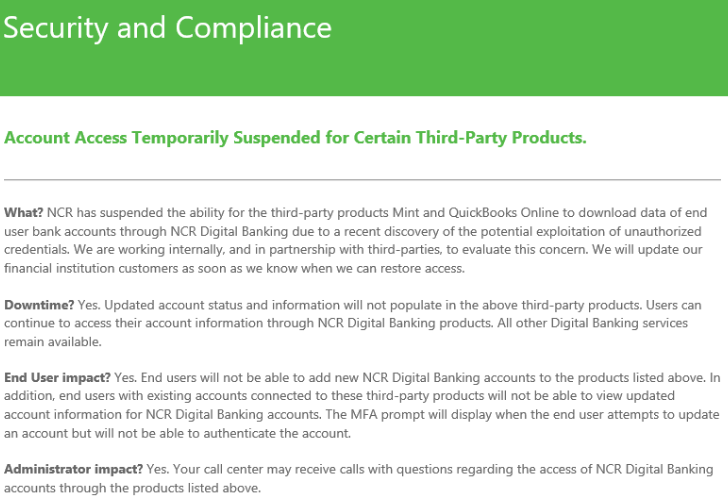
NCR Barred Mint, QuickBooks from Banking Platform During Account Takeover Storm
Banking industry giant NCR Corp. [NYSE: NCR] late last month took the unusual step of temporarily blocking third-party financial data aggregators Mint and QuicBooks Online from accessing Digital Insight, an online banking platform used by hundreds of financial institutions. That ban, which came in response to a series of bank account takeovers in which cybercriminals used aggregation sites to surveil and drain consumer accounts, has since been rescinded. But the incident raises fresh questions about the proper role of digital banking platforms in fighting password abuse.
On Oct. 29, KrebsOnSecurity heard from a chief security officer at a U.S.-based credit union and Digital Insight customer who said his institution just had several dozen customer accounts hacked over the previous week. The source, who asked to remain anonymous, said the unauthorized activity came from accounts at both Mint and QuickBooks — services that let consumers aggregate account and transaction data from multiple financial institutions.
My banking source said the attackers appeared to automate the unauthorized logins, which took place over a week in several distinct 12-hour periods in which a new account was accessed every five to ten minutes.
Most concerning, the source said, was that in many cases the aggregator service did not pass through prompts sent by the credit union’s site for multi-factor authentication, meaning the attackers could access customer accounts with nothing more than a username and password.
“The weird part is sometimes the attackers are getting the multi-factor challenge, and sometimes they aren’t,” said the source, who added that he suspected a breach at Mint and/QuickBooks because NCR had just blocked the two companies from accessing bank Web sites on its platform.
In a statement provided to KrebsOnSecurity, NCR said that on Friday, Oct. 25, NCR notified Digital Insight customers “that the aggregation capabilities of certain third-party product were being temporarily suspended.”
“The notification was sent while we investigated a report involving a single user and a third-party product that aggregates bank data,” reads their statement, which was sent to customers on Oct. 29. After confirming that the incident was contained, NCR restored connectivity that is used for account aggregation. As criminals deploy more sophisticated methods and tools to access online information, NCR continues to evaluate and proactively defend against these activities.”
What were these sophisticated methods? NCR wouldn’t say, but it seems clear the hacked accounts are tied to customers re-using their online banking passwords at other sites that got hacked.
As I noted earlier this year in The Risk of Weak Online Banking Passwords, if you bank online and choose weak or re-used passwords, there’s a decent chance your account could be pilfered by cyberthieves — even if your bank offers multi-factor authentication as part of its login process.
Crooks are constantly probing bank Web sites for customer accounts protected by weak or recycled passwords. Most often, the attacker will use lists of email addresses and passwords stolen en masse from hacked sites and then try those same credentials to see if they permit online access to accounts at a range of banks.
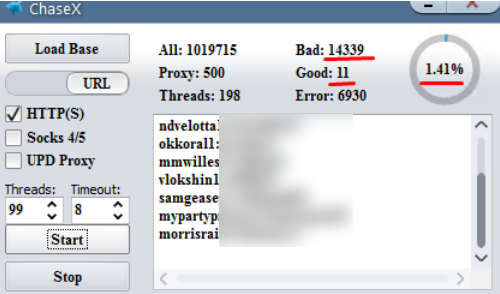
A screenshot of a password-checking tool that can be used to target Chase Bank customers who re-use passwords. There are tools like this one for just about every other major U.S. bank.
From there, thieves can take the list of successful logins and feed them into apps that rely on application programming interfaces (API)s from one of several personal financial data aggregators, including Mint, Plaid, QuickBooks, Plaid, Yodlee, and YNAB.
A number of banks that do offer customers multi-factor authentication — such as a one-time code sent via text message or an app — have chosen to allow these aggregators the ability to view balances and recent transactions without requiring that the aggregator service supply that second factor.
If the thieves are able to access a bank account via an aggregator service or API, they can view the customer’s balance(s) and decide which customers are worthy of further targeting.
But beyond targeting customers for outright account takeovers, the data available via financial aggregators enables a far more insidious type of fraud: The ability to link the target’s bank account(s) to other accounts that the attackers control.
That’s because PayPal, Zelle, and a number of other pure-play online financial institutions allow customers to link accounts by verifying the value of microdeposits. For example, if you wish to be able to transfer funds between PayPal and a bank account, the company will first send a couple of tiny deposits — a few cents, usually — to the account you wish to link. Only after verifying those exact amounts will the account-linking request be granted.
The temporary blocking of data aggregators by NCR brings up a point worthy of discussion by regulators: Namely, in the absence of additional security measures put in place by the aggregators, do the digital banking platform providers like NCR, Fiserv, Jack Henry, and FIS have an obligation to help block or mitigate these large-scale credential exploitation attacks?
KrebsOnSecurity would argue they do, and that the crooks who attacked the customers of my source’s credit union have probably already moved on to using the same attack against one of several thousand other dinky banks across the country.
Intuit Inc., which owns both Mint and QuickBooks, has not responded to requests for comment.
NCR declined to discuss specifics about how it plans to respond to similar attacks going forward.
“NCR does not make public comment on methods and tactics of malicious actors,” the company’s statement read. “As we noted, the criminals are getting aggressive and creative in accessing tools to access online information, NCR continues to evaluate and proactively defend against these activities.”
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.