Avast, NordVPN Breaches Tied to Phantom User Accounts
Antivirus and security giant Avast and virtual private networking (VPN) software provider NordVPN each today disclosed months-long network intrusions that — while otherwise unrelated — shared a common cause: Forgotten or unknown user accounts that granted remote access to internal systems with little more than a password.
 Based in the Czech Republic, Avast bills itself as the most popular antivirus vendor on the market, with over 435 million users. In a blog post today, Avast said it detected and addressed a breach lasting between May and October 2019 that appeared to target users of its CCleaner application, a popular Microsoft Windows cleanup and repair utility.
Based in the Czech Republic, Avast bills itself as the most popular antivirus vendor on the market, with over 435 million users. In a blog post today, Avast said it detected and addressed a breach lasting between May and October 2019 that appeared to target users of its CCleaner application, a popular Microsoft Windows cleanup and repair utility.
Avast said it took CCleaner downloads offline in September to check the integrity of the code and ensure it hadn’t been injected with malware. The company also said it invalidated the certificates used to sign previous versions of the software and pushed out a re-signed clean update of the product via automatic update on October 15. It then disabled and reset all internal user credentials.
“Having taken all these precautions, we are confident to say that our CCleaner users are protected and unaffected,” Avast’s Jaya Baloo wrote.
This is not the first so-called “supply chain” attack on Avast: In September 2018, researchers at Cisco Talos and Morphisec disclosed that hackers had compromised the computer cleanup tool for more than a month, leading to some 2.27 million downloads of the corrupt CCleaner version.
Avast said the intrusion began when attackers used stolen credentials for a VPN service that was configured to connect to its internal network, and that the attackers were not challenged with any sort of multi-factor authentication — such as a one-time code generated by a mobile app.
“We found that the internal network was successfully accessed with compromised credentials through a temporary VPN profile that had erroneously been kept enabled and did not require 2FA,” Baloo wrote.
THE NORDVPN BREACH
Separately, NordVPN, a virtual private networking services that promises to “protect your privacy online,” confirmed reports that it had been hacked. Today’s acknowledgment and blog post mortem from Nord comes just hours after it emerged that NordVPN had an expired internal private key exposed, potentially allowing anyone to spin out their own servers imitating NordVPN,” writes Zack Whittaker at TechCrunch.

VPN software creates an encrypted tunnel between your computer and the VPN provider, effectively blocking your ISP or anyone else on the network (aside from you and the VPN provider) from being able to tell which sites you are visiting or viewing the contents of your communications. This can offer a measure of anonymity, but the user also is placing a great deal of trust in that VPN service not to get hacked and expose this sensitive browsing data.
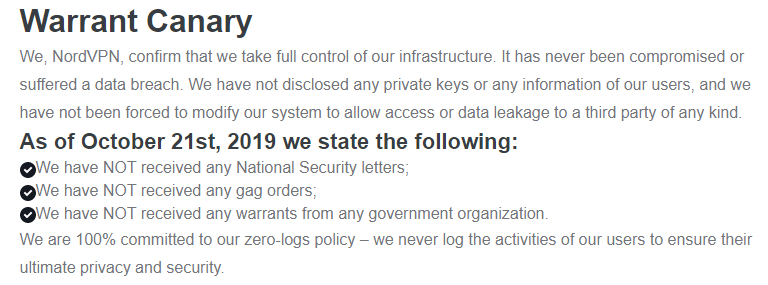
NordVPN’s account seems to downplay the intrusion, saying while the attackers could have used the private keys to intercept and view traffic for some of its customers’ traffic, the attackers would have been limited to eavesdropping on communications routing through just one of the company’s more than 3,000 servers.
“The server itself did not contain any user activity logs; none of our applications send user-created credentials for authentication, so usernames and passwords couldn’t have been intercepted either,” reads the NordVPN blog post. “On the same note, the only possible way to abuse the website traffic was by performing a personalized and complicated man-in-the-middle attack to intercept a single connection that tried to access NordVPN.”
NordVPN said the intrusion happened in March 2018 at one of its datacenters in Finland, noting that “the attacker gained access to the server by exploiting an insecure remote management system left by the datacenter provider while we were unaware that such a system existed.” NordVPN declined to name the datacenter provider, but said the provider removed the remote management account without notifying them on March 20, 2018.
“When we learned about the vulnerability the datacenter had a few months back, we immediately terminated the contract with the server provider and shredded all the servers we had been renting from them,” the company said. “We did not disclose the exploit immediately because we had to make sure that none of our infrastructure could be prone to similar issues. This couldn’t be done quickly due to the huge amount of servers and the complexity of our infrastructure.”
This page might need to be updated.
TechCrunch took NordVPN to task on the somewhat dismissive tone of its breach disclosure, noting that the company suffered a significant breach that went undetected for more than a year.
Kenneth White, director of the Open Crypto Audit Project, said on Twitter that based on the dumped Pastebin logs detailing the extent of the intrusion, “the attacker had full remote admin on their Finland node containers.”
“That’s God Mode folks,” White wrote. “And they didn’t log and didn’t detect it. I’d treat all their claims with great skepticism.”
ANALYSIS
Many readers are curious about whether they should enshroud all of their online communications by using a VPN. However, it’s important to understand the limitations of this technology, and to take the time to research providers before entrusting them with virtually all your browsing data — and possibly even compounding your privacy woes in the process. For a breakdown on what you should keep in mind when considering a VPN service, see this post.
Forgotten user accounts that provide remote access to internal systems — such as VPN and Remote Desktop services (RDP) — have been a persistent source of data breaches for years. Thousands of small to mid-sized brick-and-mortar businesses have been relieved of millions of customer payment card records over the years when their hacked IT contractors used the same remote access credentials at each client location.
Almost all of these breaches could have been stopped by requiring a second form of authentication in addition to a password, which can easily be stolen or phished.
The persistent supply chain attack against Avast brings to mind something I was considering the other day about the wisdom of allowing certain software to auto-update itself whenever it pleases. I’d heard from a reader who was lamenting the demise of programs like Secunia’s Personal Software Inspector and FileHippo, which allowed users to automatically download and install available updates for a broad range of third-party Windows programs.
These days, I find myself seeking out and turning off any auto-update functions in software that I install. I’d rather be alerted to new updates when I launch the program and have the ability to review what’s changing and whether anyone has experienced issues with the new version. I guess you could say years of dealing with unexpected surprises on Microsoft Patch Tuesdays has cured me of any sort of affinity I may have once had for auto-update features.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






