Notorious ‘Hijack Factory’ Shunned from Web
Score one for the good guys: Bitcanal, a Portuguese Web hosting firm long accused of helping spammers hijack large swaths of dormant Internet address space over the years, was summarily kicked off the Internet this week after a half-dozen of the company’s bandwidth providers chose to sever ties with the company.

Spammers and Internet service providers (ISPs) that facilitate such activity often hijack Internet address ranges that have gone unused for periods of time. Dormant or “unannounced” address ranges are ripe for abuse partly because of the way the global routing system works: Miscreants can “announce” to the rest of the Internet that their hosting facilities are the authorized location for given Internet addresses. If nothing or nobody objects to the change, the Internet address ranges fall into the hands of the hijacker.
For years, security researchers have tracked the suspected theft of millions of IPv4 Internet addresses back to Bitcanal, which was also doing business under the name “Ebony Horizon.” Experts say shortly after obtaining a chunk of IP addresses, Bitcanal would apparently sell or lease the space to spammers, who would then begin sending junk email from those addresses — taking full advantage of the good or at least neutral Internet reputation of the previous owner to evade anti-spam blacklists.
Much of the hijacked address space routed by Bitcanal was once assigned to business entities that no longer exist. But some of the more brazen hijacks attributed to Bitcanal and its customers involved thousands of Internet addresses assigned to active organizations, such as the company’s well-documented acquisition of address space assigned to the Texas State Attorney General’s office, as well as addresses managed by the U.S. Department of Defense.
Bitcanal’s reputation finally caught up with the company late last month, when anti-spam activist and researcher Ron Guilmette documented yet another new major IP address hijack at the company and challenged Bitcanal’s upstream Internet providers to stop routing traffic for it (KrebsOnSecurity has published several stories about previous high-profile IP address hijacks involving spammers who were flagged by Guilmette).
Guilmette said Bitcanal and its proprietor — Portuguese businessman Joao Silveira — have a well-documented history of “behaving badly and coloring outside the lines for literally years.”
“His actions in absconding with other people’s IP address space, over the years, are those of either a spoiled child or else those of a sociopath, depending on one’s personal point of view,” Guilmette said. “In either case the Internet will, by and large, be glad to see his backside, and will be better off without him.”
Doug Madory, a researcher for Internet performance management firm Dyn (now owned by Oracle), published a blog post chronicling Bitcanal’s history as an address “hijack factory.” That post also documents the gradual ostracization of Bitcanal over the past week, as one major Internet exchange after another pulled the plug on the company.
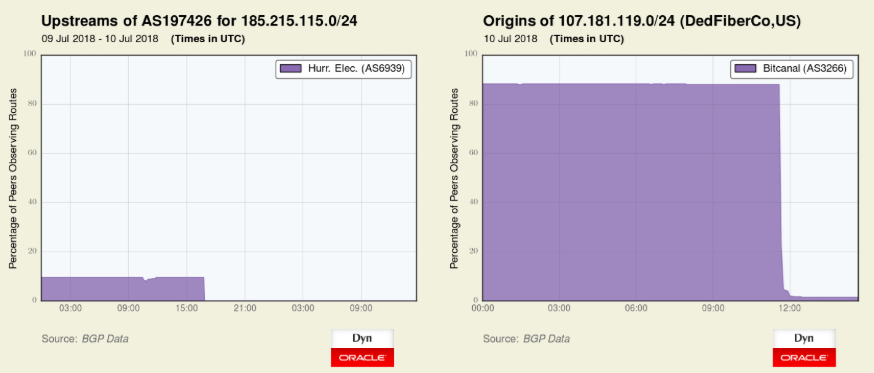
Dyn’s depiction of Bitcanal’s final remaining upstream Internet provider pulling the plug on the company on July 10, effectively severing it from existence on the Web. Source: Dyn.
Reached for comment just days before Bitcanal was shunned by all of its peering providers, Mr. Silveira expressed shock and surprise over what he called unfair attacks against his company’s reputation. He blamed the besmirchment on one or two “bad” customers who abused his service over the years.
“My thought is that one or two customer in my network maybe [imitated] people acting like a client and force the errors or injecting bad network space,” Silveira said in an emailed response to KrebsOnSecurity. “I am not the problem and this public trial and conviction will not solve the prefix hijacking matter. If these questions remain without solution, those actors will keep doing it.”
Another business tied to Mr. Silveira suggests that Bitcanal/Ebony Horizon has long been actively involved in obtaining sizable chunks of Internet address space on behalf of its clients. The same contact phone number that once existed on the (now unreachable) home page of Bitcanal.com also appears on the homepage of ip4transfer.net, a company that advertises the ability to lease large chunks of Internet address space.

Bitcanal owner Joao Silveira.
The current WHOIS registration records for ip4transfer.net are mostly redacted by domain registrar GoDaddy, but the name Ebony Horizon appears as the current business name, and Mr. Silveira’s name is on the original domain registration records from 2016, according to historic WHOIS records maintained by DomainTools [full disclosure: DomainTools is an advertiser on this blog].
Much of the content on ipv4transfer.net seeks to answer questions about what customers should expect when leasing address space from the company, including the possibility that some leased address ranges could be flagged as malicious or spammy by Spamhaus.org, an anti-spam group whose spam blacklists are relied upon by many ISPs to block large-scale spam campaigns. Prior to Bitcanal’s final disconnection this week, Spamhaus had blacklisted virtually all of Bitcanal’s address ranges as sources of spam and/or malicious email.
“Legitimate IP address space brokers don’t need to spend a lot of ink telling their customers how to avoid getting their shiny new IP address blocks listed by Spamhaus, or how to get them unlisted by Spamhaus, or what to do about it if the shiny new block they just purchased is already listed by Spamhaus,” Guilmette said.
Because the global routing of Internet address space is largely based on trust relationships between and among network operators, those operators have an obligation to ensure they’re not inadvertently facilitating the hijacking of Internet address space.
Perhaps coincidentally to the disconnection of Bitcanal, the RIPE Network Coordination Centre — one of the five global Regional Internet Registries (RIRs) providing Internet address allocations — on July 10 published an analysis of route hijacking activity across the Internet. The analysis includes a set of tips for network operators to help avoid contributing to the overall problem.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






