Who Is Agent Tesla?
A powerful, easy-to-use password stealing program known as Agent Tesla has been infecting computers since 2014, but recently this malware strain has seen a surge in popularity — attracting more than 6,300 customers who pay monthly fees to license the software. Although Agent Tesla includes a multitude of features designed to help it remain undetected on host computers, the malware’s apparent creator seems to have done little to hide his real-life identity.
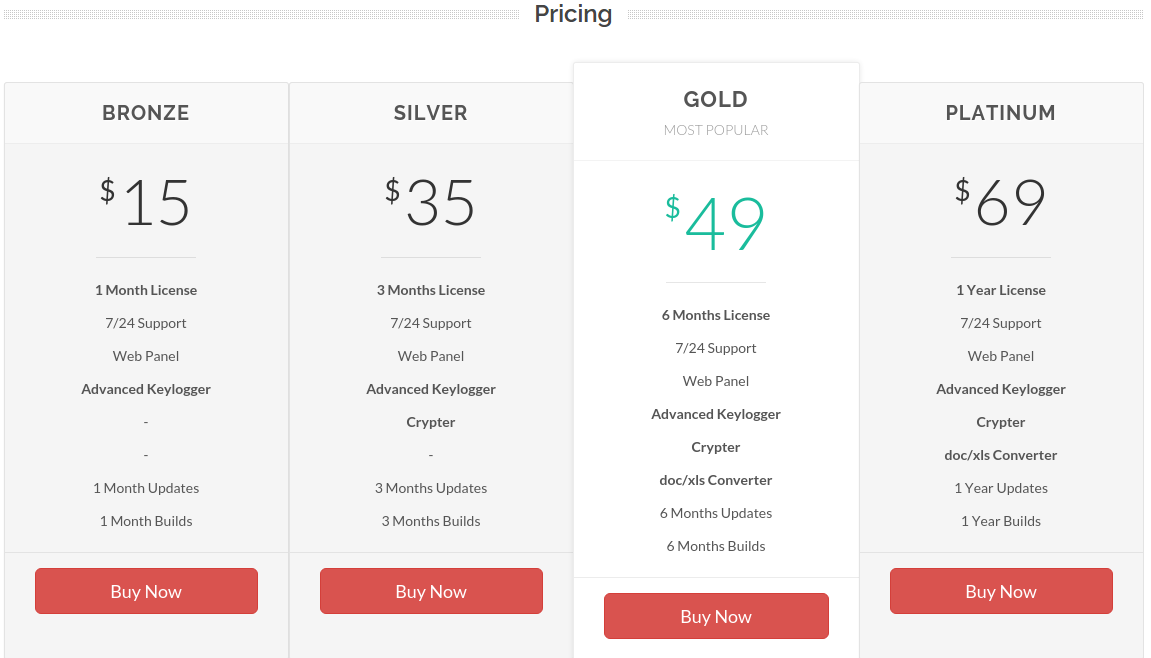
The proprietors of Agent Tesla market their product at agenttesla-dot-com, selling access to the software in monthly licenses paid for via bitcoin, for prices ranging from $15 to $69 per month depending on the desired features.
The Agent Tesla Web site emphasizes that the software is strictly “for monitoring your personel [sic] computer.” The site’s “about” page states that Agent Tesla “is not a malware. Please, don’t use for computers which is not access permission.” To backstop this disclaimer, the site warns that any users caught doing otherwise will have their software licenses revoked and subscriptions canceled.
At the same time, the Agent Tesla Web site and its 24/7 technical support channel (offered via Discord) is replete with instances of support personnel instructing users on ways to evade antivirus software detection, use software vulnerabilities to deploy the product, and secretly bundle the program inside of other file types, such as images, text, audio and even Microsoft Office files.
In August 2018, computer security firm LastLine said it witnessed a 100 percent increase in Agent Tesla instances detected in the wild over just a three month period.
“Acting as a fully-functional information stealer, it is capable of extracting credentials from different browsers, mail, and FTP clients,” LastLine wrote. “It logs keys and clipboards data, captures screen and video, and performs form-grabbing (Instagram, Twitter, Gmail, Facebook, etc.) attacks.”
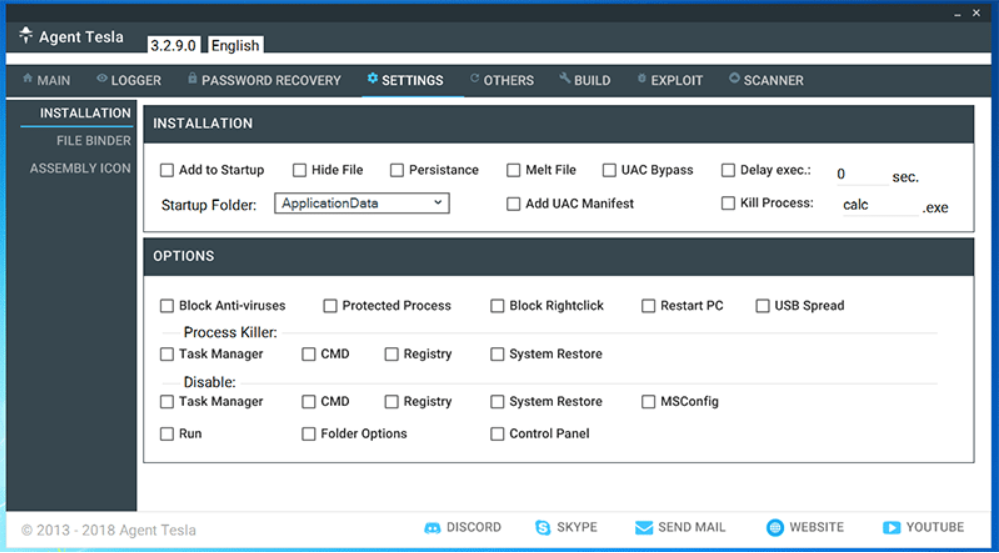
Most of the options included in Agent Tesla revolve around stealth, persistence, evading security tools, spreading to other computers, or tampering with system settings.
I CAN HAZ TESLA
The earliest versions of Agent Tesla were made available for free via a Turkish-language WordPress site that oddly enough remains online (agenttesla.wordpress-dot-com), although its home page now instructs users to visit the current AgentTesla-dot-com domain. Not long after that WordPress site was erected, its author(s) began charging for the software, accepting payments via a variety of means, including PayPal, Bitcoin and even wire transfer to several bank accounts in Turkey.
 Historic WHOIS Web site registration records maintained by Domaintools.com show that the current domain for the software — agenttesla-dot-com — was registered in 2014 to a young man from Antalya, Turkey named Mustafa can Ozaydin, and to the email address
Historic WHOIS Web site registration records maintained by Domaintools.com show that the current domain for the software — agenttesla-dot-com — was registered in 2014 to a young man from Antalya, Turkey named Mustafa can Ozaydin, and to the email address
That Gmail address is tied to a Youtube.com account for a Turkish individual by the same name who has uploaded exactly three videos over the past four years. In one of them, uploaded in October 2017 and titled “web panel,” Mr. can Ozaydin demonstrates how to configure a Web site. At around 3:45 in the video, we can see the purpose of this demonstration is to show people one way to install an Agent Tesla control panel to keep track of systems infected with the malware.
Incidentally, the administrator of the 24/7 live support channel for Agent Tesla users at one point instructed customers to view this same video if they were having trouble figuring out how to deploy the control panel.
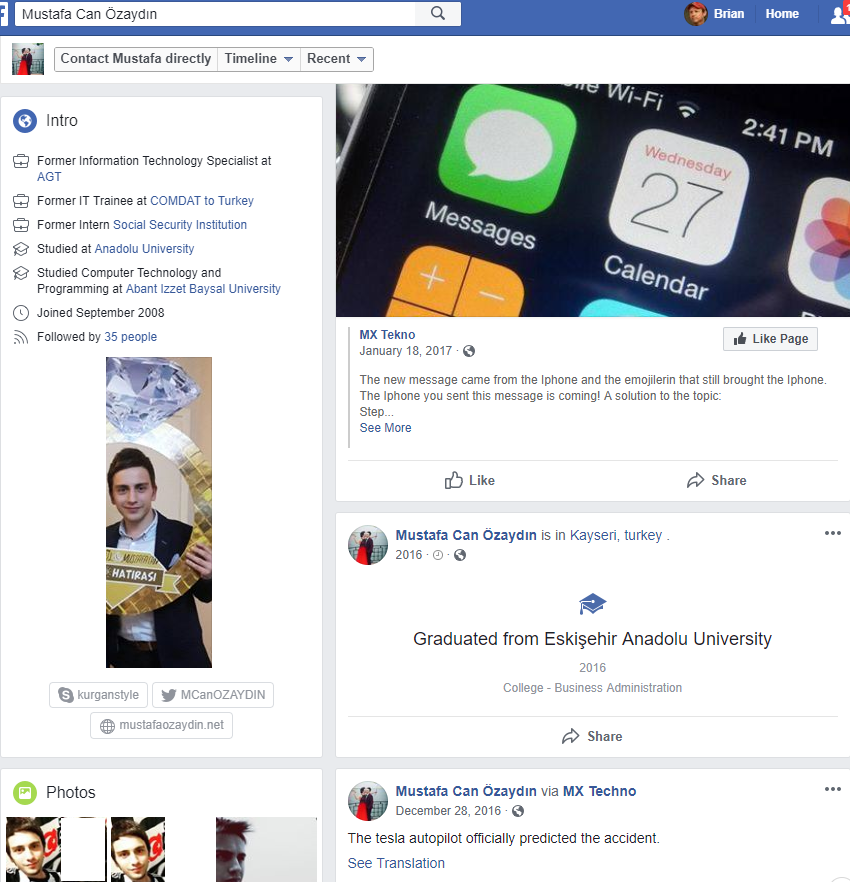
The profile picture shown in that Youtube account is remarkably similar to the one displayed on the Twitter account “MCanOZAYDIN.” This Twitter profile makes no mention of Agent Tesla, but it does state that Mustafa can Ozaydin is an “information technology specialist” in Antalya, Turkey.
That Twitter profile also shows up on a Facebook account for a Mustafa can Ozaydin from Turkey. A LinkedIn profile for a person by the same name from Antalya, Turkey states that Mr. can Ozaydin is currently a “systems support expert” for Memorial Healthcare Group, a hospital in Istanbul.
KrebsOnSecurity first reached out for comment to all of these accounts back in August 2018, but received no reply. Repeated attempts to reach those accounts this past week also elicited no response.
MALWARE OR BENIGN REMOTE ACCESS TOOL?
Many readers here have taken the view that tools like Agent Tesla are functionally no different from more mainstream “remote administration tools” like GoToMyPC, VNC, or LogMeIn, products that are frequently used by tech support personnel to remotely manage one or more systems to which those personnel legitimately have access rights.
U.S. federal prosecutors, meanwhile, have adopted a different position. Namely, when someone selling a remote administration tool begins instructing customers on how to install the product in ways that are arguably deceptive (such as through the use of software exploits, spam or disguising the tool as another program), the proprietor has crossed a legal line and can be criminally prosecuted under computer misuse laws.
In previous such cases, the prosecution’s argument has hinged on the procurement of chat logs showing that the software seller knew full well his product was being used to infect computers without the users’ knowledge or permission.
Last week, a Lexington, Ky. man was sentenced to 30 months in federal prison after pleading guilty to conspiracy to unlawfully access computers in connection with his admitted authorship of a remote access tool called LuminosityLink.
Colton Grubbs, 21, admitted to selling his software for $39.99 apiece to more than 6,000 customers in at least 78 different countries. LuminosityLink allowed his customers to record the keys that victims pressed on their keyboards, spy on victims using their computers’ cameras and microphones, view and download the computers’ files, and steal names and passwords used to access websites.
“Directly and indirectly, Grubbs offered assistance to his customers on how to use LuminosityLink for unauthorized computer intrusions through posts and group chats on websites such as HackForums,” the Justice Department wrote in a press release about the sentencing. Grubbs must also forfeit the proceeds of his crimes, including 114 bitcoin, presently valued at more than $725,000.
Around the time that Grubbs stopped responding to support requests on Hackforums, federal prosecutors were securing a guilty plea against Taylor Huddleston, a then 27-year-old programmer from Arkansas who sold the “NanoCore RAT.” Like Grubbs, Huddleston initially pleaded not guilty to computer intrusion charges, arguing that he wasn’t responsible for how customers used his products.
That is, until prosecutors presented Skype logs showing that Huddleston routinely helped buyers work out how to use the tools to secretly compromise remote computers. Huddleston is currently serving a 33-month sentence after pleading guilty to selling the NanoCore RAT.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.