Arrests in $400M SIM-Swap Tied to Heist at FTX?
Three Americans were charged this week with stealing more than $400 million in a November 2022 SIM-swapping attack. The U.S. government did not name the victim organization, but there is every indication that the money was stolen from the now-defunct cryptocurrency exchange FTX, which had just filed for bankruptcy on that same day.
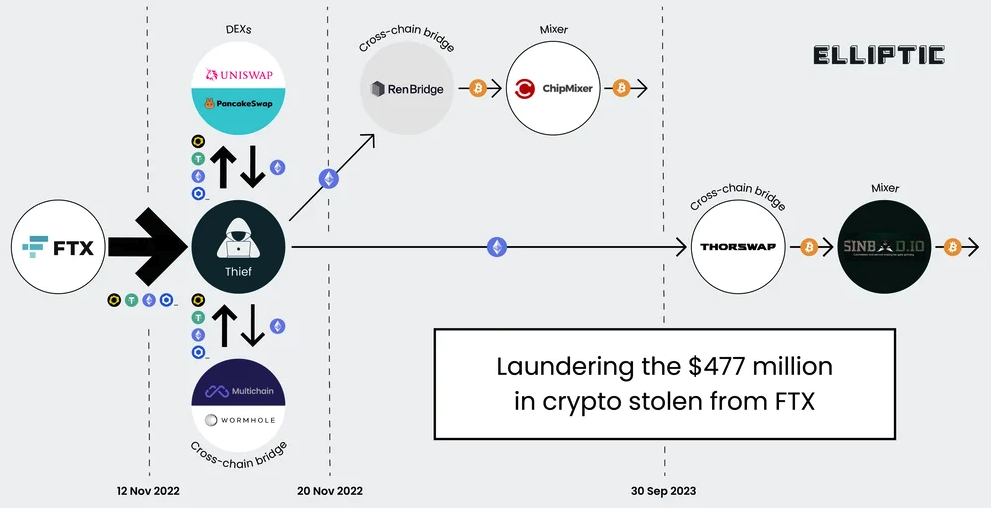
A graphic illustrating the flow of more than $400 million in cryptocurrencies stolen from FTX on Nov. 11-12, 2022. Image: Elliptic.co.
An indictment unsealed this week and first reported on by Ars Technica alleges that Chicago man Robert Powell, a.k.a. “R,” “R$” and “ElSwapo1,” was the ringleader of a SIM-swapping group called the “Powell SIM Swapping Crew.” Colorado resident Emily “Em” Hernandez allegedly helped the group gain access to victim devices in service of SIM-swapping attacks between March 2021 and April 2023. Indiana resident Carter Rohn, a.k.a. “Carti,” and “Punslayer,” allegedly assisted in compromising devices.
In a SIM-swapping attack, the crooks transfer the target’s phone number to a device they control, allowing them to intercept any text messages or phone calls sent to the victim, including one-time passcodes for authentication or password reset links sent via SMS.
The indictment states that the perpetrators in this heist stole the $400 million in cryptocurrencies on Nov. 11, 2022 after they SIM-swapped an AT&T customer by impersonating them at a retail store using a fake ID. However, the document refers to the victim in this case only by the name “Victim 1.”
Wired’s Andy Greenberg recently wrote about FTX’s all-night race to stop a $1 billion crypto heist that occurred on the evening of November 11:
“FTX’s staff had already endured one of the worst days in the company’s short life. What had recently been one of the world’s top cryptocurrency exchanges, valued at $32 billion only 10 months earlier, had just declared bankruptcy. Executives had, after an extended struggle, persuaded the company’s CEO, Sam Bankman-Fried, to hand over the reins to John Ray III, a new chief executive now tasked with shepherding the company through a nightmarish thicket of debts, many of which it seemed to have no means to pay.”
“FTX had, it seemed, hit rock bottom. Until someone—a thief or thieves who have yet to be identified—chose that particular moment to make things far worse. That Friday evening, exhausted FTX staffers began to see mysterious outflows of the company’s cryptocurrency, publicly captured on the Etherscan website that tracks the Ethereum blockchain, representing hundreds of millions of dollars worth of crypto being stolen in real time.”
The indictment says the $400 million was stolen over several hours between November 11 and 12, 2022. Tom Robinson, co-founder of the blockchain intelligence firm Elliptic, said the attackers in the FTX heist began to drain FTX wallets on the evening of Nov. 11, 2022 local time, and continuing until the 12th of November.
Robinson said Elliptic is not aware of any other crypto heists of that magnitude occurring on that date.
“We put the value of the cryptoassets stolen at $477 million,” Robinson said. “The FTX administrators have reported overall losses due to “unauthorized third-party transfers” of $413 million – the discrepancy is likely due to subsequent seizure and return of some of the stolen assets. Either way, it’s certainly over $400 million, and we are not aware of any other thefts from crypto exchanges on this scale, on this date.”
The SIM-swappers allegedly responsible for the $400 million crypto theft are all U.S. residents. But there are some indications they had help from organized cybercriminals based in Russia. In October 2023, Elliptic released a report that found the money stolen from FTX had been laundered through exchanges with ties to criminal groups based in Russia.
“A Russia-linked actor seems a stronger possibility,” Elliptic wrote. “Of the stolen assets that can be traced through ChipMixer, significant amounts are combined with funds from Russia-linked criminal groups, including ransomware gangs and darknet markets, before being sent to exchanges. This points to the involvement of a broker or other intermediary with a nexus in Russia.”
Nick Bax, director of analytics at the cryptocurrency wallet recovery firm Unciphered, said the flow of stolen FTX funds looks more like what his team has seen from groups based in Eastern Europe and Russian than anything they’ve witnessed from US-based SIM-swappers.
“I was a bit surprised by this development but it seems to be consistent with reports from CISA [the Cybersecurity and Infrastructure Security Agency] and others that “Scattered Spider” has worked with [ransomware] groups like ALPHV/BlackCat,” Bax said.
CISA’s alert on Scattered Spider says they are a cybercriminal group that targets large companies and their contracted information technology (IT) help desks.
“Scattered Spider threat actors, per trusted third parties, have typically engaged in data theft for extortion and have also been known to utilize BlackCat/ALPHV ransomware alongside their usual TTPs,” CISA said, referring to the group’s signature “Tactics, Techniques an Procedures.”
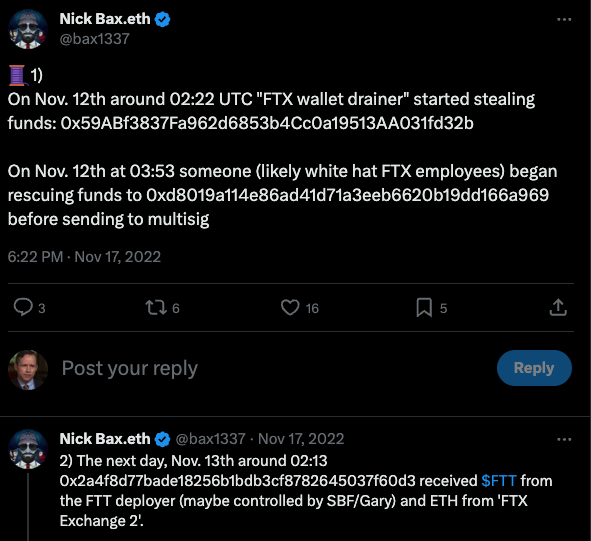
Nick Bax, posting on Twitter/X in Nov 2022 about his research on the $400 million FTX heist.
Earlier this week, KrebsOnSecurity published a story noting that a Florida man recently charged with being part of a SIM-swapping conspiracy is thought to be a key member of Scattered Spider, a hacking group also known as 0ktapus. That group has been blamed for a string of cyber intrusions at major U.S. technology companies during the summer of 2022.
Financial claims involving FTX’s bankruptcy proceedings are being handled by the financial and risk consulting giant Kroll. In August 2023, Kroll suffered its own breach after a Kroll employee was SIM-swapped. According to Kroll, the thieves stole user information for multiple cryptocurrency platforms that rely on Kroll services to handle bankruptcy proceedings.
KrebsOnSecurity sought comment for this story from Kroll, the FBI, the prosecuting attorneys, and Sullivan & Cromwell, the law firm handling the FTX bankruptcy. This story will be updated in the event any of them respond.
Attorneys for Mr. Powell said they do not know who Victim 1 is in the indictment, as the government hasn’t shared that information yet. Powell’s next court date is a detention hearing on Feb. 2, 2024.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






