WikiLeaks: We’ll Work With Software Makers on Zero-Days
When WikiLeaks on Tuesday dumped thousands of files documenting hacking tools used by the U.S. Central Intelligence Agency, many feared WikiLeaks would soon publish a trove of so-called “zero days,” the actual computer code that the CIA uses to exploit previously unknown flaws in a range of software and hardware products used by consumers and businesses. But on Thursday, WikiLeaks editor-in-chief Julian Assange promised that his organization would work with hardware and software vendors to fix the security weaknesses prior to releasing additional details about the flaws.
“After considering what we think is the best way to proceed, and hearing these calls from some of the manufacturers, we have decided to work with them to give them exclusive access to additional technical details we have, so that fixes can be developed and pushed out,” Assange said in a press conference put on by his organization. “Once this material is effectively disarmed by us, we will publish additional details about what has been occurring.”
Source: Twitter
So-called “zero-day” flaws refer to vulnerabilities in hardware or software products that vendors first learn about when those flaws are already under active attack (i.e., the vendor has “zero days” to fix the vulnerability before it begins affecting its customers and users). Zero-day flaws are highly prized by cybercriminals and nation states alike because they potentially allow attackers to stealthily bypass a target’s digital defenses.
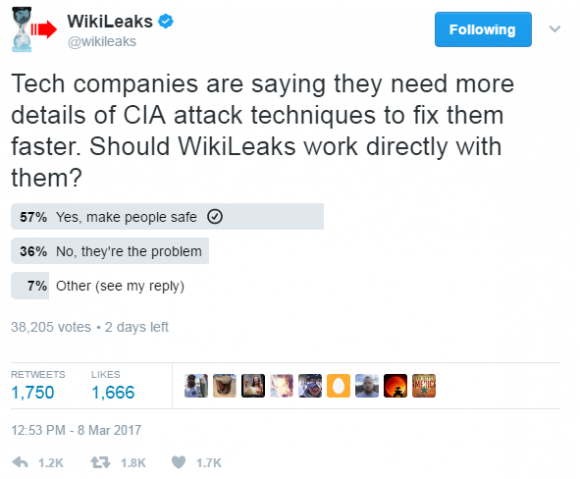
It’s unclear if WikiLeak’s decision to work with software makers on zero-days was impacted by a poll the organization took via its Twitter page over the past few days. The tweet read: “Tech companies are saying they need more details of CIA attack techniques to fix them faster. Should WikiLeaks work directly with them?”
So far, just over 38,000 people have responded, with a majority (57 percent) saying “Yes, make people safe,” while only 36 percent selected “no, they’re part of the problem.”
Assange didn’t offer additional details about the proposed information-sharing process he described, such as whether WikiLeaks would seek to work with affected vendors individually or if it might perhaps rely on a trusted third-party or third-parties to assist in that process.
But WikiLeaks seemed eager to address concerns voiced by many tech experts that leaking details about how to exploit these cyber attack weapons developed by the CIA would leave consumers and businesses caught in the middle as crooks and individual actors attempt to use the exploits for personal or financial gain. Perhaps to assuage such concerns, Assange said his vision for WikiLeaks was to act as a “neutral digital Switzerland that assists people all over the world to be secure.”
Nevertheless, even just the documentation on the CIA’s hacking tools that was released this week may offer curious and skilled hackers some strong pointers about where to look for unpatched security flaws that could be used to compromise systems running those software products. It will be interesting to see if and how often security researchers and bug hunters going forward credit the WikiLeaks CIA document dump for leading their research in a direction they hadn’t before considered.
Tags: CIA hack, Julian Assange, wikileaks
This entry was posted on Thursday, March 9th, 2017 at 1:10 pm and is filed under Other. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






