The Value of a Hacked Company
Most organizations only grow in security maturity the hard way — that is, from the intense learning that takes place in the wake of a costly data breach. That may be because so few company leaders really grasp the centrality of computer and network security to the organization’s overall goals and productivity, and fewer still have taken an honest inventory of what may be at stake in the event that these assets are compromised.
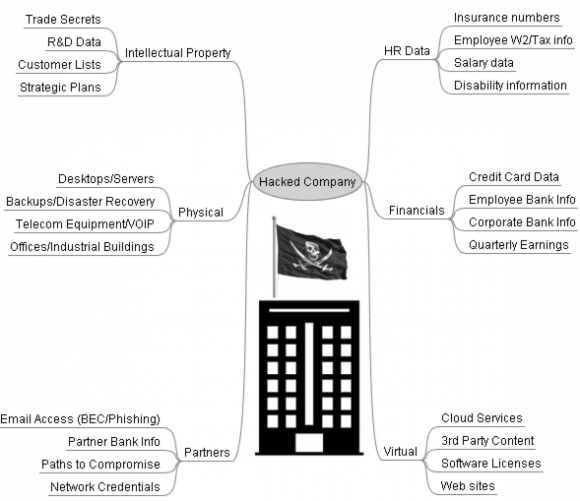
If you’re unsure how much of your organization’s strategic assets may be intimately tied up with all this technology stuff, ask yourself what would be of special worth to a network intruder. Here’s a look at some of the key corporate assets that may be of interest and value to modern bad guys.
This isn’t meant to be an exhaustive list; I’m sure we can all think of other examples, and perhaps if I receive enough suggestions from readers I’ll update this graphic. But the point is that whatever paltry monetary value the cybercrime underground may assign to these stolen assets individually, they’re each likely worth far more to the victimized company — if indeed a price can be placed on them at all.
In years past, most traditional, financially-oriented cybercrime was opportunistic: That is, the bad guys tended to focus on getting in quickly, grabbing all the data that they knew how to easily monetize, and then perhaps leaving behind malware on the hacked systems that abused them for spam distribution.
These days, an opportunistic, mass-mailed malware infection can quickly and easily morph into a much more serious and sustained problem for the victim organization (just ask Target). This is partly because many of the criminals who run large spam crime machines responsible for pumping out the latest malware threats have grown more adept at mining and harvesting stolen data.
That data mining process involves harvesting and stealthily testing interesting and potentially useful usernames and passwords stolen from victim systems. Today’s more clueful cybercrooks understand that if they can identify compromised systems inside organizations that may be sought-after targets of organized cybercrime groups, those groups might be willing to pay handsomely for such ready-made access.
It’s also never been easier for disgruntled employees to sell access to their employer’s systems or data, thanks to the proliferation of open and anonymous cybercrime forums on the Dark Web that serve as a bustling marketplace for such commerce. In addition, the past few years have seen the emergence of several very secretive crime forums wherein members routinely solicited bids regarding names of people at targeted corporations that could serve as insiders, as well as lists of people who might be susceptible to being recruited or extorted.
The sad truth is that far too many organizations spend only what they have to on security, which is often to meet some kind of compliance obligation such as HIPPA to protect healthcare records, or PCI certification to be able to handle credit card data, for example. However, real and effective security is about going beyond compliance — by focusing on rapidly detecting and responding to intrusions, and constantly doing that gap analysis to identify and shore up your organization’s weak spots before the bad guys can exploit them.
Those weak spots very well may be your users, by the way. A number of security professionals I know and respect claim that security awareness training for employees doesn’t move the needle much. These naysayers note that there will always be employees who will click on suspicious links and open email attachments no matter how much training they receive. While this is generally true, at least such security training and evaluation offers the employer a better sense of which employees may need more heavy monitoring on the job and perhaps even additional computer and network restrictions.
If you help run an organization, consider whether the leadership is investing enough to secure everything that’s riding on top of all that technology powering your mission: Chances are there’s a great deal more at stake than than you realize.
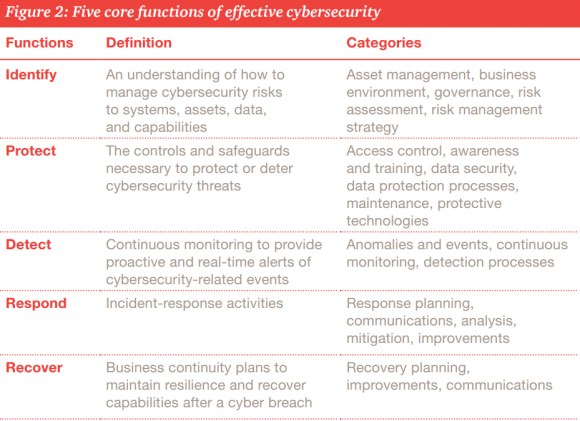
Organizational leaders in search of a clue about how to increase both their security maturity and the resiliency of all their precious technology stuff could do far worse than to start with the Cybersecurity Framework developed by the National Institute of Standards and Technology (NIST), the federal agency that works with industry to develop and apply technology, measurements, and standards. This primer (PDF) from PWC does a good job of explaining why the NIST Framework may be worth a closer look.
If you liked this post, you may enjoy the other two posts in this series — The Scrap Value of a Hacked PC and The Value of a Hacked Email Account.
Tags: HIPPA, National Institute of Standards and Technology, NIST, NIST Cybersecurity Framework, PCI, PWC, security maturity, The Value of a Hacked Company
This entry was posted on Thursday, July 14th, 2016 at 10:47 am and is filed under A Little Sunshine. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.