Is Your Browser Extension a Botnet Backdoor?
A company that rents out access to more than 10 million Web browsers so that clients can hide their true Internet addresses has built its network by paying browser extension makers to quietly include its code in their creations. This story examines the lopsided economics of extension development, and why installing an extension can be such a risky proposition.

Singapore-based Infatica[.]io is part of a growing industry of shadowy firms trying to woo developers who maintain popular browser extensions — desktop and mobile device software add-ons available for download from Apple, Google, Microsoft and Mozilla designed to add functionality or customization to one’s browsing experience.
Some of these extensions have garnered hundreds of thousands or even millions of users. But here’s the rub: As an extension’s user base grows, maintaining them with software updates and responding to user support requests tends to take up an inordinate amount of the author’s time. Yet extension authors have few options for earning financial compensation for their work.
So when a company comes along and offers to buy the extension — or pay the author to silently include some extra code — that proposal is frequently too good to pass up.
For its part, Infatica seeks out authors with extensions that have at least 50,000 users. An extension maker who agrees to incorporate Infatica’s computer code can earn anywhere from $15 to $45 each month for every 1,000 active users.
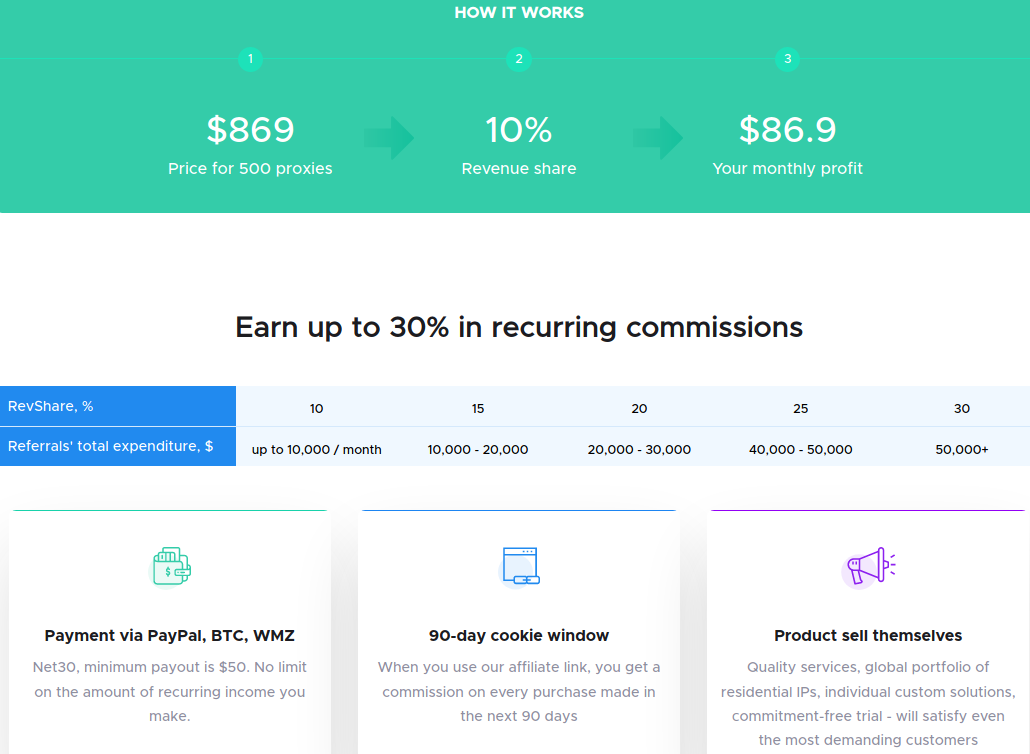
An Infatica graphic explaining the potential benefits for extension owners.
Infatica’s code then uses the browser of anyone who has that extension installed to route Web traffic for the company’s customers, including marketers or anyone able to afford its hefty monthly subscription charges.
The end result is when Infatica customers browse to a web site, that site thinks the traffic is coming from the Internet address tied to the extension user, not the customer’s.
Infatica prices its service based on the volume of web traffic a customer is seeking to anonymize, from $360 a month for 40 gigabytes all the way to $20,000 a month for 10,000 gigabytes of data traffic pushed through millions of residential computers.
THE ECONOMICS OF EXTENSIONS
Hao Nguyen is the developer behind ModHeader, an extension used by more than 400,000 people to test the functionality of websites by making it easier for users to modify the data shared with those sites. When Nguyen found himself spending increasing amounts of his time and money supporting the extension, he tried including ads in the program to help offset costs.
ModHeader users protested loudly against the change, and Nguyen removed the ads — which he said weren’t making him much money anyway.
“I had spent at least 10 years building this thing and had no luck monetizing it,” he told KrebsOnSecurity.
Nguyen said he ignored multiple requests from different companies offering to pay him to insert their code, mainly because the code gave those firms the ability to inject whatever they wanted into his program (and onto his users’ devices) at any time.
Then came Infatica, whose code was fairly straightforward by comparison, he said. It restricted the company to routing web requests through his users’ browsers, and did not try to access more sensitive components of the user’s browser experience, such as stored passwords and cookies, or viewing the user’s screen.
More importantly, the deal would net him at least $1,500 a month, and possibly quite a bit more.
“I gave Infatica a try but within a few days I got a lot of negative user reviews,” he said. “They didn’t like that the extension might be using their browser as a proxy for going to not so good places like porn sites.”
Again he relented, and removed the Infatica code.
A TARGET-RICH ENVIRONMENT
These days, Nguyen is focusing more of his time on chrome-stats.com, which provides detailed information on more than 150,000 extensions. The service is free for limited use, but subscribers who pay a monthly fee can get access to more resources, such as older extension versions and details about their code components.
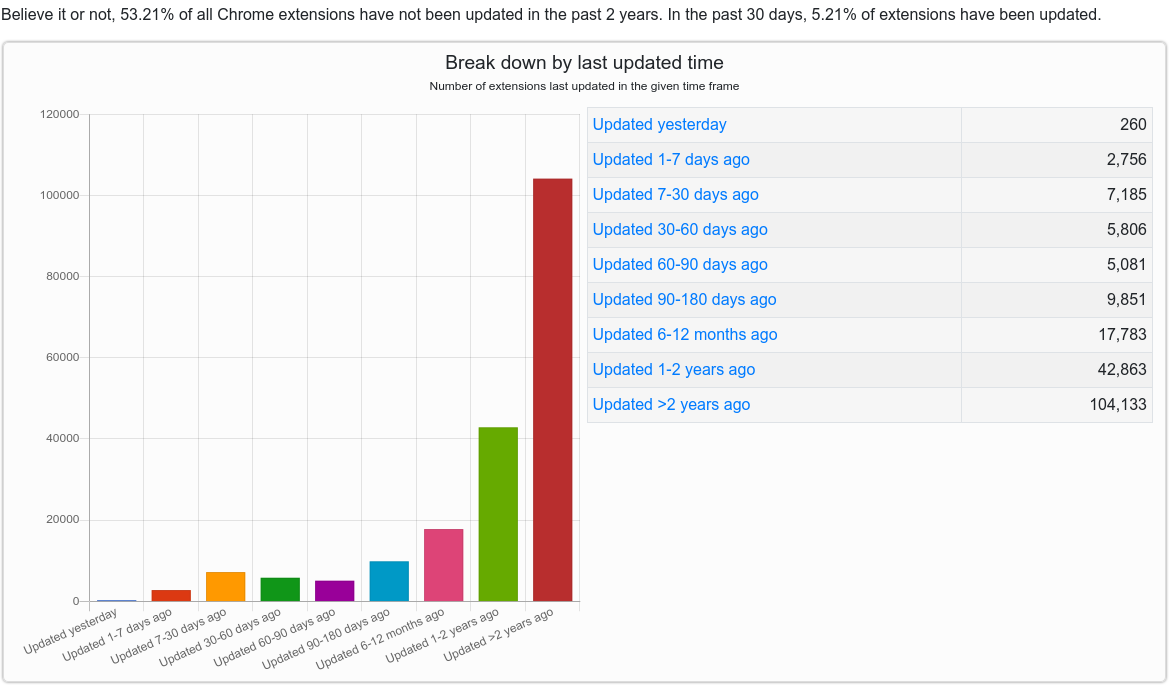
According to chrome-stats.com, the majority of extensions — more than 100,000 of them — are effectively abandoned by their authors, or haven’t been updated in more than two years. In other words, there a great many developers who are likely to be open to someone else buying up their creation and their user base.
The vast majority of extensions are free, although a handful that have attracted a large and loyal enough following have been able to charge for their creations or for subscription services tied to the extension. But last year, Google announced it was shutting down paid Chrome extensions offered on its Chrome Web Store.
Nguyen said this will only exacerbate the problem of frustrated developers turning to offers from dodgy marketing firms.
“It’s a really tough marketplace for extension developers to be able to monetize and get reward for maintaining their extensions,” he said. “There are tons of small developers who haven’t been able to do anything with their extensions. That’s why some of them will go into shady integration or sell the extension for some money and just be done with it.”
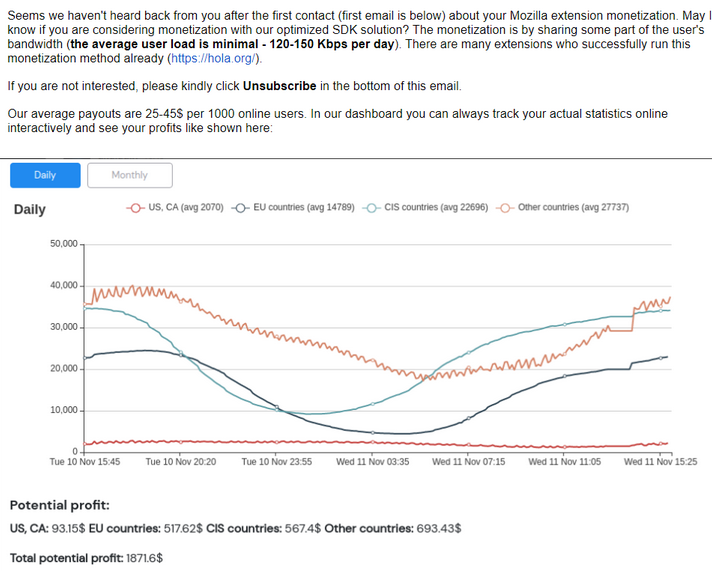
A solicitation sent by Infatica to the developer of the SponsorBlock extension. Image: sponsor.ajay.app
WHO IS INFATICA?
It is unclear how many extensions currently incorporate Infatica’s code. KrebsOnSecurity searched for extensions that invoke several domains tied to Infatica’s Web proxy service (e.g., extendbalanc[.]org, ipv4v6[.]info). This research was conducted using Nguyen’s site and crxcavator.io, a similar extension research site owned by networking giant Cisco Systems.
Those searches revealed that Infatica’s code has been associated with at least three dozen extensions over the past few years, including several that had more than 100,000 users. One of those is Video Downloader Plus, which at one point claimed nearly 1.4 million active users.
The founder and director of Infatica — a resident of Biysk, Russia named Vladimir Fomenko — did not respond to multiple requests for comment.

Infatica founder Vladimir M. Fomenko.
Fomenko is the sole director of the iNinja VPN, another service that obfuscates the true Internet address of its more than 400,000 users. It stands to reason that iNinja VPN also is not only offering its customers a way to obfuscate their Internet address, but is actively using those same systems to route traffic for other customers: A Chrome browser plugin and ad blocker by the same name whose code includes Infatica’s “extenbalanc” domain has 400,000 users.
That would put Infatica in line with the activities of another major controversial VPN/proxy provider: Illuminati, a.k.a. “HolaVPN.” In 2015, security researchers discovered that users of the HolaVPN browser extension were being used to funnel Web traffic for other people. Indeed, in the screenshot above, Infatica’s marketing team can be seen comparing its business model to that of HolaVPN.
Fomenko has appeared in two previous KrebsOnSecurity stories; both concerned King Servers (a.k.a. “Hosting Solution Ltd.“), a hosting company he has operated for years which caters mostly to adult websites.
In 2016, hackers suspected of working for Russian state security services compromised databases for election systems in Arizona and Illinois. Six of the eight Internet addresses identified by the FBI as sources of the attack traced back to King Servers. In an interview with The New York Times several months later, Fomenko flatly denied having any ties to the hacking.
According to the Russian daily Novaya Gazeta, revelations about the 2016 hacking incident’s ties to King Servers led to treason charges against Sergey Mikhaylov, the former deputy chief of Russia’s top anti-cybercrime unit.
Russian authorities charged that Mikhaylov had tipped off the FBI to information about Fomenko and King Servers. In 2019, Mikhaylov was convicted and sentenced to 22 years in a penal colony.
BE SPARING IN TRUSTING EXTENSIONS
Browser extensions — however useful or fun they may seem when you install them — typically have a great deal of power and can effectively read and/or write all data in your browsing sessions. The powers granted to each extension are roughly spelled out in its “manifest,” basically a description of what it will be able to access once you incorporate it into your browser.
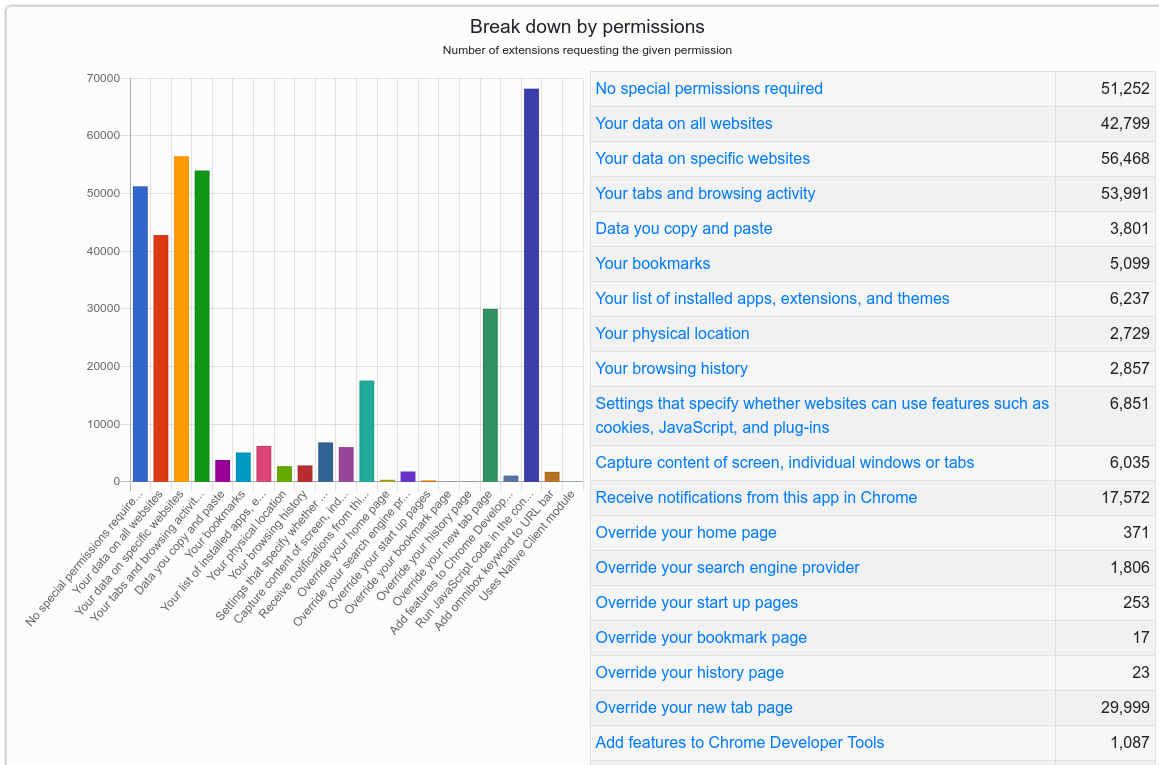
According to Nguyen’s chrome-stats.com, about a third of all extensions for Chrome — by far the most widely-used Web browser — require no special permissions. But the remainder require the user to place a good deal of trust in the extension’s author. For example, approximately 30 percent can view all of your data on all or specific websites, or index your open tabs and browsing activity.
More than 68,000 Chrome extensions allow the execution of arbitrary code in the context of webpages, effectively allowing the extension to alter the appearance and functionality of specific sites.
I hope it’s obvious by this point, but readers should be extremely cautious about installing extensions — sticking mainly to those that are actively supported and respond to user concerns.
Personally, I do not make much use of browser extensions. In almost every case I’ve considered installing one I’ve been sufficiently spooked by the permissions requested that I ultimately decided it wasn’t worth the risk, given that any extension can go rogue at the whims of its author.
If you’re the type of person who uses multiple extensions, it may be wise to adopt a risk-based approach going forward. Given the high stakes that typically come with installing an extension, consider carefully whether having the extension is truly worth it. This applies equally to plug-ins designed for Web site content management systems like WordPress and Joomla.
Do not agree to update an extension if it suddenly requests more permissions than a previous version. This should be a giant red flag that something is not right. If this happens with an extension you trust, you’d be well advised to remove it entirely.
Also, never download and install an extension just because some Web site says you need it to view some type of content. Doing so is almost always a high-risk proposition. Here, Rule #1 from KrebsOnSecurity’s Three Rules of Online Safety comes into play: “If you didn’t go looking for it, don’t install it.” Finally, in the event you do wish to install something, make sure you’re getting it directly from the entity that produced the software.
Google Chrome users can see any extensions they have installed by clicking the three dots to the right of the address bar, selecting “More tools” in the resulting drop-down menu, then “Extensions.” In Firefox, click the three horizontal bars next to the address bar and select “Add-ons,” then click the “Extensions” link on the resulting page to view any installed extensions.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.