2nd Breach at Verticalscope Impacts 25M
For the second time in as many years, hackers have compromised Verticalscope.com, a Canadian company that manages hundreds of popular Web discussion forums totaling more than 45 million user accounts. Evidence of the breach was discovered just before someone began using that illicit access as a commercial for a new paid search service that indexes consumer information exposed in corporate data breaches.
Toronto-based Verticalscope runs a network of sites that cater to automotive, pets, sports and technology markets. Verticalscope acknowledged in June 2016 that a hacking incident led to the siphoning of 45 million user accounts. Now, it appears the company may have been hit again, this time in a breach involving at least 25 million user accounts.
On Thursday, KrebsOnSecurity was contacted by Alex Holden, a security researcher and founder of Hold Security. Holden saw evidence of hackers selling access to Verticalscope.com and to a host of other sites operated by the company.
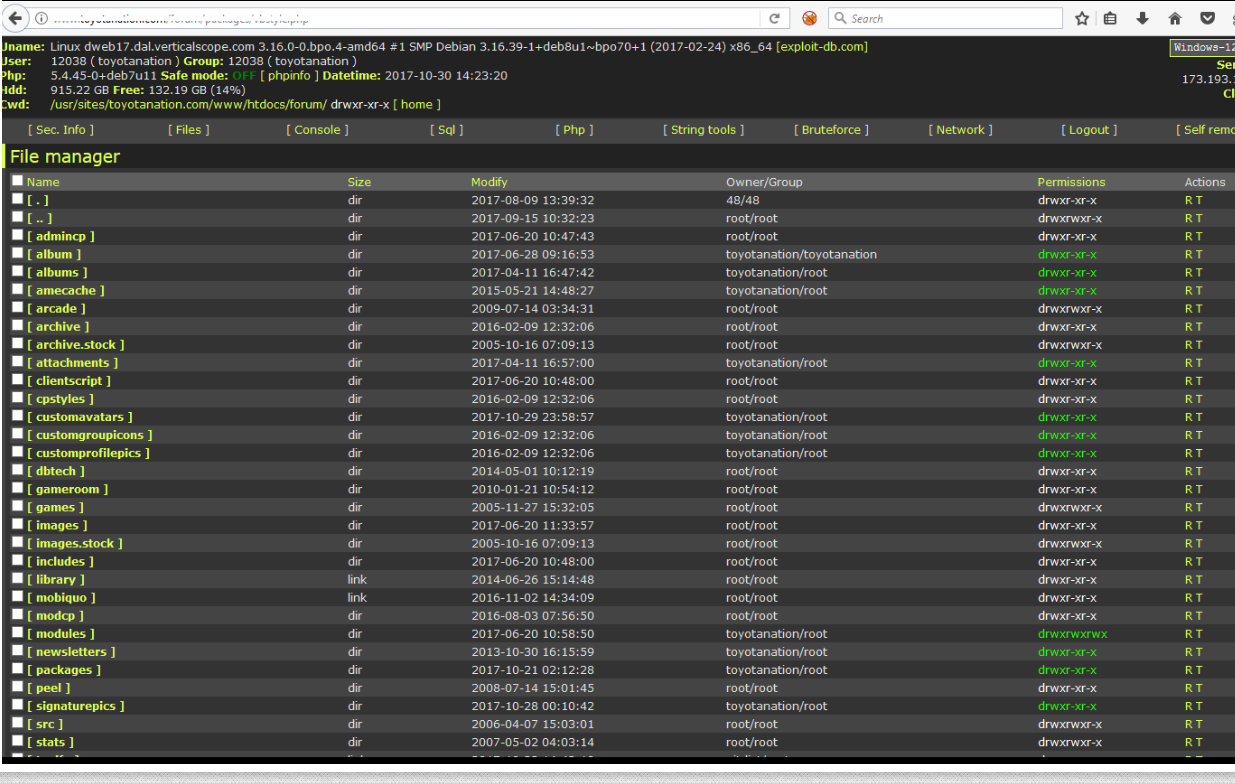
Holden said at first he suspected someone was merely trying to resell data stolen in the 2016 breach. But that was before he contacted one of the hackers selling the data and was given screen shots indicating that Verticalscope.com and several other properties were in fact compromised with a backdoor known as a “Web shell.”
With a Web shell installed on a site, anyone can remotely administer the site, upload and delete content at will, or dump entire databases of information — such as usernames, passwords, email addresses and Internet addresses associated with each account.
Holden said the intruders obfuscated certain details in the screenshots that gave away exactly where the Web shells were hidden on Verticalscope.com, but that they forgot to blur out a few critical details — allowing him to locate at least two backdoors on Veriticalscope’s Web site. He also was able to do the same with a second screen shot the hackers shared which showed a similar backdoor shell on Toyotanation.com, one of Verticalscope’s most-visited forums.
Reached for comment about the claims, Verticalscope said the company had detected an intrusion on six of its Web sites, including Toyotanation.com.
“The intrusion granted access to each individual website files,” reads a statement shared Verticalscope. “Out of an abundance of caution, we have removed the file manager, expired all passwords on the 6 websites in question, added the malicious file pattern and attack vector to our detection tools, and taken additional steps to lock down access.”
Verticalscope said the other forums impacted included Jeepforum.com — the company’s second most-popular site with 9.3 million users; and watchuseek.com, a forum for wristwatch enthusiast which claims more than 12 million users.
Verticalscope admitted a breach in 2016 after their forum users’ data was outed in a blog post on Leakedsource.com, a now-defunct service that sold access to username and password details stolen in some of history’s largest data breaches.
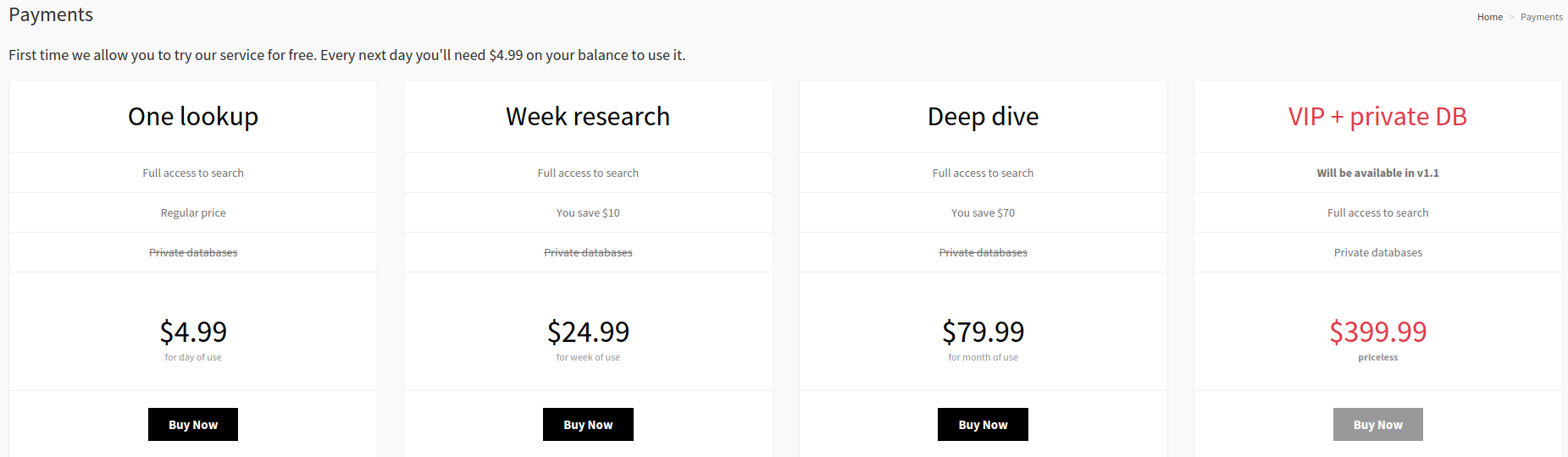
An Internet search on one of the compromised Verticalscope domains leads to a series of now-deleted Pastebin posts suggesting that the individual(s) responsible for this hack may be trying to use it to advertise a legally dicey new online service called LuiDB.
Similar to Leakedsource, LuiDB allows registered users to search for account details associated with any data element compromised in a breach — such as login, password, email, first/last name and Internet address. The first search is free, but viewing results requires purchasing a subscription for between $5 and $400 in Bitcoin.
People who re-use passwords across multiple Web sites tend to be those hardest-hit by these breaches, and by these dodgy password lookup services. It may not seem like a big deal if someone chooses to re-use the same password across a range of sites that don’t ask for or store your personal data, such as discussion forums. The problem is that this encourages poor password habits, and for many folks this eventually results in using that forum password at more important sites that do store sensitive data.
In practice, there’s no reason people should ever re-use the same password. Password managers can help users pick and remember unique, strong passwords for all sites that require a login; all the user needs to do is remember a single “master password” to unlock all the others. Old schoolers like Yours Truly tend to stick to local password managers like Keepass (or even PwdSafe), although many folks I admire in the security industry rely heavily on cloud-based password managers like LastPass and Dashlane.
While few online discussion forums offer two-factor or multi-factor authentication (requiring you to log in using a password and a one-time code, e.g.), a great many services do offer this very effective security measure. Check out twofactorauth.org to see if there are online services you use that could be furthered hardened by turning on two-factor authentication.
Tags: alex holden, Hold Security, Holdsecurity.com, LeakedSource, LuiDB, Toyotanation, verticalscope breach, Verticalscope.com breach, Web Shell
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.