The Unsexy Threat to Election Security
Much has been written about the need to further secure our elections, from ensuring the integrity of voting machines to combating fake news. But according to a report quietly issued by a California grand jury this week, more attention needs to be paid to securing social media and email accounts used by election officials at the state and local level.

California has a civil grand jury system designed to serve as an independent oversight of local government functions, and each county impanels jurors to perform this service annually. On Wednesday, a grand jury from San Mateo County in northern California released a report which envisions the havoc that might be wrought on the election process if malicious hackers were able to hijack social media and/or email accounts and disseminate false voting instructions or phony election results.
“Imagine that a hacker hijacks one of the County’s official social media accounts and uses it to report false results on election night and that local news outlets then redistribute those fraudulent election results to the public,” the report reads.
“Such a scenario could cause great confusion and erode public confidence in our elections, even if the vote itself is actually secure,” the report continues. “Alternatively, imagine that a hacker hijacks the County’s elections website before an election and circulates false voting instructions designed to frustrate the efforts of some voters to participate in the election. In that case, the interference could affect the election outcome, or at least call the results into question.”
In San Mateo County, the office of the Assessor-County Clerk-Recorder and Elections (ACRE) is responsible for carrying out elections and announcing local results. The ACRE sends election information to some 43,000 registered voters who’ve subscribed to receive sample ballots and voter information, and its Web site publishes voter eligibility information along with instructions on how and where to cast ballots.
The report notes that concerns about the security of these channels is hardly theoretical: In 2010, intruders hijacked ACRE’s election results Web page, and in 2016, cyber thieves successfully breached several county employee email accounts in a spear-phishing attack.
In the wake of the 2016 attack, San Mateo County instituted two-factor authentication for its email accounts — requiring each user to log in with a password and a one-time code sent via text message to their mobile device. However, the ACRE uses its own Twitter, Facebook, Instagram and YouTube accounts to share election information, and these accounts are not currently secured by two-factor authentication, the report found.
“The Grand Jury finds that the security protections against hijacking of ACRE’s website, email, and social media accounts are not adequate to protect against the current cyber threats. These vulnerabilities expose the public to potential disinformation by hackers who could hijack an ACRE online communication platform to mislead voters before an election or sow confusion afterward. Public confidence is at stake, even if the vote itself is secure.”
The jury recommended the county take full advantage of the most secure two-factor authentication now offered by all of these social media platforms: The use of a FIDO physical security key, a small hardware device which allows the user to complete the login process simply by inserting the USB device and pressing a button. The key works without the need for any special software drivers [full disclosure: Yubico, a major manufacturer of security keys, is currently an advertiser on this site.]
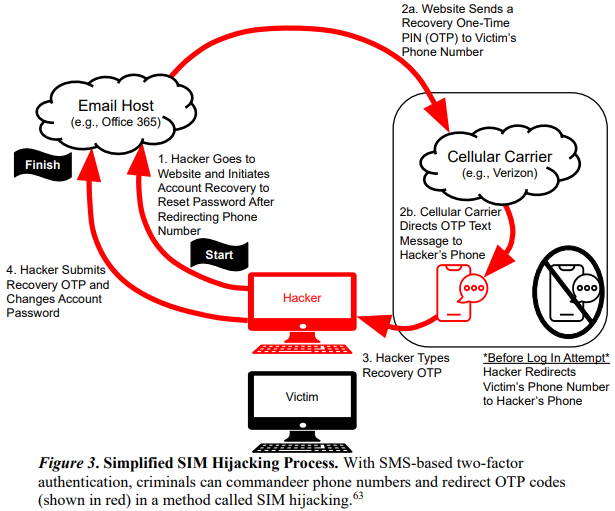
Additionally, the report urges election officials to migrate away from one-time codes sent via text message, as these can be intercepted via man-in-the-middle (MitM) and SIM-swapping attacks. MitM attacks use counterfeit login pages to steal credentials and one-time codes.
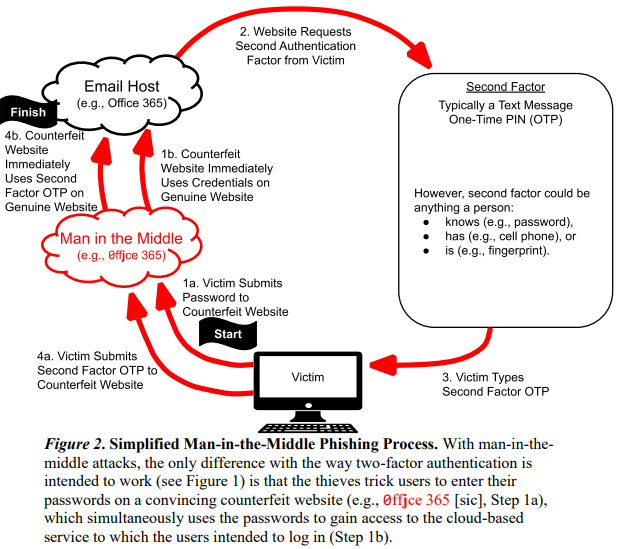
An unauthorized SIM swap is an increasingly rampant form of fraud in which scammers bribe or trick employees at mobile phone stores into seizing control of the target’s phone number and diverting all texts and phone calls to the attacker’s mobile device.
Samy Tarazi is a sergeant with the sheriff’s office in nearby Santa Clara County and a supervisor with the REACT Task Force, a team of law enforcement officers that has been tracking down individuals perpetrating SIM swapping attacks. Tarazi said he fully expects SIM swapping to emerge as a real threat to state and local election workers, as well as to staff and volunteers working for candidates.
“I wouldn’t be surprised if some major candidate or their staff has an email or social media account with tons of important stuff on there [whose password] can be reset with just a text message,” Tarazi told KrebsOnSecurity. “I hope that doesn’t happen, but politicians are regular people who use the same tools we use.”
A copy of the San Mateo County grand jury report is available here (PDF).
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






