Carding Kingpin Sentenced Again. Yahoo Hacker Pleads Guilty
Roman Seleznev, a Russian man who is already serving a record 27-year sentence in the United States for cybercrime charges, was handed a 14-year sentence this week by a federal judge in Atlanta for his role in a credit card and identity theft conspiracy that prosecutors say netted more than $50 million. Separately, a Canadian national has pleaded guilty to charges of helping to steal more than a billion user account credentials from Yahoo.
Seleznev, 33, was given the 14-year sentence in connection with two prosecutions that were consolidated in Georgia: The 2008 heist against Atlanta-based credit card processor RBS Worldpay; and a case out of Nevada where he was charged as a leading merchant of stolen credit cards at carder[dot]su, at one time perhaps the most bustling fraud forum where members openly marketed a variety of cybercrime-oriented services.

Roman Seleznev, pictured with bundles of cash. Image: US DOJ.
Seleznev’s conviction comes more than a year after he was convicted in a Seattle court on 38 counts of cybercrime charges, including wire fraud and aggravated identity theft. The Seattle conviction earned Seleznev a 27-year prison sentence — the most jail time ever given to an individual convicted of cybercrime charges in the United States.
This latest sentence will be served concurrently — meaning it will not add any time to his 27-year sentence. But it’s worth noting because Seleznev is appealing the Seattle verdict. In the event he prevails in Seattle and gets that conviction overturned, he will still serve out his 14-year sentence in the Georgia case because he pleaded guilty to those charges and waived his right to an appeal.
Prosecutors say Seleznev, known in the underworld by his hacker nicknames “nCux” and “Bulba,” enjoyed an extravagant lifestyle prior to his arrest, driving expensive sports cars and dropping tens of thousands of dollars at lavish island vacation spots. The son of an influential Russian politician, Seleznev made international headlines in 2014 after he was captured while vacationing in The Maldives, a popular destination for Russians and one that many Russian cybercriminals previously considered to be out of reach for western law enforcement agencies.
However, U.S. authorities were able to negotiate a secret deal with the Maldivian government to apprehend Seleznev. Following his capture, Seleznev was whisked away to Guam for more than a month before being transported to Washington state to stand trial for computer hacking charges.
The U.S. Justice Department says the laptop found with him when he was arrested contained more than 1.7 million stolen credit card numbers, and that evidence presented at trial showed that Seleznev earned tens of millions of dollars defrauding more than 3,400 financial institutions.
Investigators also reportedly found a smoking gun: a password cheat sheet that linked Seleznev to a decade’s worth of criminal hacking. For more on Seleznev’s arrest and prosecution, see The Backstory Behind Carder Kingpin Roman Seleznev’s Record 27-Year Sentence, and Feds Charge Carding Kingpin in Retail Hacks.
In an unrelated case, federal prosecutors in California announced a guilty plea from Karim Baratov, one of four men indicted in March 2017 for hacking into Yahoo beginning in 2014. Yahoo initially said the intrusion exposed the usernames, passwords and account data for roughly 500 million Yahoo users, but in December 2016 Yahoo said the actual number of victims was closer to one billion (read: all of its users).
Baratov, 22, is a Canadian and Kazakh national who lived in Canada (he’s now being held in California). He was charged with being hired by two Russian FSB officer defendants in this case — Dmitry Dokuchaev, 33, and Igor Sushchin, 43 — to hack into the email accounts of thousands of individuals. According to prosecutors, Baratov’s role in the charged conspiracy was to hack webmail accounts of individuals of interest to the FSB and send those accounts’ passwords to Dokuchaev in exchange for money.
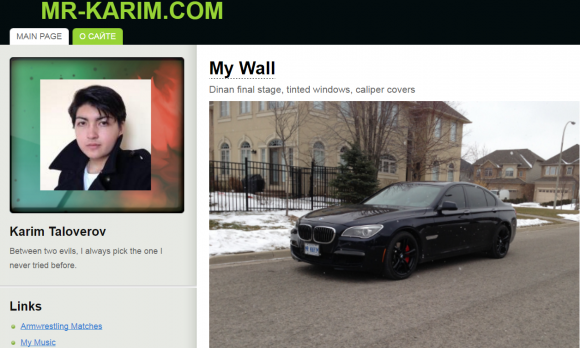
Karim Baratov, a.k.a. “Karim Taloverov,” as pictured in 2014 on his own site, mr-karim.com.
Baratov operated several business that he advertised openly online that could be hired to hack into email accounts at the world’s largest email providers, including Google, Yahoo and Yandex. As part of his plea agreement, Baratov not only admitted to agreeing and attempting to hack at least 80 webmail accounts on behalf of one of his FSB co-conspirators, but also to hacking more than 11,000 webmail accounts in total from in or around 2010 until his arrest by Canadian authorities.
Shortly after Baratov’s arrest and indictment, KrebsOnSecurity examined many of the email hacking services he operated and that were quite clearly tied to his name. One such business advertised the ability to steal email account passwords without actually changing the victim’s password. According to prosecutors, Baratov’s service relied on “spear phishing” emails that targeted individuals with custom content and enticed recipients to click a booby-trapped link.
For example, one popular email hacking business registered to Baratov was xssmail[dot]com, which for several years advertised the ability to break into email accounts of virtually all of the major Webmail providers. XSS is short for “cross-site-scripting.” XSS attacks rely on vulnerabilities in Web sites that don’t properly parse data submitted by visitors in things like search forms or anyplace one might enter data on a Web site.
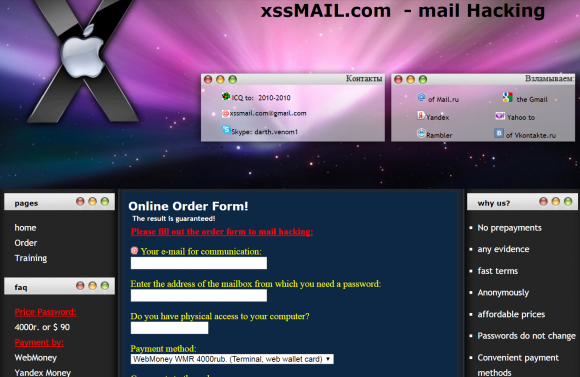
Archive.org’s cache of xssmail.com
In the context of phishing links, the user clicks the link and is actually taken to the domain he or she thinks she is visiting (e.g., yahoo.com) but the vulnerability allows the attacker to inject malicious code into the page that the victim is visiting.
This can include fake login prompts that send any data the victim submits directly to the attacker. Alternatively, it could allow the attacker to steal “cookies,” text files that many sites place on visitors’ computers to validate whether they have visited the site previously, as well as if they have authenticated to the site already.
Baratov pleaded guilty to nine counts, including one count of aggravated identity theft and eight violations of the Computer Fraud and Abuse Act. His sentencing hearing is scheduled for Feb. 20, 2018. The aggravated identity theft charge carries a mandatory two-year sentence; each of the other counts is punishable by up to 10 years in jail and fines of $250,000, although any sentence he receives will likely be heavily tempered by U.S. federal sentencing guidelines.
Meanwhile, Baratov’s co-defendant Dokuchaev is embroiled in his own legal worries in Russia, charges that could carry a death sentence. He and his former boss Sergei Mikhailov — once deputy chief of the FSB’s Center for Information Security — were arrested in December 2016 by Russian authorities and charged with treason. Also charged with treason in connection with that case was Ruslan Stoyanov, a senior employee at Russian security firm Kaspersky Lab.
There are many competing theories for the reasons behind their treason charges, some of which are explored in this Washington Post story. I have my own theory, detailed in my January 2017 piece, A Shakeup in Russia’s Top Cybercrime Unit.
Tags: bulba, Dmitry Dokuchaev, Karim Baratov, Karim Taloverov, Kaspersky Lab, nCux, RBS Worldpay hack, Roman Seleznev, Ruslan Stoyanov, Sergei Mikhailov, Yahoo hack
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






