Privnotes.com Is Phishing Bitcoin from Users of Private Messaging Service Privnote.com
For the past year, a site called Privnotes.com has been impersonating Privnote.com, a legitimate, free service that offers private, encrypted messages which self-destruct automatically after they are read. Until recently, I couldn’t quite work out what Privnotes was up to, but today it became crystal clear: Any messages containing bitcoin addresses will be automatically altered to include a different bitcoin address, as long as the Internet addresses of the sender and receiver of the message are not the same.
Earlier this year, KrebsOnSecurity heard from the owners of Privnote.com, who complained that someone had set up a fake clone of their site that was fooling quite a few regular users of the service.
And it’s not hard to see why: Privnotes.com is confusingly similar in name and appearance to the real thing, and comes up second in Google search results for the term “privnote.” Also, anyone who mistakenly types “privnotes” into Google search may see at the top of the results a misleading paid ad for “Privnote” that actually leads to privnotes.com.
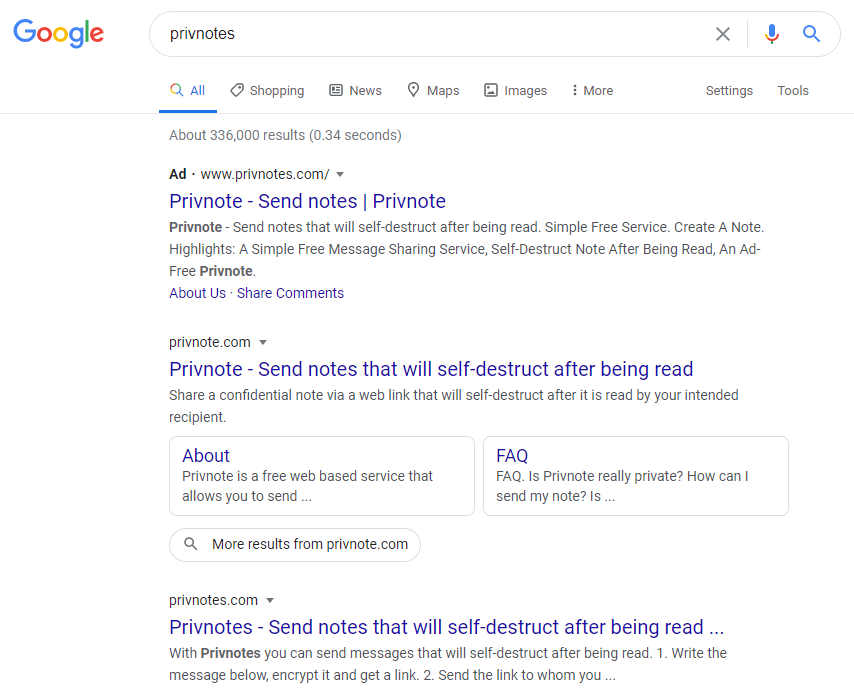
A Google search for the term “privnotes” brings up a misleading paid ad for the phishing site privnotes.com, which is listed above the legitimate site — privnote.com.
Privnote.com (the legit service) employs technology that encrypts all messages so that even Privnote itself cannot read the contents of the message. And it doesn’t send and receive messages. Creating a message merely generates a link. When that link is clicked or visited, the service warns that the message will be gone forever after it is read.
But according to the owners of Privnote.com, the phishing site Privnotes.com does not fully implement encryption, and can read and/or modify all messages sent by users.
“It is very simple to check that the note in privnoteS is sent unencrypted in plain text,” Privnote.com explained in a February 2020 message, responding to inquiries from KrebsOnSecurity. “Moreover, it doesn’t enforce any kind of decryption key when opening a note and the key after # in the URL can be replaced by arbitrary characters and the note will still open.”
But that’s not the half of it. KrebsOnSecurity has learned that the phishing site Privnotes.com uses some kind of automated script that scours messages for bitcoin addresses, and replaces any bitcoin addresses found with its own bitcoin address. The script apparently only modifies messages if the note is opened from a different Internet address than the one that composed the address.
Here’s an example, using the bitcoin wallet address from bitcoin’s Wikipedia page as an example. The following message was composed at Privnotes.com from a computer with an Internet address in New York, with the message, “please send money to bc1qar0srrr7xfkvy5l643lydnw9re59gtzzwf5mdq thanks”:
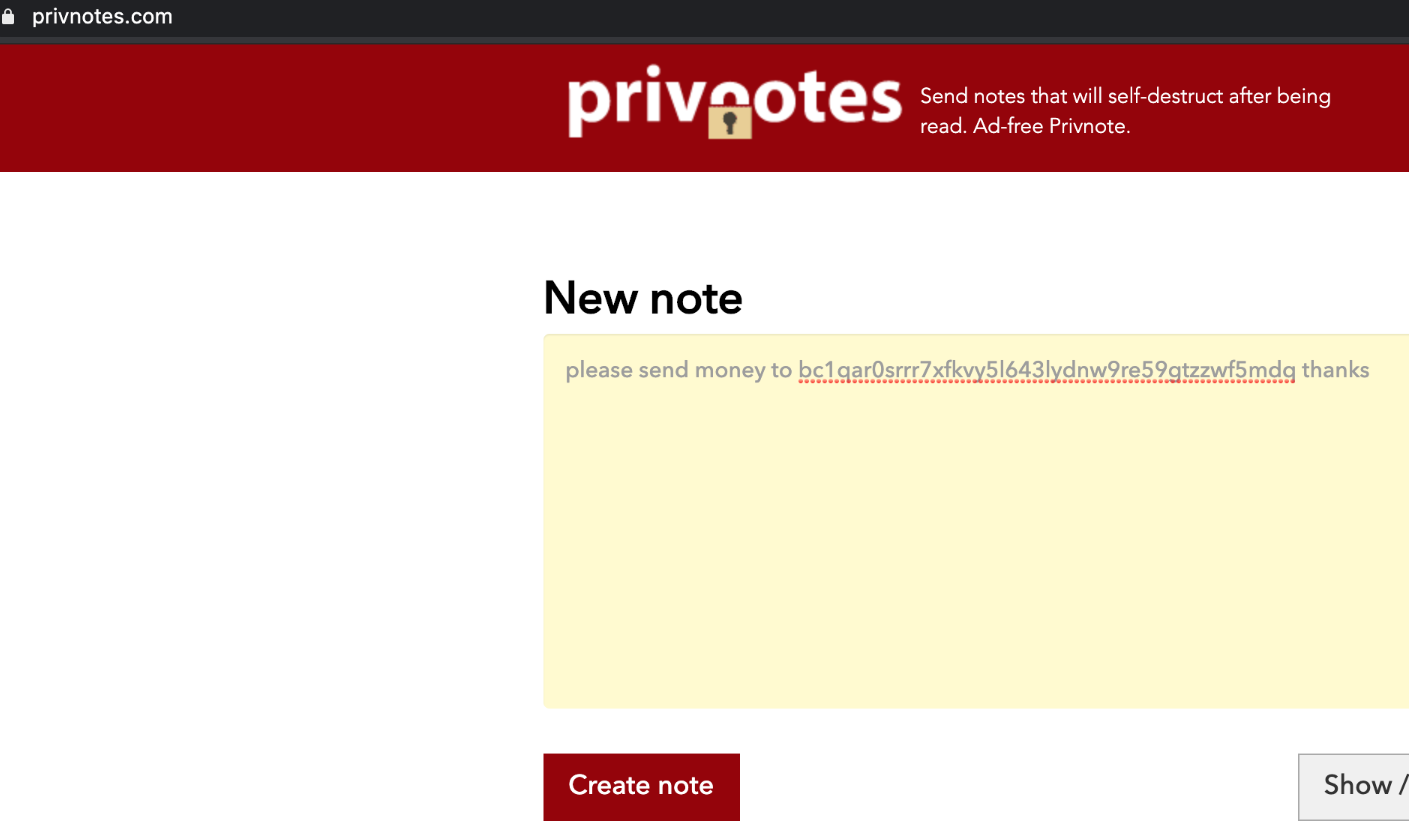
A test message composed on privnotes.com, which is phishing users of the legitimate encrypted message service privnote.com. Pay special attention to the bitcoin address in this message.
When I visited the Privnotes.com link generated by clicking the “create note” button on the above page from a different computer with an Internet address in California, this was the result. As you can see, it lists a different bitcoin address, albeit one with the same first four characters the same.
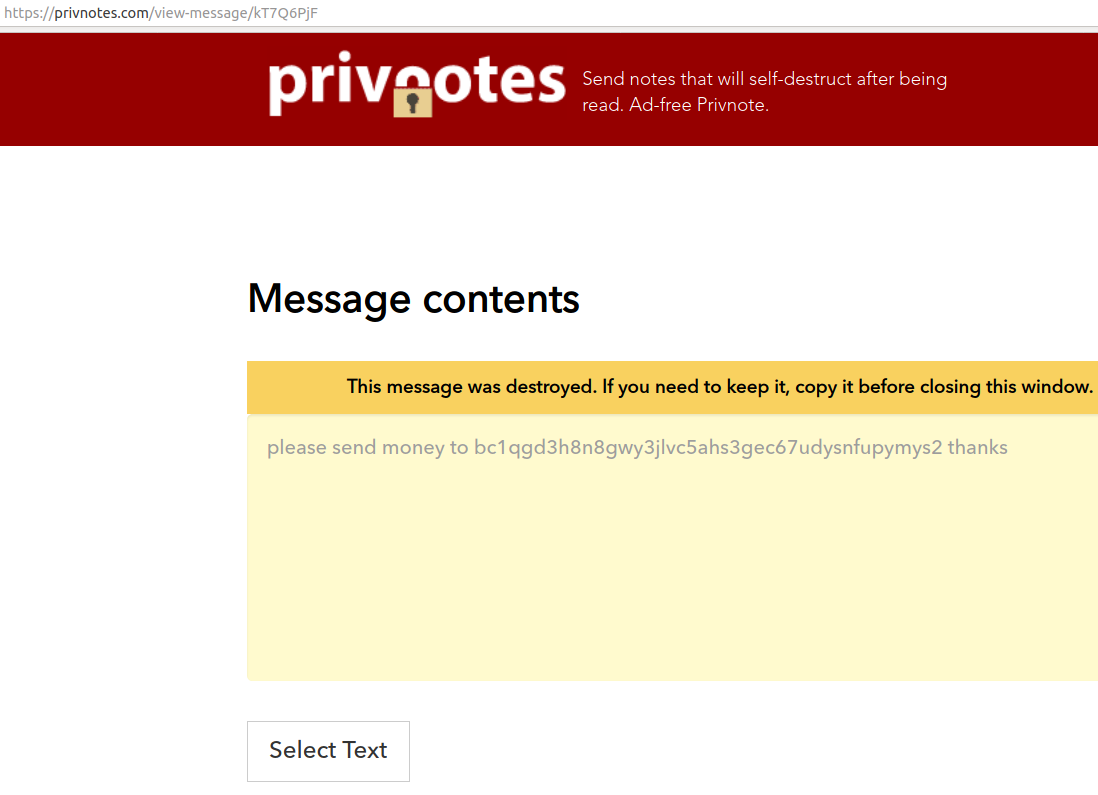
The altered message. Notice the bitcoin address has been modified and is not the same address that was sent in the original note.
Several other tests confirmed that the bitcoin modifying script does not seem to change message contents if the sender and receiver’s IP addresses are the same, or if one composes multiple notes with the same bitcoin address in it.
Allison Nixon, the security expert who helped me with this testing, said the script also only seems to replace the first instance of a bitcoin address if it’s repeated within a message, and the site stops replacing a wallet address if it is sent repeatedly over multiple messages.
“And because of the design of the site, the sender won’t be able to view the message because it self destructs after one open, and the type of people using privnote aren’t the type of people who are going to send that bitcoin wallet any other way for verification purposes,” said Nixon, who is chief research officer at Unit 221B. “It’s a pretty smart scam.”
Given that Privnotes.com is phishing bitcoin users, it’s a fair bet the phony service also is siphoning other sensitive data from people who use their site.
“So if there are password dumps in the message, they would be able to read that, too,” Nixon said. “At first, I thought that was their whole angle, just to siphon data. But the bitcoin wallet replacement is probably much closer to the main motivation for running the fake site.”
Even if you never use or plan to use the legitimate encrypted message service Privnote.com, this scam is a great reminder why it pays to be extra careful about using search engines to find sites that you plan to entrust with sensitive data. A far better approach is to bookmark such sites, and rely exclusively on those instead.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






