the spectrum are companies that conduct targeted keyword searches on behalf of clients on social media networks and darknet destinations. More serious and expensive offerings apply machine learning to internal human resources (HR) records, and work to discover and infiltrate online crime rings.
What’s Verizon’s answer to the insider threat? “Love your employees, bond at the company retreat, bring in bagels on Friday, but monitor the heck out of their authorized daily activity, especially ones with access to monetizable data (financial account information, personally identifiable information (PII), payment cards, medical records).”
Additional reading: Insider Threats Escalate and Thrive in the Dark Web.
Tags: avivah litan, darknet, darkweb, Data Breach Investigations Report, Diskin Advanced Technologies, gartner, insider threat, Noam Jolles, Verizon
This entry was posted on Wednesday, June 22nd, 2016 at 4:49 pm and is filed under A Little Sunshine, The Coming Storm. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.