Task Force Seeks to Disrupt Ransomware Payments
Some of the world’s top tech firms are backing a new industry task force focused on disrupting cybercriminal ransomware gangs by limiting their ability to get paid, and targeting the individuals and finances of the organized thieves behind these crimes.

In a 50-page report delivered to the Biden administration this week, top executives from Amazon, Cisco, FireEye, McAfee, Microsoft and dozens of other firms joined the U.S. Department of Justice (DOJ), Europol and the U.K. National Crime Agency in calling for an international coalition to combat ransomware criminals, and for a global network of ransomware investigation hubs.
The Ransomware Task Force urged the White House to make finding, frustrating and apprehending ransomware crooks a priority within the U.S. intelligence community, and to designate the current scourge of digital extortion as a national security threat.
The formation of the industry partnership comes just days after The Wall Street Journal broke the news that the DOJ was forming its own task force to deal with the “root causes” of ransomware. An internal DOJ memo reportedly “calls for developing a strategy that targets the entire criminal ecosystem around ransomware, including prosecutions, disruptions of ongoing attacks and curbs on services that support the attacks, such as online forums that advertise the sale of ransomware or hosting services that facilitate ransomware campaigns.”
According to security firm Emsisoft, almost 2,400 U.S.-based governments, healthcare facilities and schools were victims of ransomware in 2020.
“The costs of ransomware go far beyond the ransom payments themselves,” the task force report observes. “Cybercrime is typically seen as a white-collar crime, but while ransomware is profit-driven and ‘non-violent’ in the traditional sense, that has not stopped ransomware attackers from routinely imperiling lives.”
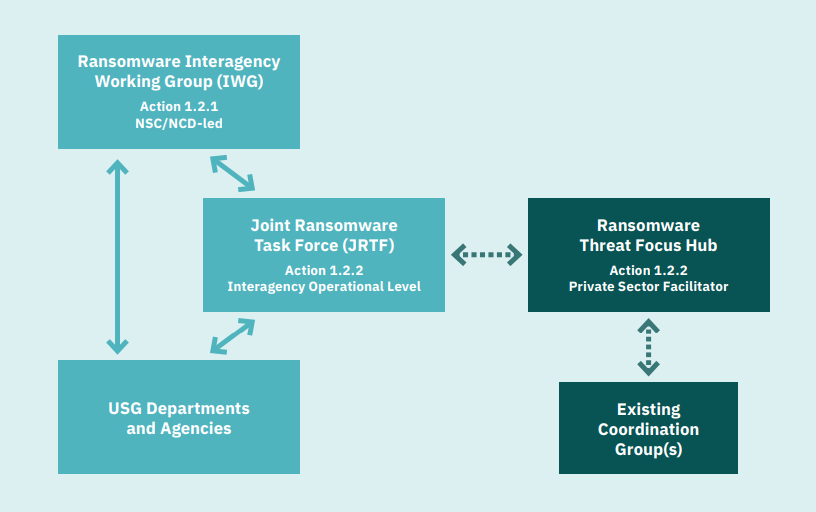
A proposed framework for a public-private operational ransomware campaign. Image: IST.
It is difficult to gauge the true cost and size of the ransomware problem because many victims never come forward to report the crimes. As such, a number of the task force’s recommendations focus on ways to encourage more victims to report the crimes to their national authorities, such as requiring victims and incident response firms who pay a ransomware demand to report the matter to law enforcement and possibly regulators at the U.S. Treasury Department.
Last year, Treasury issued a controversial memo warning that ransomware victims who end up sending digital payments to people already being sanctioned by the U.S. government for money laundering and other illegal activities could result in hefty fines.
Philip Reiner, executive director of the Institute for Security and Technology, said the reporting recommendations are one of several areas where federal agencies will likely need to dedicate more employees. For example, he said, expecting victims to clear ransomware payments with the Treasury Department first assumes the agency has the staff to respond in any kind of timeframe that might be useful for a victim undergoing a ransomware attack.
“That’s why we were so dead set in putting forward comprehensive framework,” Reiner said. “That way, Department of Homeland Security can do what they need to do, the State Department, Treasury gets involved, and it all needs to be synchronized for going after the bad guys with the same alacrity.”
Some have argued that making it illegal to pay a ransom is one way to decrease the number of victims who acquiesce to their tormentors’ demands. But the task force report says we’re nowhere near ready for that yet.
“Ransomware attackers require little risk or effort to launch attacks, so a prohibition on ransom payments would not necessarily lead them to move into other areas,” the report observes. “Rather, they would likely continue to mount attacks and test the resolve of both victim organizations and their regulatory authorities. To apply additional pressure, they would target organizations considered more essential to society, such as healthcare providers, local governments, and other custodians of critical infrastructure.”
“As such, any intent to prohibit payments must first consider how to build organizational cybersecurity maturity, and how to provide an appropriate backstop to enable organizations to weather the initial period of extreme testing,” the authors concluded in the report. “Ideally, such an approach would also be coordinated internationally to avoid giving ransomware attackers other avenues to pursue.”
The task force’s report comes as federal agencies have been under increased pressure to respond to a series of ransomware attacks that were mass-deployed as attackers began exploiting four zero-day vulnerabilities in Microsoft Exchange Server email products to install malicious backdoors. Earlier this month, the DOJ announced the FBI had conducted a first-of-its-kind operation to remove those backdoors from hundreds of Exchange servers at state and local government facilities.
Many of the recommendations in the Ransomware Task Force report are what you might expect, such as encouraging voluntary information sharing on ransomware attacks; launching public awareness campaigns on ransomware threats; exerting pressure on countries that operate as safe havens for ransomware operators; and incentivizing the adoption of security best practices through tax breaks.
A few of the more interesting recommendations (at least to me) included:
-Limit legal liability for ISPs that act in good faith trying to help clients secure their systems.
-Create a federal “cyber response and recovery fund” to help state and local governments or critical infrastructure companies respond to ransomware attacks.
-Require cryptocurrency exchanges to follow the same “know your customer” (KYC) and anti-money laundering rules as financial institutions, and aggressively targeting exchanges that do not.
-Have insurance companies measure and assert their aggregated ransomware losses and establish a common “war chest” subrogation fund “to evaluate and pursue strategies aimed at restitution, recovery, or civil asset seizures, on behalf of victims and in conjunction with law enforcement efforts.”
-Centralize expertise in cryptocurrency seizure, and scaling criminal seizure processes.
-Create a standard format for reporting ransomware incidents.
-Establish a ransomware incident response network.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






