New Charges, Sentencing in Satori IoT Botnet Conspiracy
The U.S. Justice Department today criminally charged a Canadian and a Northern Ireland man for allegedly conspiring to build botnets that enslaved hundreds of thousands of routers and other Internet of Things (IoT) devices for use in large-scale distributed denial-of-service (DDoS) attacks. In addition, a defendant in the United States was sentenced today to drug treatment and 18 months community confinement for his admitted role in the botnet conspiracy.
Indictments unsealed by a federal court in Alaska today allege 20-year-old Aaron Sterritt from Larne, Northern Ireland, and 31-year-old Logan Shwydiuk of Saskatoon, Canada conspired to build, operate and improve their IoT crime machines over several years.
Prosecutors say Sterritt, using the hacker aliases “Vamp” and “Viktor,” was the brains behind the computer code that powered several potent and increasingly complex IoT botnet strains that became known by exotic names such as “Masuta,” “Satori,” “Okiru” and “Fbot.”
Shwydiuk, a.k.a. “Drake,” “Dingle, and “Chickenmelon,” is alleged to have taken the lead in managing sales and customer support for people who leased access to the IoT botnets to conduct their own DDoS attacks.
A third member of the botnet conspiracy — 22-year-old Kenneth Currin Schuchman of Vancouver, Wash. — pleaded guilty in Sept. 2019 to aiding and abetting computer intrusions in September 2019. Schuchman, whose role was to acquire software exploits that could be used to infect new IoT devices, was sentenced today by a judge in Alaska to 18 months of community confinement and drug treatment, followed by three years of supervised release.

Kenneth “Nexus-Zeta” Schuchman, in an undated photo.
The government says the defendants built and maintained their IoT botnets by constantly scanning the Web for insecure devices. That scanning primarily targeted devices that were placed online with weak, factory default settings and/or passwords. But the group also seized upon a series of newly-discovered security vulnerabilities in these IoT systems — commandeering devices that hadn’t yet been updated with the latest software patches.
Some of the IoT botnets enslaved hundreds of thousands of hacked devices. For example, by November 2017, Masuta had infected an estimated 700,000 systems, allegedly allowing the defendants to launch crippling DDoS attacks capable of hurling 100 gigabits of junk data per second at targets — enough firepower to take down many large websites.
In 2015, then 15-year-old Sterritt was involved in the high-profile hack against U.K. telecommunications provider TalkTalk. Sterritt later pleaded guilty to his part in the intrusion, and at his sentencing in 2018 was ordered to complete 50 hours of community service.
The indictments against Sterritt and Shwydiuk (PDF) do not mention specific DDoS attacks thought to have been carried out with the IoT botnets. In an interview today with KrebsOnSecurity, prosecutors in Alaska declined to discuss any of their alleged offenses beyond building, maintaining and selling the above-mentioned IoT botnets.
But multiple sources tell KrebsOnSecuirty Vamp was principally responsible for the 2016 massive denial-of-service attack that swamped Dyn — a company that provides core Internet services for a host of big-name Web sites. On October 21, 2016, an attack by a Mirai-based IoT botnet variant overwhelmed Dyn’s infrastructure, causing outages at a number of top Internet destinations, including Twitter, Spotify, Reddit and others.
In 2018, authorities with the U.K.’s National Crime Agency (NCA) interviewed a suspect in connection with the Dyn attack, but ultimately filed no charges against the youth because all of his digital devices had been encrypted.
“The principal suspect of this investigation is a UK national resident in Northern Ireland,” reads a June 2018 NCA brief on their investigation into the Dyn attack (PDF), dubbed Operation Midmonth. “In 2018 the subject returned for interview, however there was insufficient evidence against him to provide a realistic prospect of conviction.”
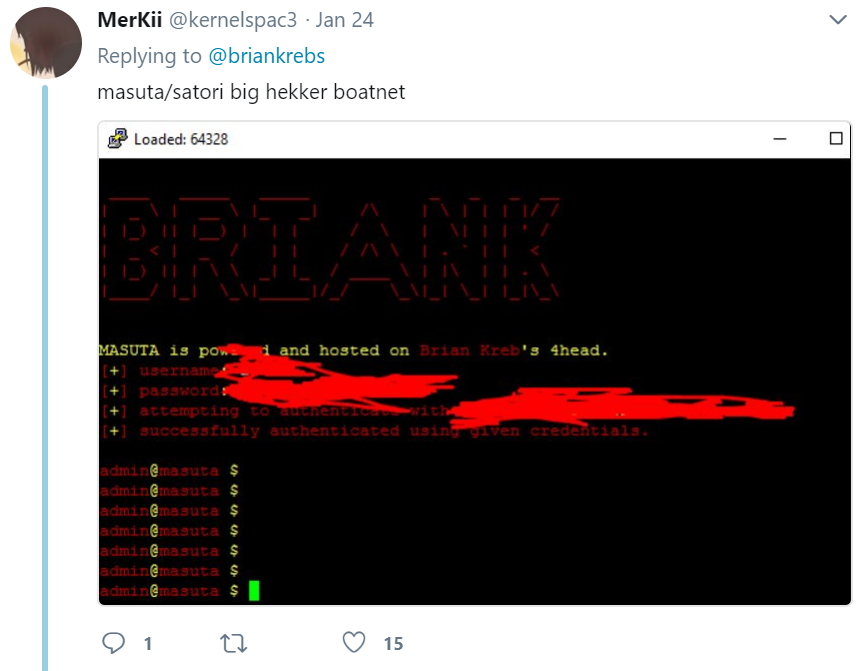
The login prompt for Nexus Zeta’s IoT botnet included the message “Masuta is powered and hosted on Brian Kreb’s [sic] 4head.” To be precise, it’s a 5head.
The unsealing of the indictments against Sterritt and Shwydiuk came just minutes after Schuchman was sentenced today. Schuchman has been confined to an Alaskan jail for the past 13 months, and Chief U.S. District Judge Timothy Burgess today ordered the sentence of 18 months community confinement to begin Aug. 1.
Community confinement in Schuchman’s case means he will spend most or all of that time in a drug treatment program. In a memo (PDF) released prior to Schuchman’s sentencing today, prosecutors detailed the defendant’s ongoing struggle with narcotics, noting that on multiple occasions he was discharged from treatment programs after testing positive for Suboxone — which is used to treat opiate addiction an is sometimes abused by addicts — and for possessing drug contraband.
The government’s sentencing memo also says Schuchman on multiple occasions absconded from pretrial supervision, and went right back to committing the botnet crimes for which he’d been arrested — even communicating with Sterritt about the details of the ongoing FBI investigation.
“Defendant’s performance on pretrial supervision has been spectacularly poor,” prosecutors explained. “Even after being interviewed by the FBI and put on restrictions, he continued to create and operate a DDoS botnet.”
Prosecutors told the judge that when he was ultimately re-arrested by U.S. Marshals, Schuchman was found at a computer in violation of the terms of his release. In that incident, Schuchman allegedly told his dad to trash his computer, before successfully encrypting his hard drive (which the Marshals service is still trying to decrypt). According to the memo, the defendant admitted to marshals that he had received and viewed videos of “juveniles engaged in sex acts with other juveniles.”
“The circumstances surrounding the defendant’s most recent re-arrest are troubling,” the memo recounts. “The management staff at the defendant’s father’s apartment complex, where the defendant was residing while on abscond status, reported numerous complaints against the defendant, including invitations to underage children to swim naked in the pool.”
Adam Alexander, assistant US attorney for the district of Alaska, declined to say whether the DOJ would seek extradition of Sterritt and Shwydiuk. Alexander said the success of these prosecutions is highly dependent on the assistance of domestic and international law enforcement partners, as well as a list of private and public entities named at the conclusion of the DOJ’s press release on the Schuchman sentencing (PDF).
Chief Judge Burgess was the same magistrate who presided over the 2018 sentencing of the co-authors of Mirai, a highly disruptive IoT botnet strain whose source code was leaked online in 2016 and was built upon by the defendants in this case. Both Mirai co-authors were sentenced to community service and home confinement thanks to their considerable cooperation with the government’s ongoing IoT botnet investigations.
Asked whether he was satisfied with the sentence handed down against Schuchman, Alexander maintained it was more than just another slap on the wrist, noting that Schuchman has waived his right to appeal the conviction and faces additional confinement of two years if he absconds again or fails to complete his treatment.
“In every case the statutory factors have to do with the history of the defendants, who in these crimes tend to be extremely youthful offenders,” Alexander said. “In this case, we had a young man who struggles with mental health and really pronounced substance abuse issues. Contrary to what many people might think, the goal of the DOJ in cases like this is not to put people in jail for as long as possible but to try to achieve the best balance of safeguarding communities and affording the defendant the best possible chance of rehabilitation.”
William Walton, supervisory special agent for the FBI’s cybercrime investigation division in Anchorage, Ala., said he hopes today’s indictments and sentencing send a clear message to what he described as a relatively insular and small group of individuals who are still building, running and leasing IoT-based botnets to further a range of cybercrimes.
“One of the things we hope in our efforts here and in our partnerships with our international partners is when we identify these people, we want very much to hold them to account in a just but appropriate way,” Walton said. “Hopefully, any associates who are aspiring to fill the vacuum once we take some players off the board realize that there are going to be real consequences for doing that.”
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






