Dell Lost Control of Key Customer Support Domain for a Month in 2017
A Web site set up by PC maker Dell Inc. to help customers recover from malicious software and other computer maladies may have been hijacked for a few weeks this summer by people who specialize in deploying said malware, KrebsOnSecurity has learned.
There is a program installed on virtually all Dell computers called “Dell Backup and Recovery Application.” It’s designed to help customers restore their data and computers to their pristine, factory default state should a problem occur with the device. That backup and recovery program periodically checks a rather catchy domain name — DellBackupandRecoveryCloudStorage.com — which until recently was central to PC maker Dell’s customer data backup, recovery and cloud storage solutions.
Sometime this summer, DellBackupandRecoveryCloudStorage.com was suddenly snatched away from a longtime Dell contractor for a month and exposed to some questionable content. More worryingly, there are signs the domain may have been pushing malware before Dell’s contractor regained control over it.

Image: Wikipedia
The purpose of DellBackupandRecoveryCloudStorage.com is inscribed in the hearts of countless PCs that Dell shipped customers over the past few years. The domain periodically gets checked by the “Dell Backup and Recovery application,” which “enables the user to backup and restore their data with just a few clicks.”
This program comes in two versions: Basic and Premium, explains “Jesse L,” a Dell customer liaison and a blogger on the company’s site.
“The Basic version comes pre-installed on all systems and allows the user to create the system recovery media and take a backup of the factory installed applications and drivers,”Jesse L writes. “It also helps the user to restore the computer to the factory image in case of an OS issue.”
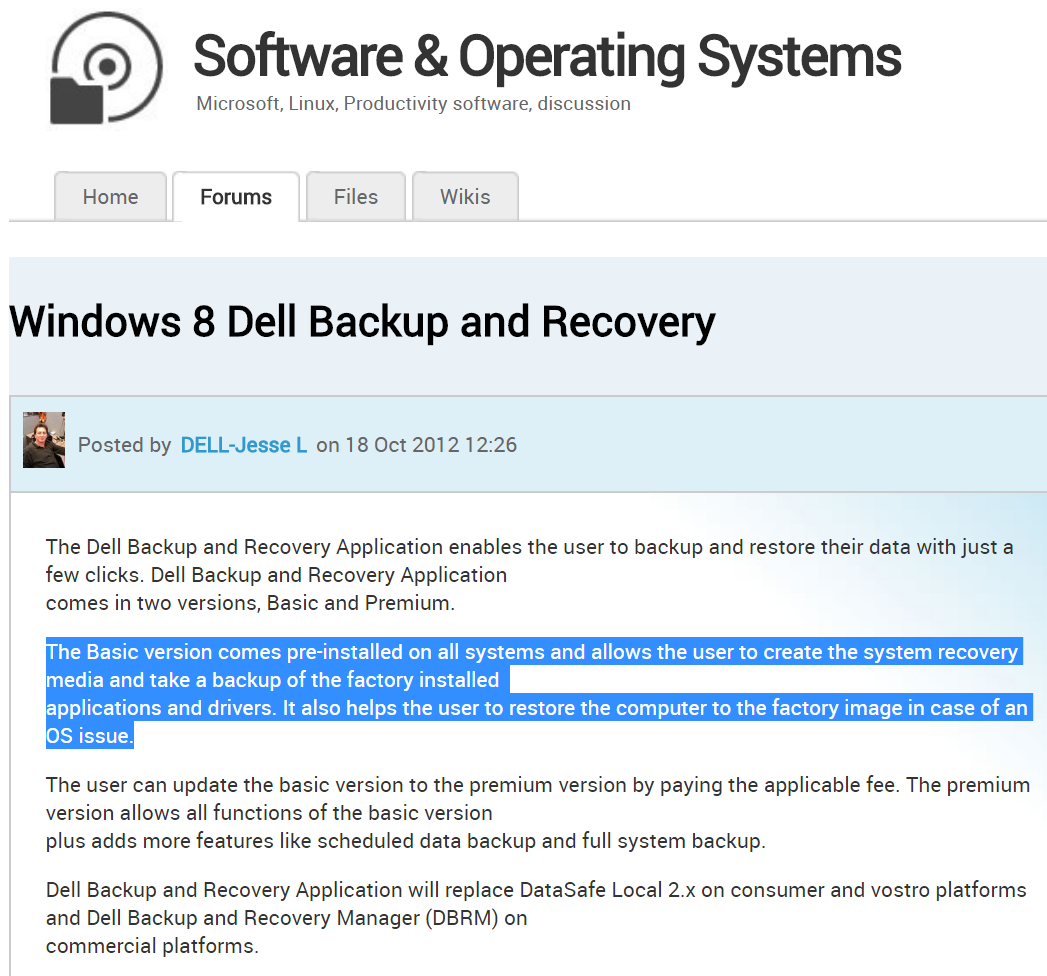
Dell customer liaison Jesse L. talks about how the program in question is by default installed on all Dell PCs.
In other words: If DellBackupandRecoveryCloudStorage.com were to fall into the wrong hands it could be used to foist malicious software on Dell users seeking solace and refuge from just such nonsense!
It’s not yet clear how or why DellBackupandRecoveryCloudStorage.com got away from SoftThinks.com — an Austin, Tex.-based software backup and imaging solutions provider that originally registered the domain back in mid-2013 and has controlled it for most of the time since. But someone at SoftThinks apparently forgot to renew the domain in mid-June 2017.
SoftThinks lists Dell among some of its “great partners” (see screenshot below). It hasn’t responded to requests for comment. Some of its other partners include Best Buy and Radio Shack.

Some of SoftThinks’ partners. Source: SoftThinks.com
From early June to early July 2017, DellBackupandRecoveryCloudStorage.com was the property of Dmitrii Vassilev of “TeamInternet.com,” a company listed in Germany that specializes in selling what appears to be typosquatting traffic. Team Internet also appears to be tied to a domain monetization business called ParkingCrew.
If you’re not sure what typosquatting is, think of what sometimes happens when you’re typing out a URL in the browser’s address field and you fat-finger a single character and suddenly get redirected to the kind of content that makes you look around quickly to see if anyone saw you looking at it. For more on Team Internet, see this enlightening Aug. 2017 post from Chris Baker at internet infrastructure firm Dyn.
It could be that Team Internet did nothing untoward with the domain name, and that it just resold it or leased it to someone who did. But approximately two weeks after Dell’s contractor lost control over the domain, the server it was hosted on started showing up in malware alerts.
That’s according to Celedonio Albarran, assistant vice president of IT infrastructure and security at Equity Residential, a real estate investment trust that invests in apartments.
Albarran said Equity is responsible for thousands of computers, and that several of those machines in late June tried to reach out to DellBackupandRecoveryCloudStorage.com but were prevented from doing so because the Internet address tied to the domain was new and because that address had been flagged by two security firms as pushing malicious software.
On that particular day, anyone visiting DellBackupandRecoveryCloudStorage.com simultaneously would have been heading to the Internet address 54-72-9-51 (I’ve replaced the dots with dashes for safety reasons). Albarran said the first alert came on June 28 from a security tool from Rapid7 that flagged a malware detection on that Internet address.
Another anti-malware product Equity Residential uses is Carbon Black, which on June 28 detected a reason why a Dell computer within the company shouldn’t be able to visit dellbackupandrecoverycloudstorage.com. According to Albarran, that second alert was generated by Abuse.ch, a Swiss infrastructure security company and active anti-abuse advocate.
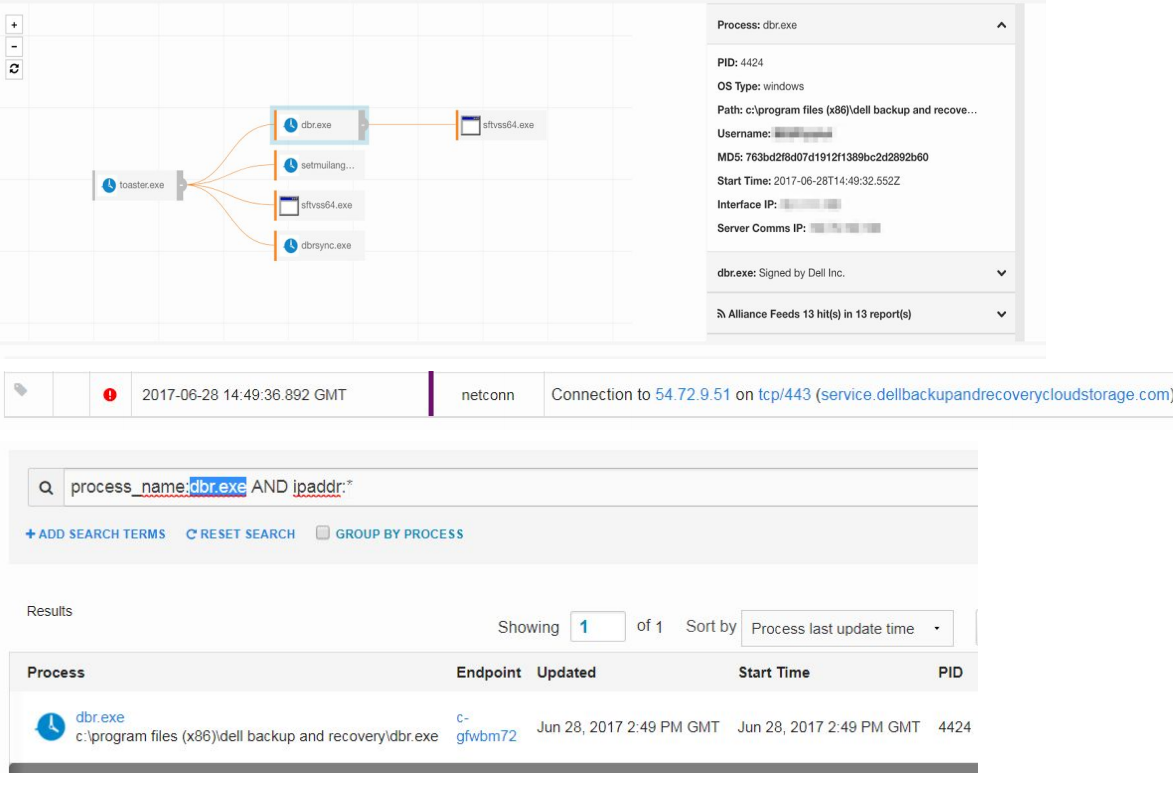
This Carbon Black log shows dellbackupandrecoverycloudstorage.com reaching out to a nasty Internet address on June 28, 2017.
The domain’s host appears to have been flagged by Abuse.ch’s Ransomware Tracker, which is a running list of Internet addresses and domains that have a history of foisting ransomware — a threat that encrypts your files with tough-to-crack encryption, and then makes you pay for a key to unlock the files.
Albarran told KrebsOnSecurity that his company was never able to find any evidence that computers on its networks that were beaconing home to DellBackupandRecoveryCloudStorage.com had any malware installed as a result of the traffic. But he said his systems were blocked from visiting the domains on June 28, 2017, and that his employer immediately notified Dell of the problem.
“A few weeks after that they confirmed they fixed the issue,” Albarran said. “They just acknowledged the issue and said it was fixed, but they didn’t offer any comment besides that.”
AlienVault‘s Open Threat Exchange says the Internet address that was assigned to DellBackupandRecoveryCloudStorage.com in late June is an Amazon server which is “actively malicious” (even today), categorizing it as an address known for spamming.
Reached for comment about the domain snafu, Dell spokesperson Ellen Murphy shared the following statement:
“A domain as part of the cloud backup feature for the Dell Backup and Recovery (DBAR) application, www.dellbackupandrecoverycloudstorage.com, expired on June 1, 2017 and was subsequently purchased by a third party. The domain reference in the DBAR application was not updated, so DBAR continued to reach out to the domain after it expired. Dell was alerted of this error and it was addressed. Dell discontinued the Dell Backup and Recovery application in 2016.”
I have asked Dell for more information about this incident, such as whether the company knows if any customers were harmed as a result of this rather serious oversight. I’ll update this story in the event that I hear back from Dell.
This is not the first time the failure to register a domain name caused a security concern for a company that should be very concerned about security. Earlier this month, experts noticed that the Web sites for credit bureaus Trans Union and Equifax were both redirecting browsers to popup ads that tried to disguise adware and spyware as an update for Adobe Flash Player.
The spyware episodes at Equifax’s and Trans Union’s Web sites were made possible because both companies outsourced e-commerce and digital marketing to Fireclick, a now-defunct digital marketing product run by Digital River. Fireclick in turn invoked a domain called Netflame.cc. But according to an Oct. 13 story in The Wall Street Journal, Netflame’s registration “was released in October 2016, three months after Digital River ended support for Fireclick as part of an ‘ongoing domain cleanup.'”
The problem with the Dell customer support domain name comes as Dell customers continue to complain of being called by scammers pretending to be Dell tech support specialists. In many cases, the callers will try to make their scams sound more convincing by reading off the unique Dell “service tag” code printed on each Dell customer’s PC or laptop.
How can scammers have all this data if Dell’s service and support system isn’t compromised, many Dell customers have asked? And still ask: I’ve had three readers quiz me about these Dell service tag scams in the past week alone. Dell continues to be silent on what may be going on with the service tag scams, and has urged Dell customers targeted by such scams to report them to the company.
Tags: Abuse.ch, Carbon Black, Celedonio Albarran, Chris Baker, Dell, Dell Backup and Recovery Application, dell service tag scams, Dellbackupandrecoverycloudstorage.com, digital river, Dmitrii Vassilev, Dyn, Ellen Murphy, Equifax, Equity Residential, Fireclick, parkingcrew, Rapid7, SoftThinks.com, Team Internet, Trans Union
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






