The ‘Groove’ Ransomware Gang Was a Hoax
A number of publications in September warned about the emergence of “Groove,” a new ransomware group that called on competing extortion gangs to unite in attacking U.S. government interests online. It now appears that Groove was all a big hoax designed to toy with security firms and journalists.
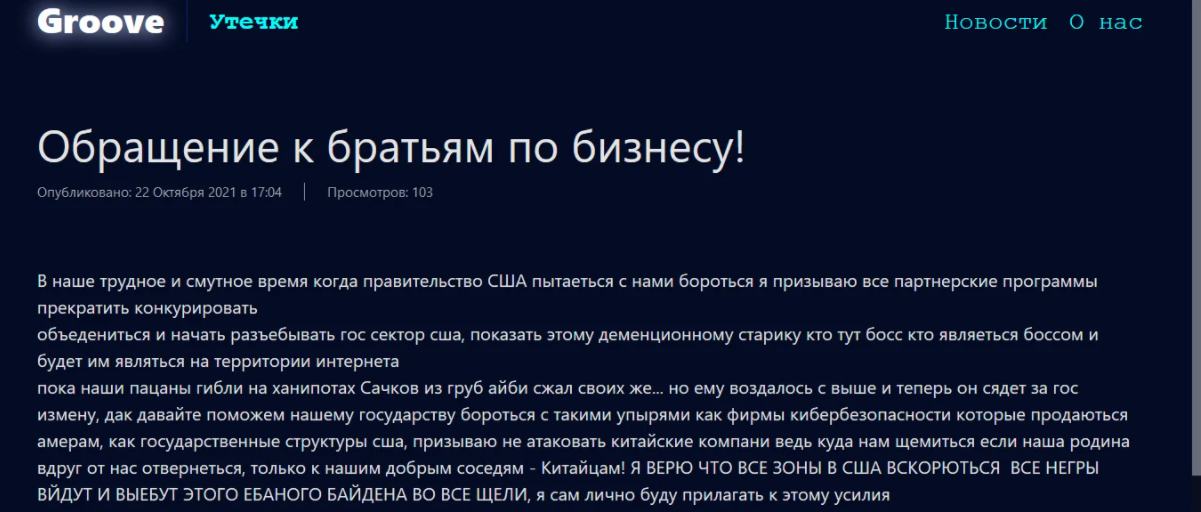
“An appeal to business brothers!” reads the Oct. 22 post from Groove calling for attacks on the United States government sector.
Groove was first announced Aug. 22 on RAMP, a new and fairly exclusive Russian-language darknet cybercrime forum.
“GROOVE is first and foremost an aggressive financially motivated criminal organization dealing in industrial espionage for about two years,” wrote RAMP’s administrator “Orange” in a post asking forum members to compete in a contest for designing a website for the new group. “Let’s make it clear that we don’t do anything without a reason, so at the end of the day, it’s us who will benefit most from this contest.”
According to a report jointly published by McAfee, Intel 471 and Coveware, Orange launched RAMP to appeal to ransomware-related threat actors who were were ousted from major cybercrime forums for being too toxic, or to cybercriminals who complained of being short-changed or stiffed altogether by different ransomware affiliate programs.
The report said RAMP was the product of a dispute between members of the Babuk ransomware gang, and that its members likely had connections to another ransomware group called BlackMatter.
“[McAfee] believes, with high confidence, that the Groove gang is a former affiliate or subgroup of the Babuk gang, who are willing to collaborate with other parties, as long as there is financial gain for them,” the joint report said. “Thus, an affiliation with the BlackMatter gang is likely.”
In the first week of September, Groove posted on its darknet blog nearly 500,000 login credentials for customers of Fortinet VPN products, usernames and passwords that could be used to remotely connect to vulnerable systems. Fortinet said the credentials were collected from systems that hadn’t yet implemented a patch issued in May 2019.
Some security experts said the post of the Fortinet VPN usernames and passwords was aimed at drawing new affiliates to Groove. But it seems more likely the credentials were posted to garner the attention of security researchers and journalists.
Sometime in the last week, Groove’s darknet blog disappeared. In a post on the Russian cybercrime forum XSS, an established cybercrook using the handle “Boriselcin” explained that Groove was little more than a pet project to screw with the media and security industry.
“For those who don’t understand what’s going on: I set up a fake Groove Gang and named myself a gang,” Boriselcin wrote. The rest of the post reads:
“They ate it up, I dumped 500k old Fortinet [access credentials] that no one needed and they ate it up. I say that I am going to target the U.S. government sector and they eat it up. Few journalists realized that this was all a show, a fake, and a scam! And my respect goes out to those who figured it out. I don’t even know what to do now with this blog with a ton of traffic. Maybe sell it? Now I just need to start writing [the article], but I can’t start writing it without checking everything.”
A review of Boriselcin’s recent postings on XSS indicate he has been planning this scheme for several months. On Sept. 13, Boriselcin posted that “several topics are ripening,” and that he intended to publish an article about duping the media and security firms.
“Manipulation of large information security companies and the media through a ransom blog,” he wrote. “It’s so funny to read Twitter and the news these days  But the result is great so far. Triggering the directors of information security companies. We fuck the supply chain of the information security office.”
But the result is great so far. Triggering the directors of information security companies. We fuck the supply chain of the information security office.”
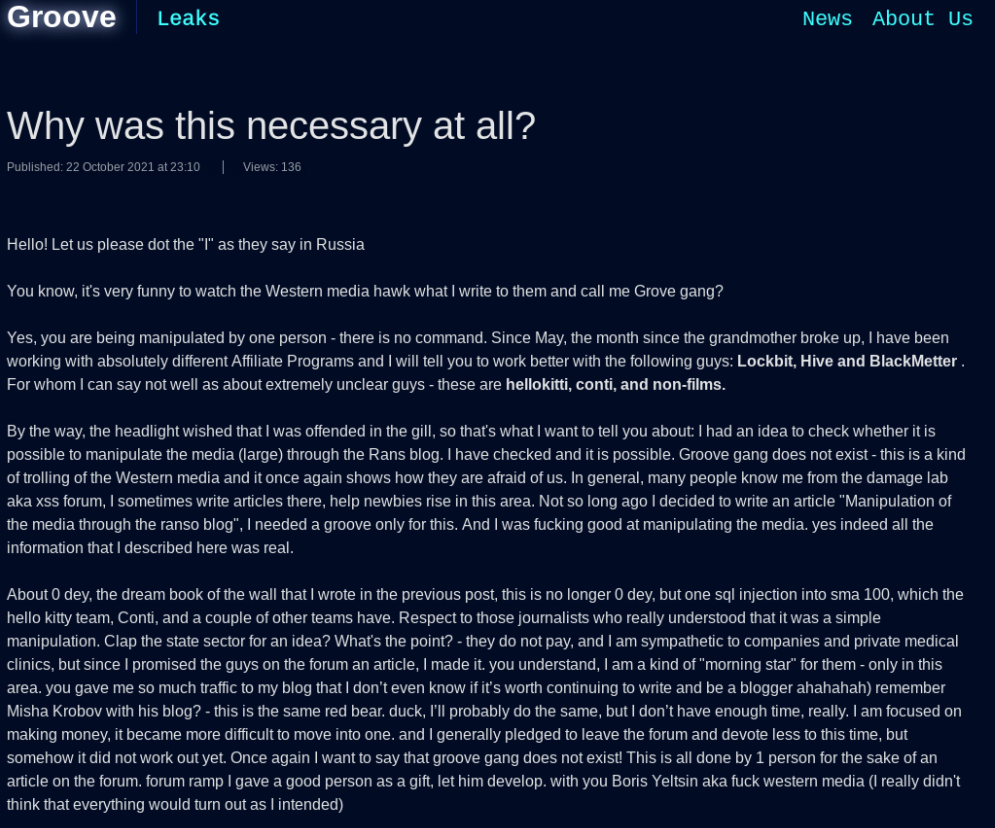
Image: @nokae8
Throughout its short existence, Groove listed only a handful of victims on its darknet victim shaming blog, leading some to conclude the group wasn’t much of a threat.
“I wouldn’t take this call too seriously,” tweeted The Record’s Catalin Cimpanu in response to tweets about Groove’s rallying cry to attack U.S. government interests. “Groove are low-tier actors with few skills.”
Normally, when a cybercriminal forum or enterprise turns out to be fake or a scam, we learn the whole thing was a sting operation by federal investigators from the United States and/or other countries. Perhaps the main reason we don’t see more scams like Boricelcin’s is because there’s not really any money in it.
But that’s not to say his cynical ploy fails to serve a larger purpose. Over the past few years, we’ve seen multiple ransomware gangs reinvent themselves and rebrand to evade prosecution or economic sanctions. From that vantage point, anything which sows confusion and diverts the media and security industry’s time and attention away from real threats is a net plus for the cybercriminal community.
Tom Hoffman, senior vice president of intelligence at Flashpoint, said mocking Western media outlets and reporters is a constant fixture of the conversation on top-tier cybercrime forums. ”
“It is clear the criminal actors read all the press releases and Twitter claims about them,” Hoffman said. “We know some of them just want to inflict pain on the West, so this type of trolling is likely to continue. With the high level of attention this one got, I would assume we will see some other copycats pretty soon.”
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






