Bomb Threat, DDoS Purveyor Gets Eight Years
A 22-year-old North Carolina man has been sentenced to nearly eight years in prison for conducting bomb threats against thousands of schools in the U.S. and United Kingdom, running a service that launched distributed denial-of-service (DDoS) attacks, and for possessing sexually explicit images of minors.
Timothy Dalton Vaughn from Winston-Salem, N.C. was a key member of the Apophis Squad, a gang of young ne’er-do-wells who made bomb threats to more than 2,400 schools and launched DDoS attacks against countless Web sites — including KrebsOnSecurity on multiple occasions.
The Justice Department says Vaughn and his gang ran a DDoS-for-hire service that they used to shake down victims.
“In early 2018, Vaughn demanded 1.5 bitcoin (then worth approximately $20,000) from a Long Beach company, to prevent denial-of-service attacks on its website,” reads a statement from Nicola Hanna, U.S. attorney for the Central District of California. “When the company refused to pay, he launched a DDoS attack that disabled the company’s website.”
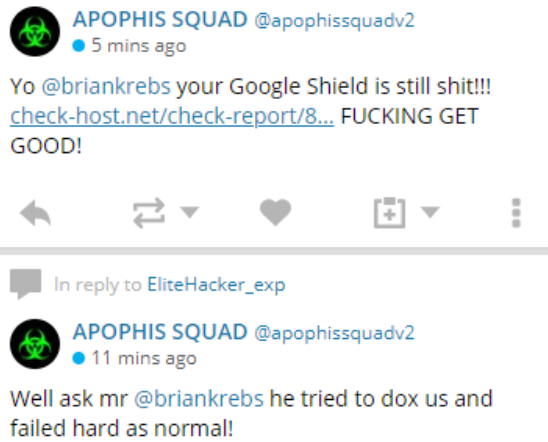
One of many tweets from the attention-starved Apophis Squad, which launched multiple DDoS attacks against KrebsOnSecurity over the past few months.
Dalton, whose online aliases included “WantedbyFeds” and “Hacker_R_US,” pleaded guilty last year to one count of conspiracy to convey threats to injure, convey false information concerning use of explosive device, and intentionally damage a computer; one count of computer hacking; and one count of possession of child pornography.
Federal judge Otis D. Wright II sentenced Vaughn to 95 months for possessing 200 sexually explicit images and videos depicting children, including at least one toddler, the Justice Department said. Vaughn was sentenced to 60 months in federal prison for the remaining charge. The sentences will be served concurrently.
As KrebsOnSecurity noted in 2019, Vaughn’s identity was revealed by following the trail of clues from a gaming website he used that later got hacked.
Vaughn used multiple aliases on Twitter and elsewhere to crow about his attacks, including “HDGZero,” “WantedByFeds,” and “Xavier Farbel.” Among the Apophis Squad’s targets was encrypted mail service Protonmail, which reached out to this author in 2018 for clues about the identities of the Apophis Squad members after noticing we were both being targeted by them and receiving demands for money in exchange for calling off the attacks.
Protonmail later publicly thanked KrebsOnSecurity for helping to bring about the arrest of Apophis Squad leader George Duke-Cohan — a.k.a. “opt1cz,” “7R1D3n7,” and “Pl3xl3t,” — a 19-year-old from the United Kingdom who was convicted in December 2018 and sentenced to three years in prison. But the real-life identity of HDGZero remained a mystery to both of us, as there was little publicly available information at the time connecting that moniker to anyone.
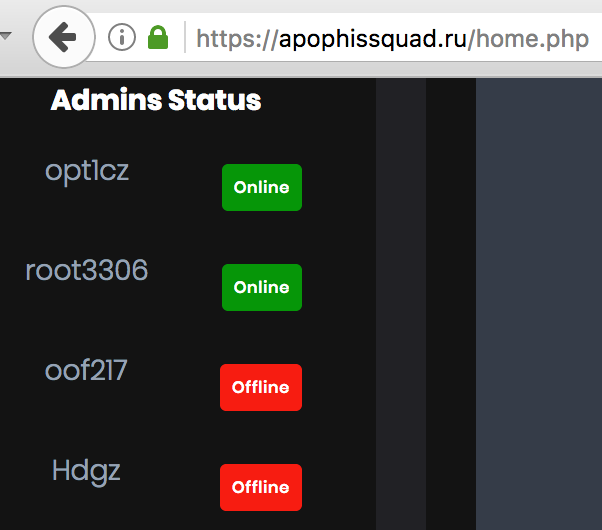
The DDoS-for-hire service run by Apophis Squad listed their members.
That is, until early January 2019, when news broke that hackers had broken into the servers of computer game maker BlankMediaGames and made off with account details of some 7.6 million people who had signed up to play “Town of Salem,” a browser-based role playing game. That stolen information has since been posted and resold in underground forums.
A review of the leaked BlankMediaGames user database shows that in late 2018, someone who selected the username “hdgzero” signed up to play Town of Salem, registering with the email address
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






