Akamai on the Record KrebsOnSecurity Attack
Internet infrastructure giant Akamai last week released a special State of the Internet report. Normally, the quarterly accounting of noteworthy changes in distributed denial-of-service (DDoS) attacks doesn’t delve into attacks on specific customers. But this latest Akamai report makes an exception in describing in great detail the record-sized attack against KrebsOnSecurity.com in September, the largest such assault it has ever mitigated.
“The attacks made international headlines and were also covered in depth by Brian Krebs himself,” Akamai said in its report, explaining one reason for the exception. “The same data we’ve shared here was made available to Krebs for his own reporting and we received permission to name him and his site in this report. Brian Krebs is a security blogger and reporter who does in-depth research and analysis of cybercrime throughout the world, with a recent emphasis on DDoS. His reporting exposed a stressor site called vDOS and the security firm BackConnect Inc., which made him the target of a series of large DDoS attacks starting September 15, 2016.”
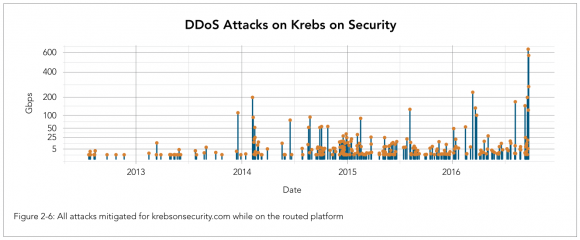
A visual depiction of the increasing size and frequency of DDoS attacks against KrebsOnSecurity.com, between 2012 and 2016. Source: Akamai.
Akamai said so-called “booter” or “stresser” DDoS-for-hire services that sell attacks capable of knocking Web sites offline continue to account for a large portion of the attack traffic in mega attacks. According to Akamai, most of the traffic from those mega attacks in Q3 2016 were thanks to Mirai — the now open-source malware family that was used to coordinate the attack on this site in September and a separate assault against infrastructure provider Dyn in October.
Akamai said the attack on Sept. 20 was launched by just 24,000 systems infected with Mirai, mostly hacked Internet of Things (IoT) devices such as digital video recorders and security cameras.
“The first quarter of 2016 marked a high point in the number of attacks peaking at more than 100 Gbps,” Akamai stated in its report. “This trend was matched in Q3 2016, with another 19 mega attacks. It’s interesting that while the overall number of attacks fell by 8% quarter over quarter, the number of large attacks, as well as the size of the biggest attacks, grew significantly.”
As detailed here in several previous posts, KrebsOnSecurity.com was a pro-bono customer of Akamai, beginning in August 2012 with Prolexic before Akamai acquired them. Akamai mentions this as well in explaining its decision to terminate our pro-bono arrangement. KrebsOnSecurity is now behind Google‘s Project Shield, a free program run by Google to help protect journalists and dissidents from online censorship.
“Almost as soon as the site was on the Prolexic network, it was hit by a trio of attacks based on the Dirt Jumper DDoS tookit,” Akamai wrote of this site. “Those attacks marked the start of hundreds of attacks that were mitigated on the routed platform.”
In total, Akamai found, this site received 269 attacks in the little more than four years it was on the Prolexic/Akamai network.
“During that time, there were a dozen mega attacks peaking at over 100 Gbps,” the company wrote. “The first happened in December 2013, the second in February 2014, and the third in August 2015. In 2016, the size of attacks accelerated dramatically, with four mega attacks happening between March and August, while five attacks occurred in September, ranging from 123 to 623 Gbps. An observant reader can probably correlate clumps of attacks to specific stories covered by Krebs. Reporting on the dark side of cybersecurity draws attention from people and organizations who are not afraid of using DDoS attacks to silence their detractors.”
In case any trenchant observant readers wish to attempt that, I’ve published a spreadsheet here (in .CSV format) which lists the date, duration, size and type of attack used in DDoS campaigns against KrebsOnSecurity.com over the past four years. Although 269 attacks over four years works out to an average of just one attack roughly every five days, both the frequency and intensity of these attacks have increased substantially over the past four years as illustrated by the graphic above.
“The magnitude of the attacks seen during the final week were significantly larger than the majority of attacks Akamai sees on a regular basis,” Akamai reports. “In fact, while the attack on September 20 was the largest attack ever mitigated by Akamai, the attack on September 22 would have qualified for the record at any other time, peaking at 555 Gbps.”
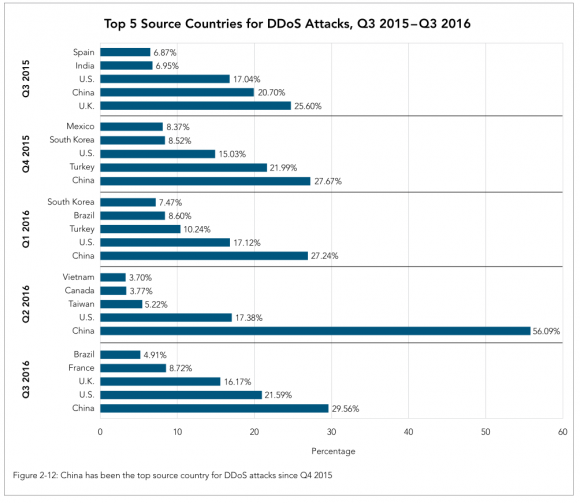
Akamai found that the 3rd quarter of 2016 marks a full year with China as the top source country for DDoS attacks, with just under 30 percent of attack traffic in Q3 2016. The company notes that this metric doesn’t count UDP-based attacks – such as amplification and reflection attacks — due to the ease with which the sources of the attacks can be spoofed and could create significant distortion of the data.
“More importantly, the proportion of traffic from China has been reduced by 56%, which had a significant effect on the overall attack count and led to the 8% drop in attacks seen this quarter,” Akamai reported. The U.S., U.K., France, and Brazil round out the remaining top five source countries.”
A copy of Akamai’s Q3 2016 State of the Internet report is available here.
Tags: Akamai, BackConnect, google, internet of things, mirai, Project Shield, Prolexic, State of the Internet report 2016, vDos
This entry was posted on Tuesday, November 22nd, 2016 at 11:06 am and is filed under Other. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.