Equifax Breach Fallout: Your Salary History
In May, KrebsOnSecurity broke a story about lax security at a payroll division of big-three credit bureau Equifax that let identity thieves access personal and financial data on an unknown number of Americans. Incredibly, this same division makes it simple to access detailed salary and employment history on a large portion of Americans using little more than someone’s Social Security number and date of birth — both data elements that were stolen in the recent breach at Equifax.
At issue is a service provided by Equifax’s TALX division called The Work Number. The service is designed to provide automated employment and income verification for prospective employers, and tens of thousands of companies report employee salary data to it. The Work Number also allows anyone whose employer uses the service to provide proof of their income when purchasing a home or applying for a loan.
The homepage for this Equifax service wants to assure visitors that “Your personal information is protected.”
“With your consent your personal data can be retrieved only by credentialed verifiers,” Equifax assures us, referring mainly to banks and other entities that request salary data for purposes of setting credit limits.
Sadly, this isn’t anywhere near true because most employers who contribute data to The Work Number — including Fortune 100 firms, government agencies and universities — rely on horribly weak authentication for access to the information.
To find out how easy it is to view your detailed salary history, you’ll need your employer’s name or employer code. Helpfully, this page lets you look that up quite easily (although if you opt to list employers alphabetically by the fist letter of the company name, there are so many entries for each letter that I found Equifax’s database simply crashes half the time instead of rendering the entire list).
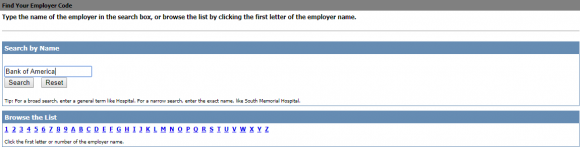
What’s needed to access your salary and employment history? Go here, and enter the employer name or employer code. After that, it asks for a “user ID.” This might sound like privileged information, but in most cases this is just the employees’s Social Security number (or a portion of it).
At the next step, the site asks visitors to “enter your PIN,” short for Personal Identification Number. However, in the vast majority of cases this appears to be little more than someone’s eight-digit date of birth. The formats differ by employer, but it’s usually either yyyy/mm/dd or mm/dd/yyyy, without the slashes.
Successful validation to the system produces two sets of data: An employee’s salary and employment history going back at least a decade, and a report listing all of the entities (ostensibly, the aforementioned “credentialed verifiers”) that have previously requested and viewed this information.
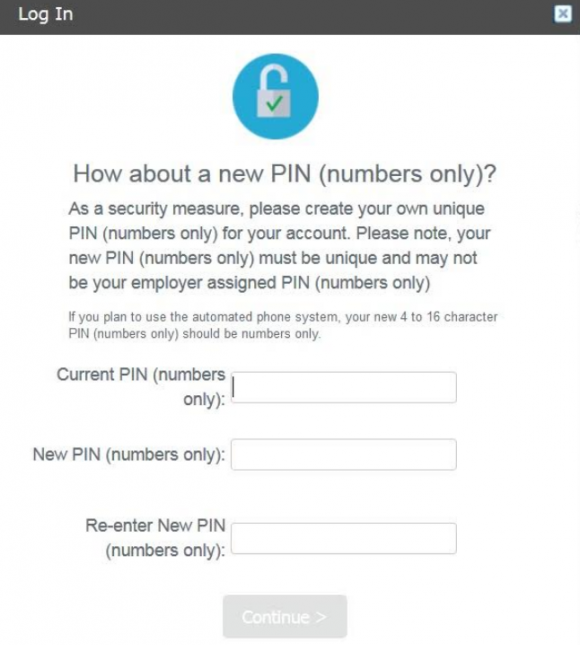
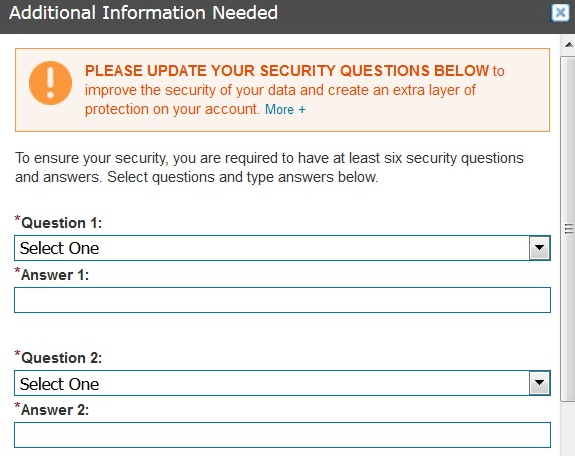
Once you’re successfully “authenticated,” the system asks you to change your PIN to something more secret than your birthday. When the default PIN is changed, The Work Number prompts users to select a series of six challenge/response questions, which Equifax claims will “improve the security of your data and create an extra layer of protection on your account.”
Unfortunately, consumers whose employee history is stored by this service effectively have no privacy or security unless they possess both the awareness that this service exists and the forethought to access their account online before identity thieves or others do it first.
The Work Number does allow employers to opt for TALX’s “enhanced authentication” feature, wherein after logging in with your employer ID and PIN (often the last four digits of an SSN plus the birth year), the system is designed to require the requester to respond to an email at a work address or a phone call to a work number to validate the login.
However, I did not find this to be the case in several instances involving readers whose employers supposedly used this enhanced authentication method. In cases where corporate human resources departments fail to populate employee email addresses and phone numbers, the system defaults to asking visitors to enter any email address and phone number to complete the validation. This is detailed here (PDF), wherein The Work Number states “if you do not have the required phone and e-mail information on file, you will be prompted to update/add your phone numbers/email addresses.”
Worse yet, while companies that use this service tend to vary their approaches to what’s required in terms of user IDs and PINs, a great many employers publish online detailed instructions on how to fill out these various forms. For example, the State of California‘s process is listed here (PDF); instructions for the Health Resources & Services Administration (HRSA) are here; employees at the National Institutes of Health (NIH) can learn the steps by consulting this document (PDF). The process for getting this information on current and former UCLA employees is spelled out here. There are countless other examples that are easy to find with a simple Internet search.
Many readers probably consider their current and former salaries to be very private information, but as we can see this data is easily available on a broad spectrum of the working population in America today. The information needed to obtain it has been widely compromised in thousands of data breaches over the past few years, and the SSN and DOB on most Americans is for sale in a variety of places online. In short, if you can get these details from Equifax’s online service, so can anyone else.
Fortunately, you can reduce the likelihood that an acquaintance, co-worker, stalker or anyone else can do this by claiming your own account, changing the PIN and selecting a half-dozen security questions and answers. As always, it’s best not to answer these questions truthfully, but to input answers that only you will know and that can’t be found using social networking sites or other public data sources.
I could see this service potentially helping to create a toxic workplace environment because it offers a relatively simple method for employees to glean data about the salaries of their co-workers and bosses. While some people believe that companies should be more transparent about employee salaries, this data in the wrong hands very often generates a great deal of resentment and hostility among co-workers.
Employers who use The Work Number should strongly consider changing as many defaults as possible, and truly implementing the service’s enhanced authentication features.
October is National Cybersecurity Awareness Month, and as such KrebsOnSecurity will continue pointing readers to similar services that let anyone access your personal data armed with little more than static identifiers about you that should no longer be considered private. Although some readers may take issue with my pointing these out — reasoning that I’m only making it easier for bad people to do bad things — it’s important to understand that knowledge is half the battle: Planting your flag before someone else does is usually the only way to keep others from abusing such services to expose your personal information.
Related reading:
–USPS ‘Informed Delivery’ is Stalker’s Dream
–Student Aid Tool Held Key for Tax Fraudsters
–Sign Up at IRS.gov Before Crooks Do It For You
–Crooks Hijack Retirement Funds via SSA Portal
–Social Security Administration Now Requires Two-Factor Authentication
–SSA: Ixnay on txt msg reqmnt 4 e-acct, sry
Tags: Equifax, National Cybersecurity Awareness Month, TALX, The Work Number
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






