The Limits of SMS for 2-Factor Authentication
A recent ping from a reader reminded me that I’ve been meaning to blog about the security limitations of using cell phone text messages for two-factor authentication online. The reader’s daughter had received a text message claiming to be from Google, warning that her Gmail account had been locked because someone in India had tried to access her account. The young woman was advised to expect a 6-digit verification code to be sent to her and to reply to the scammer’s message with that code.
 Mark Cobb, a computer technician in Reno, Nev., said had his daughter fallen for the ruse, her Gmail account would indeed have been completely compromised, and she really would have been locked out of her account because the crooks would have changed her password straight away.
Mark Cobb, a computer technician in Reno, Nev., said had his daughter fallen for the ruse, her Gmail account would indeed have been completely compromised, and she really would have been locked out of her account because the crooks would have changed her password straight away.
Cobb’s daughter received the scam text message because she’d enabled 2-factor authentication on her Gmail account, selecting the option to have Google request that she enter a 6-digit code texted to her cell phone each time it detects a login from an unknown computer or location (in practice, the code is to be entered on the Gmail site, not sent in any kind of texted or emailed reply).
In this case, the thieves already had her password — most likely because she re-used it on some other site that got hacked. Cobb says he and his daughter believe her mobile number and password may have been exposed as part of the 2012 breach at LinkedIn.
In any case, the crooks were priming her to expect a code and to repeat it back to them because that code was the only thing standing in the way of their seizing control over her account. And they could control when Google would send the code to her phone because Google would do this as soon as they tried to log in using her username and password. Indeed, the timing aspect of this attack helps make it more believable to the target.
This is a fairly clever — if not novel — attack, and it’s one I’d wager would likely fool a decent percentage of users who have enabled text messages as a form of two-factor authentication. Certainly, text messaging is far from the strongest form of 2-factor authentication, but it is better than allowing a login with nothing more than a username and password, as this scam illustrates.
Nevertheless, text messaging codes to users isn’t the safest way to do two-factor authentication, even if some entities — like the U.S. Social Security Administration and Sony’s Playstation network — are just getting around to offering two-factor via SMS.
But don’t take my word for it. That’s according to the National Institute of Standards and Technology (NIST), which recently issued new proposed digital authentication guidelines urging organizations to favor other forms of two-factor — such as time-base one-time passwords generated by mobile apps — over text messaging. By the way, NIST is seeking feedback on these recommendations.
If anyone’s interested, Sophos’s Naked Security blog has a very readable breakdown of what’s new in the NIST guidelines. Among my favorite highlights is this broad directive: Favor the user.
“To begin with, make your password policies user friendly and put the burden on the verifier when possible,” Sophos’s Chester Wisniewski writes. “In other words, we need to stop asking users to do things that aren’t actually improving security.” Like expiring passwords and making users change them frequently, for example.
Okay, so the geeks-in-chief are saying it’s time to move away from texting as a form of 2-factor authentication. And, of course, they’re right, because text messages are a lot like email, in that it’s difficult to tell who really sent the message, and the message itself is sent in plain text — i.e. is readable by anyone who happens to be lurking in the middle.
But security experts and many technology enthusiasts have a tendency to think that everyone should see the world through the lens of security, whereas most mere mortal users just want to get on with their lives and are perfectly content to use the same password across multiple sites — regardless of how many times they’re told not to do so.
Indeed, while many more companies now offer some form of two-factor authentication than did two or three years ago — consumer adoption of this core security feature remains seriously lacking. For example, the head of security at Dropbox recently told KrebsOnSecurity that less than one percent of its user base of 500 million registered users had chosen to turn on 2-factor authentication for their accounts. And Dropbox isn’t exactly a Johnny-come-lately to the 2-factor party: It has been offering 2-factor logins for a full four years now.
I doubt Dropbox is somehow an aberration in this regard, and it seems likely that other services also suffer from single-digit two-factor adoption rates. But if more consumers haven’t enabled two-factor options, it’s probably because a) it’s still optional and b) it still demands too much caring and understanding from the user about what’s going on and how these security systems can be subverted.
Personally, I favor app-based time-based one-time password (TOTP) systems like Google Authenticator, which continuously auto-generates a unique code via a mobile-based app.
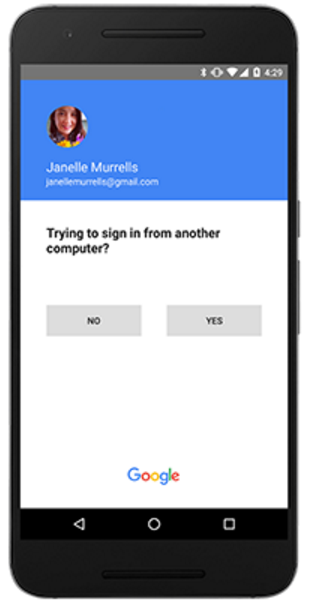
Google recently went a step further along the lines of where I’d like to see two-factor headed across the board, by debuting a new “push” authentication system that generates a prompt on the user’s mobile device that users need to tap to approve login requests. This is very similar to another push-based two-factor system I’ve long used and trusted — from Duo Security [full disclosure: Duo is an advertiser on this site].
For a comprehensive breakdown of which online services offer two-factor authentication and of what type, check out twofactorauth.org. And bear in mind that even if text-based authentication is all that’s offered, that’s still better than nothing. What’s more, it’s still probably more security than the majority of the planet has protecting their accounts.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.