Cybercrime Overtakes Traditional Crime in UK
In a notable sign of the times, cybercrime has now surpassed all other forms of crime in the United Kingdom, the nation’s National Crime Agency (NCA) warned in a new report. It remains unclear how closely the rest of the world tracks the U.K.’s experience, but the report reminds readers that the problem is likely far worse than the numbers suggest, noting that cybercrime is vastly under-reported by victims.
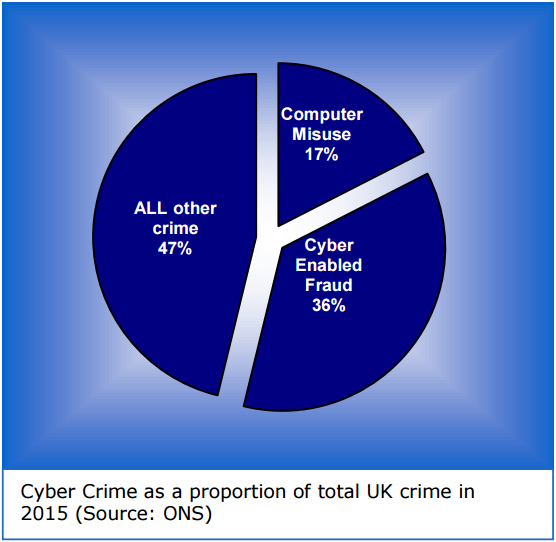 The NCA’s Cyber Crime Assessment 2016, released July 7, 2016, highlights the need for stronger law enforcement and business partnership to fight cybercrime. According to the NCA, cybercrime emerged as the largest proportion of total crime in the U.K., with “cyber enabled fraud” making up 36 percent of all crime reported, and “computer misuse” accounting for 17 percent.
The NCA’s Cyber Crime Assessment 2016, released July 7, 2016, highlights the need for stronger law enforcement and business partnership to fight cybercrime. According to the NCA, cybercrime emerged as the largest proportion of total crime in the U.K., with “cyber enabled fraud” making up 36 percent of all crime reported, and “computer misuse” accounting for 17 percent.
One explanation for the growth of cybercrime reports in the U.K. may be that the Brits are getting better at tracking it. The report notes that the U.K. Office of National Statistics only began including cybercrime for the first time last year in its annual Crime Survey for England and Wales.
“The ONS estimated that there were 2.46 million cyber incidents and 2.11 million victims of cyber crime in the U.K. in 2015,” the report’s authors wrote. “These figures highlight the clear shortfall in established reporting, with only 16,349 cyber dependent and approximately 700,000 cyber-enabled incidents reported to Action Fraud over the same period.”
The report also focuses on the increasing sophistication of organized cybercrime gangs that develop and deploy targeted, complex malicious software — such as Dridex and Dyre, which are aimed at emptying consumer and business bank accounts in the U.K. and elsewhere.
Avivah Litan, a fraud analyst with Gartner Inc., said cyber fraudsters in the U.K. bring their best game when targeting U.K. banks, which generally require far more stringent customer-facing security measures than U.S. banks — including smart cards and one-time tokens.
“I’m definitely hearing more about advanced attacks on U.K. banks than in the U.S.,” Litan said, adding that the anti-fraud measures put in place by U.K. banks have forced cybercriminals to focus more on social engineering U.K. retail and commercial banking customers.
Litan said if organized cybercrime gangs prefer to pick on U.K. banks, businesses and consumers, it may have more to do with convenience for the fraudsters than anything else. After all, she said, London is just two time zones behind Moscow, whereas the closest time zone in the U.S. is 7 hours behind.
“In most cases, the U.K. banks are pretty close to the fraudster’s own time zone, it’s a language the criminals can speak, and they’ve studied the banks’ systems up close and know how to get around security controls,” Litan said. “Just because you have more fraud controls doesn’t mean the fraudsters can’t beat them, it just forces the [crooks] to stay on top of their game. Why would you want to stay up all night doing online fraud against banks in the U.S. when you’d rather be out drinking with your buddies?”
The report observes that “despite the growth in scale and complexity of cyber crime and intensifying attacks, visible damage and losses have not (yet) been large enough to impact long term on shareholder value. The UK has yet to experience a cyber attack on business as damaging and publicly visible as the attack on the Target US retail chain.”
Although it would likely be difficult for a large, multinational European company to hide a breach similar in scope to that of the 2013 breach at Target, European nations generally have not had to adhere to the same data breach disclosure laws that are currently on the books in nearly every U.S. state — laws which prompt multiple U.S. companies each week to publicly acknowledge when they’ve suffered data breaches.
However, under the new European Union General Data Protection Regulation, companies that do business in Europe or with European customers will need to disclose “a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data transmitted, stored or otherwise processed.”
It may be some time yet before U.K. and European businesses start coming forward about data breaches: For better or worse, the GDPR requirements don’t go into full effect for two more years.
Hat tip to Trend Micro’s blog as the inspiration for this post.
Tags: avivah litan, Cyber Crime Assessment 2016, Dridex, Dyre, EU General Data Protection Regulation, European Union General Data Protection Regulation, Gartner Inc., U.K. National Crime Agency
This entry was posted on Friday, July 15th, 2016 at 12:14 pm and is filed under A Little Sunshine, The Coming Storm. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






