Dual-Use Software Criminal Case Not So Novel
“He built a piece of software. That tool was pirated and abused by hackers. Now the feds want him to pay for the computer crooks’ crimes.”
The above snippet is the subhead of a story published last month by the The Daily Beast titled, “FBI Arrests Hacker Who Hacked No One.” The subject of that piece — a 26-year-old American named Taylor Huddleston — faces felony hacking charges connected to two computer programs he authored and sold: An anti-piracy product called Net Seal, and a Remote Administration Tool (RAT) called NanoCore that he says was a benign program designed to help users remotely administer their computers.

Photo illustration by Lyne Lucien/The Daily Beast
The author of the Daily Beast story, former black hat hacker and Wired.com editor Kevin Poulsen, argues that Huddleston’s case raises a novel question: When is a programmer criminally responsible for the actions of his users?
“Some experts say [the case] could have far reaching implications for developers, particularly those working on new technologies that criminals might adopt in unforeseeable ways,” Poulsen wrote.
But a closer look at the government’s side of the story — as well as public postings left behind by the accused and his alleged accomplices — paints a more complex and nuanced picture that suggests this may not be the case to raise that specific legal question in any meaningful way.
Mark Rumold, senior staff attorney at the Electronic Frontier Foundation (EFF), said cases like these are not so cut-and-dry because they hinge on intent, and determining who knew what and when.
“I don’t read the government’s complaint as making the case that selling some type of RAT is illegal, and if that were the case I think we would be very interested in this,” Rumold said. “Whether or not [the government’s] claims are valid is going to be extraordinarily fact-specific, but unfortunately there is not a precise set of facts that would push this case from being about the valid reselling of a tool that no one questions can be done legally to crossing that threshold of engaging in a criminal conspiracy.”
Citing group chat logs and other evidence that hasn’t yet been made public, U.S. prosecutors say Huddleston intended NanoCore to function more like a Remote Access Trojan used to remotely control compromised PCs, and they’ve indicted Huddleston on criminal charges of conspiracy as well as aiding and abetting computer intrusions.
Poulsen depicts Huddleston as an ambitious — if extremely naive — programmer struggling to make an honest living selling what is essentially a dual-use software product. Using the nickname “Aeonhack,” Huddleston marketed his NanoCore RAT on Hackforums[dot]net, an English-language hacking forum that is overrun with young, impressionable but otherwise low-skilled hackers who are constantly looking for point-and-click tools and services that can help them demonstrate their supposed hacking prowess.
Yet we’re told that Huddleston was positively shocked to discover that many buyers on the forum were using his tools in a less-than-legal manner, and that in response he chastised and even penalized customers who did so. By way of example, Poulsen writes that Huddleston routinely used his Net Seal program to revoke the software licenses for customers who boasted online about using his NanoCore RAT illegally.
We later learn that — despite Net Seal’s copy protection abilities — denizens of Hackforums were able to pirate copies of NanoCore and spread it far and wide in malware and phishing campaigns. Eventually, Huddleston said he grew weary of all the drama and sold both programs to another Hackforums member, using the $60,000 or so in proceeds to move out of the rusty trailer he and his girlfriend shared and buy a house in a low-income corner of Hot Springs, Arkansas.
From the story:
“Now even Huddleston’s modest home is in jeopardy,” Poulsen writes. “As part of their case, prosecutors are seeking forfeiture of any property derived from the proceeds of NanoCore, as well as from Huddleston’s anti piracy system, which is also featured in the indictment. ‘Net Seal licensing software is licensing software for cybercriminals,’ the indictment declares.
“For this surprising charge—remember, Huddleston use the licenses to fight crooks and pirates—the government leans on the conviction of a Virginia college student named Zachary Shames, who pleaded guilty in January to selling hackers a keystroke logging program called Limitless. Unlike Huddleston, Shames embraced malicious use of his code. And he used Net Seal to protect and distribute it.
“Huddleston admits an acquaintanceship with Shames, who was known on HackForums as ‘Mephobia,’ but bristles at the accusation that Net Seal was built for crime. ‘Net Seal is literally the exact opposite of aiding and abetting’ criminals, he says. ‘It logs their IP addresses, it block their access to the software, it stops them from sharing it with other cyber criminals. I mean, every aspect of it fundamentally prevents cybercrime. For them to say that [crime] is its intention is just ridiculous.’”
Poulsen does note that Shames pleaded guilty in January to selling his Limitless keystroke logging program, which relied on Huddleston’s Net Seal program for distribution and copy protection.
Otherwise, The Daily Beast story seems to breeze over relationship between Huddleston and Shames as almost incidental. But according to the government it is at the crux of the case, and a review of the indictment against Huddleston suggests the two’s fortunes were intimately intertwined.
From the government’s indictment:
“During the course of the conspiracy, Huddleston received over 25,000 payments via PayPal from Net Seal customers. As part of the conspiracy, Huddleston provided Shames with access to his Net Seal licensing software in order to assist Shames in the distribution of his Limitless keylogger. In exchange, Shames made at least one thousand payments via PayPal to Huddleston.”
“As part of the conspiracy, Huddleston and Shames distributed the Limitless keylogger to over 3,000 people who used it to access over 16,000 computers without authorization with the goal and frequently with the result of stealing sensitive information from those computers. As part of the conspiracy, Huddleston provided Net Seal to several other co-conspirators to assist in the profitable distribution of the malicious software they developed, including prolific malware that has repeatedly been used to conduct unlawful and unauthorized computer intrusions.”
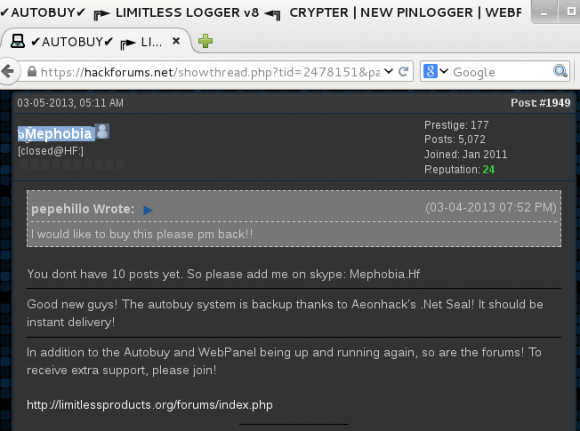
A screen shot of Zach “Mephobia” Shames on Hackforums discussing the relationship between his Limitless keylogger and Huddleston’s (Aeonhack) Net Seal anti-piracy and payment platform.
Allison Nixon, director of security research for New York City-based security firm Flashpoint, observed that in the context of Hackforums, payment processing through Paypal is a significant problem for forum members trying to sell dual-use software and services on the forum.
“Most of their potential customer base uses PayPal, but their vendor accounts keep getting suspended for being associated with crime, so people who can successfully get payments through are prized,” Nixon said. “Net Seal can revoke access to a program that uses it, but it is a payment processing and digital rights management (DRM) system. Huddleston can claim the DRM is to prevent cybercrime, but realistically speaking the DRM is part of the payment system — to prevent people from pirating the software or initiating a Paypal chargeback. Just because he says that he blocked someone’s license due to an admission of crime does not mean that was the original purpose of the software.”
Nixon, a researcher who has spent countless hours profiling hackers and activities on Hackforums, said selling the NanoCore RAT on Hackforums and simultaneously scolding people for using it to illegally spy on people “could at best be seen as the actions of the most naive software developer on the Earth.”
“In the greater context of his role as the money man for Limitless Keylogger, it does raise questions about how sincere his anti-cybercrime stance really is,” Nixon said. “Considering that he bought a house from this, he has a significant financial incentive to play ignorant while simultaneously operating a business that can’t make nearly as much money if it was operated on a forum that wasn’t infested with criminals.”
Huddleston makes the case in Poulsen’s story that there’s a corporate-friendly double standard at work in the government’s charges, noting that malicious hackers have used commercial remote administration tools like TeamViewer and VNC for years, but the FBI doesn’t show up at their corporate headquarters with guns drawn.
But Nixon notes that RATs sold on Hackforums are extremely dangerous for the average person to use on his personal computer because there are past cases when RAT authors divert infected machines to their own botnet.
Case in point: The author of the Blackshades Trojan — once a wildly popular RAT sold principally on Hackforums before its author and hundreds of its paying customers were arrested in a global law enforcement sweep — wasn’t content to simply rake in money from the sale of each Blackshades license: He also included a backdoor that let him secretly commandeer machines running the software.
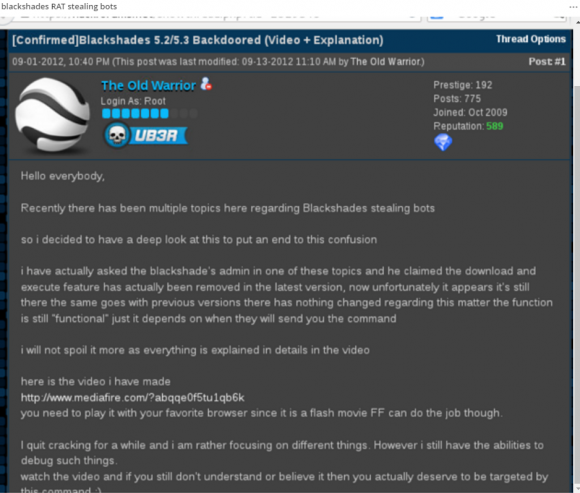
A Hackforums user details how the Blackshades RAT included a backdoor that let the RAT’s original author secretly access systems infected with the RAT.
“If a person is using RAT software on their personal machine that they purchased from Hackforums, they are taking this risk,” Nixon said. “Programs like VNC and Teamviewer are much safer for legitimate use, because they are actual companies, not programs produced by teenagers in a criminogenic environment.”
All of this may be moot if the government can’t win its case against Huddleston. The EFF’s Rumold said while prosecutors may have leverage in Shames’s conviction, the government probably doesn’t want to take the case to trial.
“My guess is if they want a conviction, they’re going to have to go to trial or offer him some type of very favorable plea,” Rumold said. “Just the fact that Huddleston was able to tell his story in a way that makes him come off as a very sympathetic character sounds like the government may have a difficult time prosecuting him.”
A copy of the indictment against Huddleston is available here (PDF).
If you enjoyed this story, take a look at a related piece published here last year about a different RAT proprietor selling his product on Hackforums who similarly claimed the software was just a security tool designed for system administrators, despite features of the program and related services that strongly suggested otherwise.
Tags: Aeonhack, Allison Nixon, Blackshades RAT, Blackshades trojan, Electronic Frontier Foundation, fbi, Flashpoint, Hackforums, justice department, Kevin Poulsen, Limitless Keylogger, Mark Rumold, Mephobia, NanoCore, Net Seal, RAT, remote access trojan, remote administration tool, Taylor Huddleston, TeamViewer and VNC, The Daily Beast, wired, Zachary Shames
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






