Accused ‘Raccoon’ Malware Developer Fled Ukraine After Russian Invasion
A 26-year-old Ukrainian man is awaiting extradition from The Netherlands to the United States on charges that he acted as a core developer for Raccoon, a popular “malware-as-a-service” offering that helped paying customers steal passwords and financial data from millions of cybercrime victims. KrebsOnSecurity has learned that the defendant was busted in March 2022, after fleeing mandatory military service in Ukraine in the weeks following the Russian invasion.

Ukrainian national Mark Sokolovsky, seen here in a Porsche Cayenne on Mar. 18 fleeing mandatory military service in Ukraine. This image was taken by Polish border authorities as Sokolovsky’s vehicle entered Germany. Image: KrebsOnSecurity.com.
The U.S. Attorney for the Western District of Texas unsealed an indictment last week that named Mark Sokolvsky as the core developer for the Raccoon Infostealer business, which was marketed on several Russian-language cybercrime forums beginning in 2019.
Raccoon was essentially a Web-based control panel, where — for $200 a month — customers could get the latest version of the Raccoon Infostealer malware, and interact with infected systems in real time. Security experts say the passwords and other data stolen by Raccoon malware were often resold to groups engaged in deploying ransomware.
Working with investigators in Italy and The Netherlands, U.S. authorities seized a copy of the server used by Raccoon to help customers manage their botnets. According to the U.S. Justice Department, FBI agents have identified more than 50 million unique credentials and forms of identification (email addresses, bank accounts, cryptocurrency addresses, credit card numbers, etc.) stolen with the help of Raccoon.
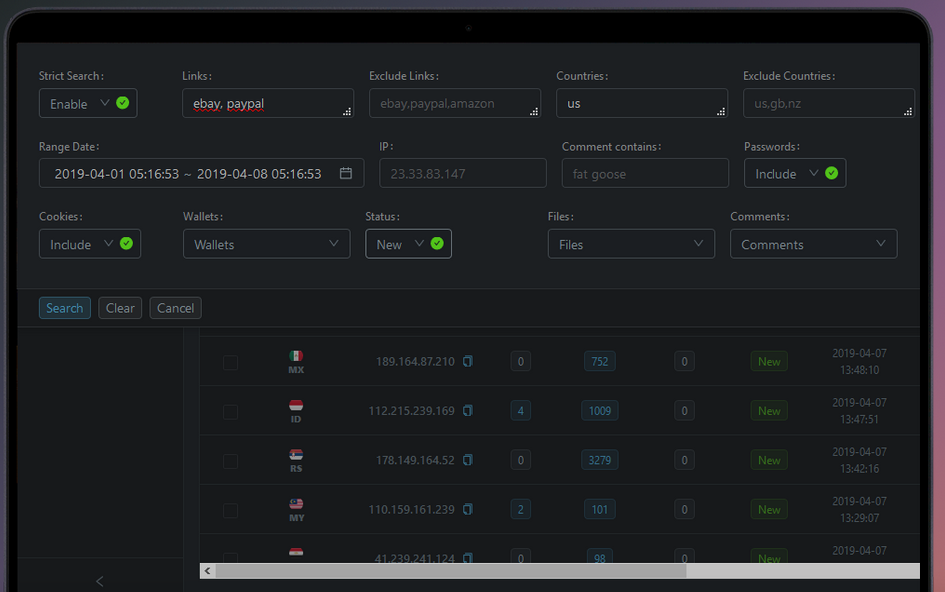
The Raccoon v. 1 web panel, where customers could search by infected IP, and stolen cookies, wallets, domains and passwords.
The unsealed indictment (PDF) doesn’t delve much into how investigators tied Sokolovsky to Raccoon, but two sources close to the investigation shared more information about that process on condition of anonymity because they were not authorized to discuss the case publicly.
According to those sources, U.S. authorities zeroed in on an operational security mistake that the Raccoon developer made early on in his posts to the crime forums, connecting a Gmail account for a cybercrime forum identity used by the Raccoon developer (“Photix”) to an Apple iCloud account belonging to Sokolovsky. For example, the indictment includes a photo that investigators subpoenaed from Sokolovsky’s iCloud account that shows him posing with several stacks of bundled cash.

A selfie pulled from Mark Sokolovsky’s iCloud account. Image: USDOJ.
When Russian President Vladimir Putin invaded Ukraine in late February 2022, Sokolovsky was living in Kharkiv, a city in northeast Ukraine that would soon come under heavy artillery bombardment from Russian forces. Authorities monitoring Sokolovsky’s iCloud account had spent weeks watching him shuttle between Kharkiv and the Ukrainian capital Kyiv, but on Mar. 18, 2022, his phone suddenly showed up in Poland.
Investigators learned from Polish border guards that Sokolovsky had fled Ukraine in a Porsche Cayenne along with a young blond woman, leaving his mother and other family behind. The image at the top of this post was shared with U.S. investigators by Polish border security officials, and it shows Sokolovsky leaving Poland for Germany on Mar. 18.
At the time, all able-bodied men of military age were required to report for service to help repel the Russian invasion, and it would have been illegal for Sokolovsky to leave Ukraine without permission. But both sources said investigators believe Sokolovsky bribed border guards to let them pass.
Authorities soon tracked Sokolvsky’s phone through Germany and eventually to The Netherlands, with his female companion helpfully documenting every step of the trip on her Instagram account. Here is a picture she posted of the two embracing upon their arrival in Amsterdam’s Dam Square:

Authorities in The Netherlands arrested Sokolovsky on Mar. 20, and quickly seized control over the Raccoon Infostealer infrastructure. Meanwhile, on March 25 the accounts that had previously advertised the Raccoon Stealer malware on cybercrime forums announced the service was closing down. The parting message to customers said nothing of an arrest, and instead insinuated that the core members in charge of the malware-as-a-service project had perished in the Russian invasion.
“Unfortunately, due to the ‘special operation,’ we will have to close our Raccoon Stealer project,” the team announced Mar. 25. “Our team members who were responsible for critical components of the product are no longer with us. Thank you for this experience and time, for every day, unfortunately everything, sooner or later, the end of the WORLD comes to everyone.”
Sokolovsky’s extradition to the United States has been granted, but he is appealing that decision. He faces one count of conspiracy to commit computer fraud; one count of conspiracy to commit wire fraud; one count of conspiracy to commit money laundering, and one count of aggravated identity theft.
Sources tell KrebsOnSecurity that Sokolovsky has been consulting with Houston, Tx.-based attorney F. Andino Reynal, the same lawyer who represented Alex Jones in the recent defamation lawsuit against Jones and his conspiracy theory website Infowars. Reynal was responsible for what Jones himself referred to as the “Perry Mason” moment of the trial, wherein the plaintiff’s lawyer revealed that Reynal had inadvertently given them an entire digital copy of Jones’s cell phone. Mr. Reynal did not respond to requests for comment.
If convicted, Sokolovsky faces a maximum penalty of 20 years in prison for the wire fraud and money laundering offenses, five years for the conspiracy to commit computer fraud charge, and a mandatory consecutive two-year term for the aggravated identity theft offense.
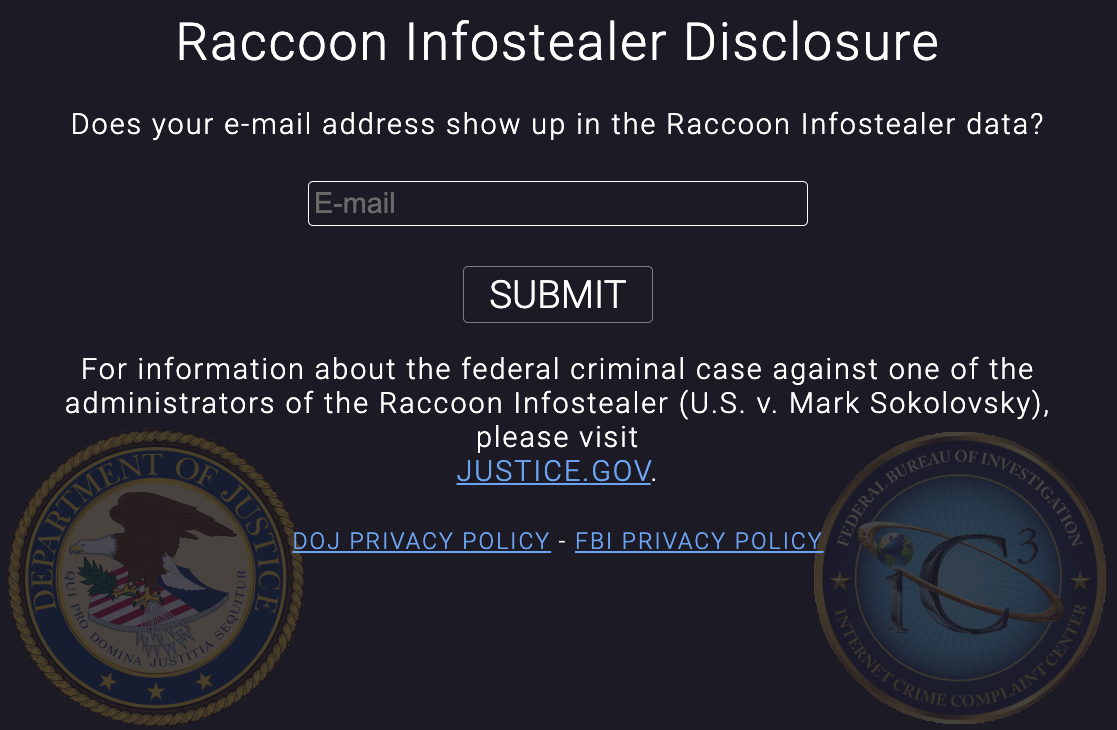
The Justice Department has set up a website — raccoon.ic3.gov — that allows visitors to check whether their email address shows up in the data collected by the Raccoon Stealer service.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.






