Krebs on Security
VW’s Audi steps up collaboration with Chinese tech groups
September 11, 2016Tesla says new Autopilot would likely have prevented fatality
September 11, 2016http://krebsonsecurity.com In-depth security news and investigation Sat, 10 Sep 2016 19:13:39 +0000 en-US hourly 1 https://wordpress.org/?v=4.4.5 http://krebsonsecurity.com/2016/09/alleged-vdos-proprietors-arrested-in-israel/ http://krebsonsecurity.com/2016/09/alleged-vdos-proprietors-arrested-in-israel/#comments Sat, 10 Sep 2016 19:13:39 +0000
http://krebsonsecurity.com/?p=36288
Two young Israeli men alleged to be the co-owners of a popular online attack-for-hire service were reportedly arrested in Israel on Thursday. The pair were arrested around the same time that KrebsOnSecurity published a story naming them as the masterminds behind a service that can be hired to knock Web sites and Internet users offline with powerful blasts of junk data.

18-year-old Yarden Bidani.
According to a story at Israeli news site TheMarker.com, Itay Huri and Yarden Bidani, both 18 years old, were arrested Thursday in connection with an investigation by the U.S. Federal Bureau of Investigation (FBI).
The pair were reportedly questioned and released Friday on the equivalent of about USD $10,000 bond each. Israeli authorities also seized their passports, placed them under house arrest for 10 days, and forbade them from using the Internet or telecommunications equipment of any kind for 30 days.
Huri and Bidani are suspected of running an attack service called vDOS. As I described in this week’s story, vDOS is a “booter” service that has earned in excess of $600,000 over the past two years helping customers coordinate more than 150,000 so-called distributed denial-of-service (DDoS) attacks designed to knock Web sites offline.
The two men’s identities were exposed because vDOS got massively hacked, spilling secrets about tens of thousands of paying customers and their targets. A copy of that database was obtained by KrebsOnSecurity.
For most of Friday, KrebsOnSecurity came under a heavy and sustained denial-of-service attack, which spiked at almost 140 Gbps. A single message was buried in each attack packet: “godiefaggot.” For a brief time the site was unavailable, but thankfully it is guarded by DDoS protection firm Prolexic/Akamai. The attacks against this site are ongoing.
Huri and Bidani were fairly open about their activities, or at least not terribly careful to cover their tracks. Yarden’s now abandoned Facebook page contains several messages from friends who refer to him by his hacker nickname “AppleJ4ck” and discuss DDoS activities. vDOS’s customer support system was configured to send a text message to Huri’s phone number in Israel — the same phone number that was listed in the Web site registration records for the domain v-email[dot]org, a domain the proprietors used to help manage the site.
At the end of August 2016, Huri and Bidani authored a technical paper (PDF) on DDoS attack methods which was published in the Israeli security e-zine Digital Whisper. In it, Huri signs his real name and says he is 18 years old and about to be drafted into the Israel Defense Forces. Bidani co-authored the paper under the alias “Raziel.b7@gmail.com,” an email address that I pointed out in my previous reporting was assigned to one of the administrators of vDOS.
Sometime on Friday, vDOS went offline. It is currently unreachable. Before it went offline, vDOS was supported by at least four servers hosted in Bulgaria at a provider called Verdina.net (the Internet address of those servers was 82.118.233.144. But according to several automated Twitter feeds that track suspicious large-scale changes to the global Internet routing tables, sometime in the last 24 hours vDOS was apparently the victim of what’s known as a BGP hijack.
BGP hijacking involves one ISP fraudulently “announcing” to the rest of the world’s ISPs that it is in fact the rightful custodian of a range of Internet addresses that it doesn’t actually have the right to control. It is a hack most often associated with spamming activity. According to those Twitter feeds, vDOS’s Internet addresses were hijacked by a firm called BackConnect Security.
Reached by phone, Bryant Townsend, founder and CEO of BackConnect Security, confirmed that his company did in fact hijack Verdina/vDOS’s Internet address space. Townsend said the company took the extreme measure in an effort to get out from under a massive attack launched on the company’s network Thursday, and that the company received an email directly from vDOS claiming credit for the attack.
“For about six hours, we were seeing attacks of more than 200 Gbps hitting us,” Townsend explained. “What we were doing was for defensive purposes. We were simply trying to get them to stop and to gather as much information as possible about the botnet they were using and report that to the proper authorities.”
I noted earlier this week that I would be writing more about the victims of vDOS. That story will have to wait for a few more days, but Friday evening CloudFlare (another DDoS protection service that vDOS was actually hiding behind) agreed to host the rather large log file listing roughly four months of vDOS attack logs from April through July 2016.
For some reason the attack logs only go back four months, probably because they were wiped at one point. But vDOS has been in operation since Sept. 2012, so this is likely a very small subset of the attacks this DDoS-for-hire service has perpetrated.
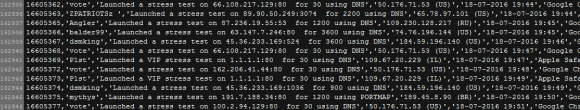
The file lists the vDOS username that ordered and paid for the attack; the target Internet address; the method of attack; the Internet address of the vDOS user at the time; the date and time the attack was executed; and the browser user agent string of the vDOS user.
]]>
http://krebsonsecurity.com/2016/09/alleged-vdos-proprietors-arrested-in-israel/feed/ 39 http://krebsonsecurity.com/2016/09/israeli-online-attack-service-vdos-earned-600000-in-two-years/ http://krebsonsecurity.com/2016/09/israeli-online-attack-service-vdos-earned-600000-in-two-years/#comments Thu, 08 Sep 2016 16:04:44 +0000
http://krebsonsecurity.com/?p=35857
vDOS — a “booter” service that has earned in excess of $600,000 over the past two years helping customers coordinate more than 150,000 so-called distributed denial-of-service (DDoS) attacks designed to knock Web sites offline — has been massively hacked, spilling secrets about tens of thousands of paying customers and their targets.
The vDOS database, obtained by KrebsOnSecurity.com at the end of July 2016, points to two young men in Israel as the principal owners and masterminds of the attack service, with support services coming from several young hackers in the United States.
To say that vDOS has been responsible for a majority of the DDoS attacks clogging up the Internet over the past few years would be an understatement. The various subscription packages to the service are sold based in part on how many seconds the denial-of-service attack will last. And in just four months between April and July 2016, vDOS was responsible for launching more than 277 million seconds of attack time, or approximately 8.81 years worth of attack traffic.
Let the enormity of that number sink in for a moment: That’s nearly nine of what I call “DDoS years” crammed into just four months. That kind of time compression is possible because vDOS handles hundreds — if not thousands — of concurrent attacks on any given day.
Although I can’t prove it yet, it seems likely that vDOS is responsible for several decades worth of DDoS years. That’s because the data leaked in the hack of vDOS suggest that the proprietors erased all digital records of attacks that customers launched between Sept. 2012 (when the service first came online) and the end of March 2016.
HOW vDOS GOT HACKED
The hack of vDOS came about after a source was investigating a vulnerability he discovered on a similar attack-for-hire service called PoodleStresser. The vulnerability allowed my source to download the configuration data for PoodleStresser’s attack servers, which pointed back to api.vdos-s[dot]com. PoodleStresser, as well as a large number of other booter services, appears to rely exclusively on firepower generated by vDOS.
From there, the source was able to exploit a more serious security hole in vDOS that allowed him to dump all of the service’s databases and configuration files, and to discover the true Internet address of four rented servers in Bulgaria (at Verdina.net) that are apparently being used to launch the attacks sold by vDOS. The DDoS-for-hire service is hidden behind DDoS protection firm Cloudflare, but its actual Internet address is 82.118.233.144.
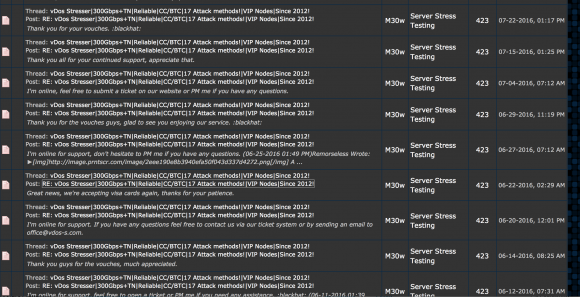
vDOS had a reputation on cybercrime forums for prompt and helpful customer service, and the leaked vDOS databases offer a fascinating glimpse into the logistical challenges associated with running a criminal attack service online that supports tens of thousands of paying customers — a significant portion of whom are all trying to use the service simultaneously.
Multiple vDOS tech support tickets were filed by customers who complained that they were unable to order attacks on Web sites in Israel. Responses from the tech support staff show that the proprietors of vDOS are indeed living in Israel and in fact set the service up so that it was unable to attack any Web sites in that country — presumably so as to not attract unwanted attention to their service from Israeli authorities. Here are a few of those responses:
(‘4130′,’Hello `d0rk`,rnAll Israeli IP ranges have been blacklisted due to security reasons.rnrnBest regards,rnP1st.’,’03-01-2015 08:39),
(‘15462′,’Hello `g4ng`,rnMh, neither. I’m actually from Israel, and decided to blacklist all of them. It’s my home country, and don’t want something to happen to them :)rnrnBest regards,rnDrop.’,’11-03-2015 15:35),
(‘15462′,’Hello `roibm123`,rnBecause I have an Israeli IP that is dynamic.. can’t risk getting hit/updating the blacklist 24/7.rnrnBest regards,rnLandon.’,’06-04-2015 23:04),
(‘4202′,’Hello `zavi156`,rnThose IPs are in israel, and we have all of Israel on our blacklist. Sorry for any inconvinience.rnrnBest regards,rnJeremy.’,’20-05-2015 10:14),
(‘4202′,’Hello `zavi156`,rnBecause the owner is in Israel, and he doesn’t want his entire region being hit offline.rnrnBest regards,rnJeremy.’,’20-05-2015 11:12),
(‘9057′,’There is a option to buy with Paypal? I will pay more than $2.5 worth.rnThis is not the first time I am buying booter from you.rnIf no, Could you please ask AplleJack? I know him from Israel.rnThanks.’,’21-05-2015 12:51),
(‘4120′,’Hello `takedown`,rnEvery single IP that’s hosted in israel is blacklisted for safety reason. rnrnBest regards,rnAppleJ4ck.’,’02-09-2015 08:57),
WHO RUNS vDOS?
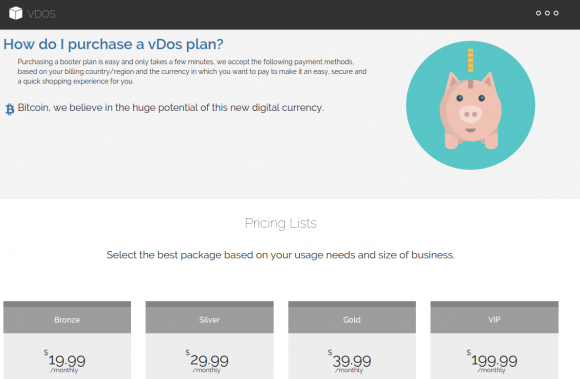
As we can see from the above responses from vDOS’s tech support, the owners and operators of vDOS are young Israeli hackers who go by the names P1st a.k.a. P1st0, and AppleJ4ck. The two men market their service mainly on the site hackforums[dot]net, selling monthly subscriptions using multiple pricing tiers ranging from $20 to $200 per month. AppleJ4ck hides behind the same nickname on Hackforums, while P1st goes by the alias “M30w” on the forum.
vDOS appears to be the longest-running booter service advertised on Hackforums, and it is by far and away the most profitable such business. Records leaked from vDOS indicate that since July 2014, tens of thousands of paying customers spent a total of more than $618,000 at the service using Bitcoin and PayPal.
Incredibly, for brief periods the site even accepted credit cards in exchange for online attacks, although it’s unclear how much the site might have made in credit card payments because the information is not in the leaked databases.
The Web server hosting vDOS also houses several other sites, including huri[dot]biz, ustress[dot]io, and vstress[dot]net. Virtually all of the administrators at vDOS have an email account that ends in v-email[dot]org, a domain that also is registered to an Itay Huri with a phone number that traces back to Israel.
The proprietors of vDOS set their service up so that anytime a customer asked for technical assistance the site would blast a text message to six different mobile numbers tied to administrators of the service, using an SMS service called Nexmo.com. Two of those mobile numbers go to phones in Israel. One of them is the same number listed for Itay Huri in the Web site registration records for v-email[dot]org; the other belongs to an Israeli citizen named Yarden Bidani. Neither individual responded to requests for comment.
The leaked database and files indicate that vDOS uses Mailgun for email management, and the secret keys needed to manage that Mailgun service were among the files stolen by my source. The data shows that vDOS support emails go to itay@huri[dot]biz, itayhuri8@gmail.com and raziel.b7@gmail.com.
LAUNDERING THE PROCEEDS FROM DDOS ATTACKS
The $618,000 in earnings documented in the vDOS leaked logs is almost certainly a conservative income figure. That’s because the vDOS service actually dates back to Sept 2012, yet the payment records are not available for purchases prior to 2014. As a result, it’s likely that this service has made its proprietors more than $1 million.
vDOS does not currently accept PayPal payments. But for several years until recently it did, and records show the proprietors of the attack service worked assiduously to launder payments for the service through a round-robin chain of PayPal accounts.
They did this because at the time PayPal was working with a team of academic researchers to identify, seize and shutter PayPal accounts that were found to be accepting funds on behalf of booter services like vDOS. Anyone interested in reading more on their success in making life harder for these booter service owners should check out my August 2015 story, Stress-Testing the Booter Services, Financially.
People running dodgy online services that violate PayPal’s terms of service generally turn to several methods to mask the true location of their PayPal Instant Payment Notification systems. Here is an interesting analysis of how popular booter services are doing so using shell corporations, link shortening services and other tricks.
Turns out, AppleJ4ck and p1st routinely recruited other forum members on Hackforums to help them launder significant sums of PayPal payments for vDOS each week.
“The paypals that the money are sent from are not verified,” AppleJ4ck says in one recruitment thread. “Most of the payments will be 200$-300$ each and I’ll do around 2-3 payments per day.”
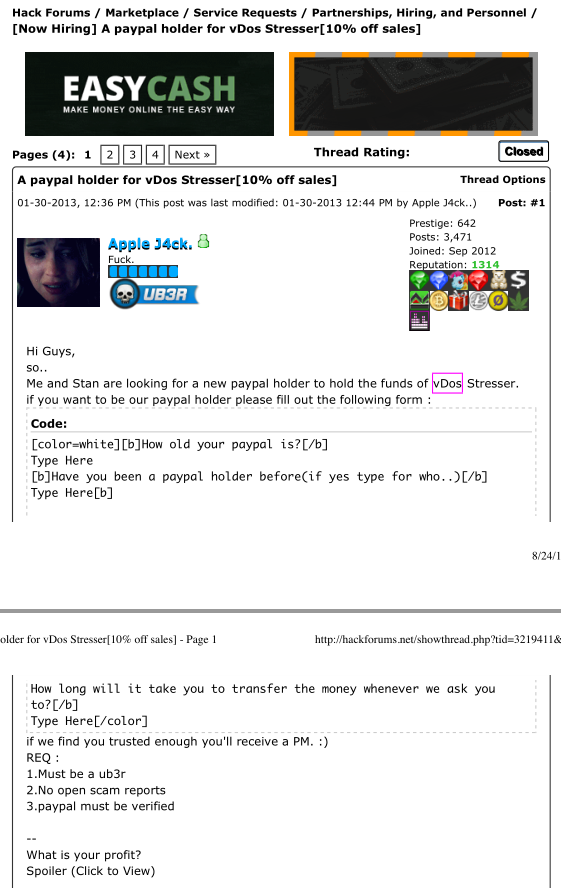
vDos co-owner AppleJ4ck recruiting Hackforums members to help launder PayPal payments for his booter service.
It is apparent from the leaked vDOS logs that in July 2016 the service’s owners implemented an additional security measure for Bitcoin payments, which they accept through Coinbase. The data shows that they now use an intermediary server (45.55.55.193) to handle Coinbase traffic. When a Bitcoin payment is received, Coinbase notifies this intermediary server, not the actual vDOS servers in Bulgaria.
A server situated in the middle and hosted at a U.S.-based address from Digital Ocean then updates the database in Bulgaria, perhaps because the vDOS proprietors believed payments from the USA would attract less interest from Coinbase than huge sums traversing through Bulgaria each day.
ANALYSIS
The extent to which the proprietors of vDOS went to launder profits from the service and to obfuscate their activities clearly indicate they knew that the majority of their users were using the service to knock others offline.
Defenders of booter and stresser services argue the services are legal because they can be used to help Web site owners stress-test their own sites and to build better defenses against such attacks. While it’s impossible to tell what percentage of vDOS users actually were using the service to stress-test their own sites, the leaked vDOS logs show that a huge percentage of the attack targets are online businesses.
In reality, the methods that vDOS uses to sustain its business are practically indistinguishable from those employed by organized cybercrime gangs, said Damon McCoy, an assistant professor of computer science at New York University.
“These guys are definitely taking a page out of the playbook of the Russian cybercriminals,” said McCoy, the researcher principally responsible for pushing vDOS and other booter services off of PayPal (see the aforementioned story Stress-Testing the Booter Services, Financially for more on this).
“A lot of the Russian botnet operators who routinely paid people to infect Windows computers with malware used to say they wouldn’t buy malware installs from Russia or CIS countries,” McCoy said. “The main reason was they didn’t want to make trouble in their local jurisdiction in the hopes that no one in their country would be a victim and have standing to bring a case against them.”
The service advertises attacks at up to 50 gigabits of data per second (Gbps). That’s roughly the equivalent of trying to cram two, high-definition Netflix movies down a target’s network pipe all at the same moment.
But Allison Nixon, director of security research at business risk intelligence firm Flashpoint, said her tests of vDOS’s service generated attacks that were quite a bit smaller than that — 14 Gbps and 6 Gbps. Nevertheless, she noted, even an attack that generates just 6 Gbps is well more than enough to cripple most sites which are not already protected by anti-DDoS services.
And herein lies the rub with services like vDOS: They put high-powered, point-and-click cyber weapons in the hands of people — mostly young men in their teens — who otherwise wouldn’t begin to know how to launch such attacks. Worse still, they force even the smallest of businesses to pay for DDoS protection services or else risk being taken offline by anyone with a grudge or agenda.
“The problem is that this kind of firepower is available to literally anyone willing to pay $30 a month,” Nixon said. “Basically what this means is that you must have DDoS protection to participate on the Internet. Otherwise, any angry young teenager is going to be able to take you offline in a heartbeat. It’s sad, but these attack services mean that DDoS protection has become the price of admission for running a Web site these days.”
Stay tuned for the next piece in this series on the hack of vDOS, which will examine some of the more interesting victims of this service.
]]>
http://krebsonsecurity.com/2016/09/israeli-online-attack-service-vdos-earned-600000-in-two-years/feed/ 78 http://krebsonsecurity.com/2016/09/the-limits-of-sms-for-2-factor-authentication/ http://krebsonsecurity.com/2016/09/the-limits-of-sms-for-2-factor-authentication/#comments Thu, 08 Sep 2016 01:29:09 +0000
http://krebsonsecurity.com/?p=36198
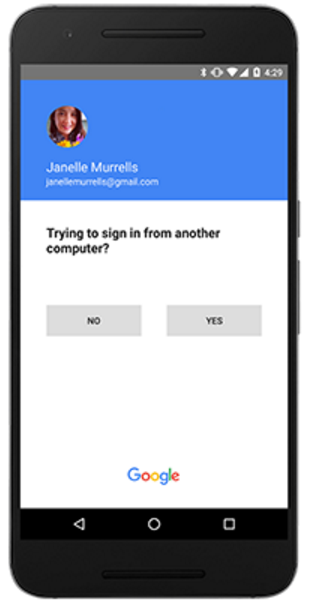
A recent ping from a reader reminded me that I’ve been meaning to blog about the security limitations of using cell phone text messages for two-factor authentication online. The reader’s daughter had received a text message claiming to be from Google, warning that her Gmail account had been locked because someone in India had tried to access her account. The young woman was advised to expect a 6-digit verification code to be sent to her and to reply to the scammer’s message with that code.
 Mark Cobb, a computer technician in Reno, Nev., said had his daughter fallen for the ruse, her Gmail account would indeed have been completely compromised, and she really would have been locked out of her account because the crooks would have changed her password straight away.
Mark Cobb, a computer technician in Reno, Nev., said had his daughter fallen for the ruse, her Gmail account would indeed have been completely compromised, and she really would have been locked out of her account because the crooks would have changed her password straight away.
Cobb’s daughter received the scam text message because she’d enabled 2-factor authentication on her Gmail account, selecting the option to have Google request that she enter a 6-digit code texted to her cell phone each time it detects a login from an unknown computer or location (in practice, the code is to be entered on the Gmail site, not sent in any kind of texted or emailed reply).
In this case, the thieves already had her password — most likely because she re-used it on some other site that got hacked. Cobb says he and his daughter believe her mobile number and password may have been exposed as part of the 2012 breach at LinkedIn.
In any case, the crooks were priming her to expect a code and to repeat it back to them because that code was the only thing standing in the way of their seizing control over her account. And they could control when Google would send the code to her phone because Google would do this as soon as they tried to log in using her username and password. Indeed, the timing aspect of this attack helps make it more believable to the target.
This is a fairly clever — if not novel — attack, and it’s one I’d wager would likely fool a decent percentage of users who have enabled text messages as a form of two-factor authentication. Certainly, text messaging is far from the strongest form of 2-factor authentication, but it is better than allowing a login with nothing more than a username and password, as this scam illustrates.
Nevertheless, text messaging codes to users isn’t the safest way to do two-factor authentication, even if some entities — like the U.S. Social Security Administration and Sony’s Playstation network — are just getting around to offering two-factor via SMS.
But don’t take my word for it. That’s according to the National Institute of Standards and Technology (NIST), which recently issued new proposed digital authentication guidelines urging organizations to favor other forms of two-factor — such as time-base one-time passwords generated by mobile apps — over text messaging. By the way, NIST is seeking feedback on these recommendations.
If anyone’s interested, Sophos’s Naked Security blog has a very readable breakdown of what’s new in the NIST guidelines. Among my favorite highlights is this broad directive: Favor the user.
“To begin with, make your password policies user friendly and put the burden on the verifier when possible,” Sophos’s Chester Wisniewski writes. “In other words, we need to stop asking users to do things that aren’t actually improving security.” Like expiring passwords and making users change them frequently, for example.
Okay, so the geeks-in-chief are saying it’s time to move away from texting as a form of 2-factor authentication. And, of course, they’re right, because text messages are a lot like email, in that it’s difficult to tell who really sent the message, and the message itself is sent in plain text — i.e. is readable by anyone who happens to be lurking in the middle.
But security experts and many technology enthusiasts have a tendency to think that everyone should see the world through the lens of security, whereas most mere mortal users just want to get on with their lives and are perfectly content to use the same password across multiple sites — regardless of how many times they’re told not to do so.
Indeed, while many more companies now offer some form of two-factor authentication than did two or three years ago — consumer adoption of this core security feature remains seriously lacking. For example, the head of security at Dropbox recently told KrebsOnSecurity that less than one percent of its user base of 500 million registered users had chosen to turn on 2-factor authentication for their accounts. And Dropbox isn’t exactly a Johnny-come-lately to the 2-factor party: It has been offering 2-factor logins for a full four years now.
I doubt Dropbox is somehow an aberration in this regard, and it seems likely that other services also suffer from single-digit two-factor adoption rates. But if more consumers haven’t enabled two-factor options, it’s probably because a) it’s still optional and b) it still demands too much caring and understanding from the user about what’s going on and how these security systems can be subverted.
Personally, I favor app-based time-based one-time password (TOTP) systems like Google Authenticator, which continuously auto-generates a unique code via a mobile-based app.
Google recently went a step further along the lines of where I’d like to see two-factor headed across the board, by debuting a new “push” authentication system that generates a prompt on the user’s mobile device that users need to tap to approve login requests. This is very similar to another push-based two-factor system I’ve long used and trusted — from Duo Security [full disclosure: Duo is an advertiser on this site].
For a comprehensive breakdown of which online services offer two-factor authentication and of what type, check out twofactorauth.org. And bear in mind that even if text-based authentication is all that’s offered, that’s still better than nothing. What’s more, it’s still probably more security than the majority of the planet has protecting their accounts.
]]>
http://krebsonsecurity.com/2016/09/the-limits-of-sms-for-2-factor-authentication/feed/ 62 http://krebsonsecurity.com/2016/09/congressional-report-slams-opm-on-data-breach/ http://krebsonsecurity.com/2016/09/congressional-report-slams-opm-on-data-breach/#comments Wed, 07 Sep 2016 04:08:16 +0000
http://krebsonsecurity.com/?p=36196
The massive data breach at the U.S. Office of Personnel Management (OPM) that exposed background investigations and fingerprint data on millions of Americans was the result of a cascading series of cybersecurity blunders from the agency’s senior leadership on down to the outdated technology used to secure the sensitive data, according to a lengthy report released today by a key government oversight panel.

OPM offices in Washington, DC. Image: Flickr.
The 241-page analysis, commissioned by the U.S. House Oversight & Government Reform Committee, blames OPM for jeopardizing U.S. national security for more than a generation.
The report offers perhaps the most exhaustive accounting and timeline of the breach since it was first publicly disclosed in mid-2015. According to the document, the lax state of OPM’s information security left the agency’s information systems exposed for any experienced hacker to infiltrate and compromise.
“The agency’s senior leadership failed to fully comprehend the extent of the compromise, allowing the hackers to remove manuals and other sensitive materials that essentially provided a roadmap to the OPM IT environment and key users for potential compromise,” the report charges.
Probably the most incisive portion of the assessment is the timeline of major events in the breach, which details a series of miscalculations on the part of the OPM leadership. The analysis paints the picture of a chronic — almost willful — underestimation by senior leadership at OPM about the seriousness of the threat facing the agency, until it was too late.
According to the report, the OPM first learned something was amiss on March 20, 2014, when the US-CERT notified the agency of data being exfiltrated from its network. In the ensuing weeks, OPM worked with US-CERT to implement a strategy to monitor the attackers’ movements to gather counterintelligence.
The only problem with this plan, according to the panel, was that the agency erroneously believed it had cornered the intruder. However, the hacker that OPM and US-CERT had eyes on wasn’t alone. While OPM monitored the first hacker [referred to in the report only as Hacker X1] on May 7, 2014 another hacker posed as an employee of an OPM contractor (Keypoint) performing background investigations. That intruder, referred to as Hacker X2, used the contractor’s OPM credentials to log into the OPM system, install malware and create a backdoor to the network.
As the agency monitored Hacker X1’s movements through the network, the committee found, it noticed hacker X1 was getting dangerously close to the security clearance background information. OPM, in conjunction with DHS, quickly developed a plan to kick Hacker X1 out of its system. It termed this remediation “the Big Bang.” At the time, the agency was confident the planned remediation effort on May 27, 2014 eliminated Hacker X1’s foothold on their systems.
The decision to execute the Big Bang plan was made after OPM observed the attacker load keystroke logging malware onto the workstations of several database administrators, the panel found.
“But Hacker X2, who had successfully established a foothold on OPM’s systems and had not been detected due to gaps in OPM’s security posture, remained in OPM’s systems post-Big Bang,” the report notes.
On June 5, malware was successfully installed on a KeyPoint Web server. After that, X2 moved around OPM’s system until July 29, 2014, when the intruders registered opmlearning.org — a domain the attackers used as a command-and-control center to manage their malware operations.
Beginning in July through August 2014, the Hacker X2 exfiltrated the security clearance background investigation files. Then in December 2014, 4.2 million personnel records were exfiltrated.
On March 3, 2015, wdc-news-post[dot]com was registered by the attackers, who used it as a command-and-control network. On March 26, 2015, the intruders begin stealing fingerprint data.
The committee found that had the OPM implemented basic, required security controls and more expeditiously deployed cutting edge security tools when they first learned hackers were targeting such sensitive data, they could have significantly delayed, potentially prevented, or significantly mitigated the theft.
For example, “OPM’s adoption of two-factor authentication for remote logons in early 2015, which had long been required of federal agencies, would have precluded continued access by the intruder into the OPM network,” the panel concluded.
Unfortunately, the exact details on how and when the attackers gained entry and established a persistent presence in OPM’s network are not entirely clear, the committee charges.
“This is in large part due to sloppy cyber hygiene and inadequate security technologies that left OPM with reduced visibility into the traffic on its systems,” the report notes. “The data breach by Hacker X1 in 2014 should have sounded a high level, multi-agency national security alarm that a sophisticated, persistent actor was seeking to access OPM’s highest-value data. It wasn’t until April 15, 2015 that the OPM identified the first indicator that its systems were compromised by Hacker X2.”
The information stolen in the breach included detailed files and personal background reports on more than 21.5 million individuals, and fingerprint data on 5.6 million of these individuals. Those security clearance background reports often included extremely sensitive information, such as whether applicants had consulted with a health care professional regarding an emotional or mental health condition; illegally used any drugs or controlled substances; experienced financial problems due to gambling.
The intrusion, widely attributed to hackers working with the Chinese government, likely pointed out which federal employees working for the U.S. State Department were actually spies trained by the U.S. Central Intelligence Agency. That’s because — unlike most federal agencies — the CIA conducted its own background checks on potential employees, and did not manage the process through the OPM.
As The Washington Post pointed out in September 2015, the CIA ended up pulling a number of officers from its embassy in Beijing in the wake of the OPM breach, mainly because the data leaked in the intrusion would have let the Chinese government work out which State Department employees stationed there were not listed in the background check data stolen from the OPM.
As bad and as total as the OPM breach has been, it’s remarkable how few security experts I’ve heard raise the issue of what might be at stake if the OPM plunderers had not simply stolen data, but also manipulated it.
Not long after congressional hearings began on the OPM breach, I heard from a source in the U.S. intelligence community who wondered why nobody was asking this question: If the attackers could steal all of this sensitive data and go undetected for so long, could they not also have granted security clearances to people who not only didn’t actually warrant them, but who might have been recruited in advance to work for the attackers? To this date, I’ve not heard a good answer to this question.
A copy of the 110 mb report is available here (PDF).
]]>
http://krebsonsecurity.com/2016/09/congressional-report-slams-opm-on-data-breach/feed/ 76 http://krebsonsecurity.com/2016/09/location-privacy-the-purview-of-the-rich-and-indigent/ http://krebsonsecurity.com/2016/09/location-privacy-the-purview-of-the-rich-and-indigent/#comments Tue, 06 Sep 2016 01:46:11 +0000
http://krebsonsecurity.com/?p=34888
I’d just finished parking my car in the covered garage at Reagan National Airport just across the river from Washington, D.C. when I noticed a dark green minivan slowly creeping through the row behind me. The vehicle caught my attention because its driver didn’t appear to be looking for an open spot. What’s more, the van had what looked like two cameras perched atop its roof — one of each side, both pointed down and slightly off to the side.
I had a few hours before my flight boarded, so I delayed my walk to the terminal and cut through several rows of cars to snag a video of the guy moving haltingly through another line of cars. I approached the driver and asked what he was doing. He smiled and tilted the lid on his bolted-down laptop so that I could see the pictures he was taking with the mounted cameras: He was photographing every license plate in the garage (for the record, his plate was a Virginia tag number 36-646L).

A van at Reagan National Airport equipped with automated license plate readers fixed to the roof.
The man said he was hired by the airport to keep track of the precise location of every car in the lot, explaining that the data is most often used by the airport when passengers returning from a trip forget where they parked their vehicles. I checked with the Metropolitan Washington Airports Authority (MWAA), which manages the garage, and they confirmed the license plate imaging service was handled by a third-party firm called HUB Parking.
I’m accustomed to having my license plate photographed when entering a parking area (Dulles International Airport in Virginia does this), but until that encounter at Reagan National I never considered that this was done manually.
“Reagan National uses this service to assist customers in finding their lost vehicles,” said MWAA spokesperson Kimberly Gibbs. “If the customer remembers their license plate it can be entered into the system to determine what garages and on what aisle their vehicle is parked.”
What does HUB Parking do with the information its clients collect? Ilaria Riva, marketing manager for HUB Parking, says the company does not sell or share the data it collects, and that it is up to the client to decide how that information is stored or shared.
“It is true the solution that HUB provides to our clients may collect data, but HUB does not own the data nor do we have any control over what the customer does with it,” Riva said.
Gibbs said MWAA does not share parking information with outside organizations. But make no mistake: the technology used at Reagan National Airport, known as automated license plate reader or ALPR systems, is already widely deployed by municipalities, police forces and private companies — particularly those in the business of repossessing vehicles from deadbeat owners who don’t pay their bills.
It’s true that people have zero expectation of privacy in public places — and roads and parking garages certainly are public places for the most part. But according to the Electronic Frontier Foundation (EFF), the data collected by ALPR systems can be very revealing, and in many cities ALPR technology is rapidly outpacing the law.
“By matching your car to a particular time, date and location, and then building a database of that information over time, law enforcement can learn where you work and live, what doctor you go to, which religious services you attend, and who your friends are,” the EFF warns.
A 2014 ABC News investigation in Los Angeles found the technology broadly in use by everyone from the local police to repo men. The story notes that there are little or no restrictions on what private companies that collect time- and location-stamped license plate data can do with the information. As a result, they are selling it to insurers, banks, law enforcement and federal agencies.
In Texas, the EFF highlights how state and local law enforcement agencies have free access to ALPR equipment and license plate data maintained by a private company called Vigilant Solutions. In exchange, police cruisers are retrofitted with credit-card machines so that law enforcement officers can take payments for delinquent fines and other charges on the spot — with a 25 percent processing fee tacked on that goes straight to Vigilant. In essence, the driver is paying Vigilant to provide the local cops with the technology used to identify and detain the driver.
“The ‘warrant redemption’ program works like this,” the EFF wrote. “The agency is given no-cost license plate readers as well as free access to LEARN-NVLS, the ALPR data system Vigilant says contains more than 2.8-billion plate scans and is growing by more than 70-million scans a month. This also includes a wide variety of analytical and predictive software tools. Also, the agency is merely licensing the technology; Vigilant can take it back at any time.”
That’s right: Even if the contract between the state and Vigilant ends, the latter gets to keep all of the license plate data collected by the agency, and potentially sell or license the information to other governments or use it for other purposes.
I wanted to write this story not because it’s particularly newsy, but because I was curious about a single event and ended up learning a great deal that I didn’t already know about how pervasive this technology has become.
Yes, we need more transparency about what companies and governments are doing with information collected in public. But here’s the naked truth: None of us should harbor any illusions about maintaining the privacy of our location at any given moment — particularly in public spaces.
As it happens, location privacy is a considerably expensive and difficult goal for most Americans to attain and maintain. Our mobile phones are constantly pinging cell towers, making it simple for mobile providers and law enforcement agencies to get a fix on your location within a few dozen meters.
Obscuring the address of your residence is even harder. If you’ve ever had a mortgage on your home or secured utilities for your residence using your own name, chances are excellent that your name and address are in thousands of databases, and can be found with a free or inexpensive public records search online.
Increasingly, location privacy is the exclusive purview of two groups of Americans: Those who are indigent and/or homeless and those who are wealthy. Only the well-off can afford the substantial costs and many petty inconveniences associated with separating one’s name from their address, vehicle, phone records and other modern niceties that make one easy to track and find.
]]>
http://krebsonsecurity.com/2016/09/location-privacy-the-purview-of-the-rich-and-indigent/feed/ 85 http://krebsonsecurity.com/2016/09/flash-hijacks-add-new-twist-to-muggings/ http://krebsonsecurity.com/2016/09/flash-hijacks-add-new-twist-to-muggings/#comments Sat, 03 Sep 2016 21:29:36 +0000
http://krebsonsecurity.com/?p=36164
A frequent crime in Brazil is a scheme in which thieves kidnap people as they’re leaving a bank, and free them only after visiting a number of ATMs to withdraw cash. Now the crooks have introduced a new time-saving wrinkle into this scam: In these so-called “flash hijacks” the thieves pull out a wireless card reader, swipe a few debit transactions with the victim’s card, and then release the individual.
A story in the Brazilian newspaper Liberal documents one such recent flash hijacking, involving two musicians in their 20s who were accosted by a pair of robbers — one of whom was carrying a gun. The thieves forced the victims to divulge their debit card personal identification numbers (PINs), and then proceeded to swipe the victim’s cards on a handheld, wireless card machine.
First spotted in 2015, flash hijackings are becoming more common in Brazil, said Paulo Brito, a cybersecurity expert living in the Campinas area of Brazil. Brito said even his friend’s son was similarly victimized recently.
“Of course transactions can be traced as far as they are done with Brazilian banks, but these bad guys can evolve and transact with foreign banks,” Brito said.
I suppose it’s slightly less traumatic for the victim if the use of handheld machines by the crooks mean victims have a gun to their heads for a shorter duration. It’s also nice that the thieves are bringing the theft to the victim, instead of the other way around.
In any case, these attacks underscore a major point I try to make when adding updates to my All About Skimmers series: Most of us are far more likely to get mugged after withdrawing money from an ATM or bank than we are to encounter a skimming device in real life.
The most important security advice is to watch out for your own physical safety while using an ATM. Keep your wits about you as you transact in and leave the area, and try to be keenly aware of your immediate surroundings. Use only machines in public, well-lit areas, and avoid ATMs in secluded spots. Also, cover the PIN pad with your hand when entering your PIN: That way, if even if the thieves somehow skim your card, there is less chance that they will be able to snag your PIN as well.
]]>
http://krebsonsecurity.com/2016/09/flash-hijacks-add-new-twist-to-muggings/feed/ 34 http://krebsonsecurity.com/2016/09/kimpton-hotels-acknowledges-data-breach/ http://krebsonsecurity.com/2016/09/kimpton-hotels-acknowledges-data-breach/#comments Thu, 01 Sep 2016 12:44:31 +0000
http://krebsonsecurity.com/?p=36174
Kimpton Hotels on Wednesday formally acknowledged that malware found on payment terminals in many of its hotels and restaurants may have compromised credit/debit cards of guests who patronized the properties in the first half of this year. The disclosure comes more than a month after KrebsOnSecurity first contacted to the company about a possible credit card breach across most of its locations.
 According to a notice added to the Kimpton Web site, the incident involved cards used at certain restaurants and hotel front desks from February 16, 2016 to July 7, 2016. Kimpton has posted a list of more than 60 restaurants and hotels where the company found and removed card-stealing malicious software from payment terminals.
According to a notice added to the Kimpton Web site, the incident involved cards used at certain restaurants and hotel front desks from February 16, 2016 to July 7, 2016. Kimpton has posted a list of more than 60 restaurants and hotels where the company found and removed card-stealing malicious software from payment terminals.
Kimpton joins a long list of hotel brands that have acknowledged card breaches over the last year after prompting by KrebsOnSecurity, including Trump Hotels (twice), Hilton, Mandarin Oriental, and White Lodging (twice). Breaches also have hit hospitality chains Starwood Hotels and Hyatt.
In many of those incidents, thieves had planted malicious software on the point-of-sale devices at restaurants and bars inside of the hotel chains. However, the source and extent of the apparent breach at Kimpton properties is still unknown.
Point-of-sale based malware has driven most of the credit card breaches over the past two years, including intrusions at Target and Home Depot, as well as breaches at a slew of point-of-sale vendors. The malware usually is installed via hacked remote administration tools. Once the attackers have their malware loaded onto the point-of-sale devices, they can remotely capture data from each card swiped at that cash register.
Thieves can then sell the data to crooks who specialize in encoding the stolen data onto any card with a magnetic stripe, and using the cards to buy gift cards and high-priced goods from big-box stores like Target and Best Buy.
Readers should remember that they’re not liable for fraudulent charges on their credit or debit cards, but they still have to report the unauthorized transactions. There is no substitute for keeping a close eye on your card statements. Also, consider using credit cards instead of debit cards; having your checking account emptied of cash while your bank sorts out the situation can be a hassle and lead to secondary problems (bounced checks, for instance).
]]>
http://krebsonsecurity.com/2016/09/kimpton-hotels-acknowledges-data-breach/feed/ 49 http://krebsonsecurity.com/2016/08/hostsailor-threatens-to-sue-krebsonsecurity/ http://krebsonsecurity.com/2016/08/hostsailor-threatens-to-sue-krebsonsecurity/#comments Mon, 29 Aug 2016 02:57:09 +0000
http://krebsonsecurity.com/?p=36147
Earlier this month, KrebsOnSecurity published The Reincarnation of a Bulletproof Hoster, which examined evidence suggesting that a Web hosting company called HostSailor was created out of the ashes of another, now-defunct hosting firm notorious for harboring spammers, scammers and other online ne’er-do-wells. Today, HostSailor’s lawyers threatened to sue this author unless the story is removed from the Web.
Obviously, I stand by my reporting and have no intention of unpublishing stories. But I’m writing about HostSailor again here because I promised to post an update if they ever responded to my requests for comment.
The letter, signed by Abdullah Alzarooni Advocates in Dubai — where HostSailor says it is based — carries the subject line, “Warning from Acts of Extortion and Abuse of the Privacy of Third Parties.” It lists a number of links to content the company apparently finds objectionable.
Could this same kind of legal pressure be why security industry giant Trend Micro removed all reference to HostSailor from the report that started all this? Trend hasn’t responded to direct questions about that.
Astute readers will notice in the letter (pasted below) a link to a Twitter message from this author among the many things HostSailor’s lawyers will like me to disappear from the Internet. That tweet to HostSailor’s Twitter account read:
“Potential downside of reporting ISIS sites: The hosting firm (ahem @HostSailor) may share your info/name/report with ISIS. Opsec, people!”
I sent that tweet after hearing from a source with whom I’ve been working to report sites affiliated with the jihadist militant group ISIS. The source had reported to HostSailor several of its Internet addresses that were being used by a propaganda site promoting videos of beheadings and other atrocities by ISIS, and he shared emails indicating that HostSailor had simply forwarded his abuse email on to its customer — complete with my source’s name and contact information. Thankfully, he was using a pseudonym and throwaway email address.
HostSailor’s twitter account responded by saying that the company doesn’t share information about its customers. But of course my tweet was regarding information shared about someone who is not a HostSailor customer.
This isn’t the first time KrebsOnSecurity has been threatened with lawsuits over stories published here. The last time I got one of these letters was in Sept. 2015, from a lawyer representing AshleyMadison’s former chief technology officer. The year before, it was Sony Pictures Entertainment, whose lawyers lashed out a large number of publications for too closely covering its epic and unprecedented data breach in 2014.
Prior to that, I received some letters from the lawyers for Igor Gusev, one of the main characters in my book, Spam Nation. Mr. Gusev’s attorneys insisted that I was publishing stolen information — pictures of him, financial records from his spam empire “SpamIt” — and demanded that I remove all offending items and publish an apology.
My attorney in that instance laughed out loud when I shared the letter from Gusev’s lawyers, calling it a “blivit.” When I apparently took more than a moment to get the joke, he explained that a “blivit” is a term coined by the late great author Kurt Vonnegut, who defined it as “two pounds of shit in a one-pound bag.”
Only time will tell if this letter is a blivit as well. I’ve taken the liberty of sanitizing the PDF document it came in, and converting that into two image files – in case anyone wants to take a look.

An emailed “legal notice” I apparently received from a law firm in Dubai, demanding that I unpublish an unflattering story about HostSailor.
]]>
http://krebsonsecurity.com/2016/08/hostsailor-threatens-to-sue-krebsonsecurity/feed/ 82 http://krebsonsecurity.com/2016/08/inside-the-attack-that-almost-broke-the-internet/ http://krebsonsecurity.com/2016/08/inside-the-attack-that-almost-broke-the-internet/#comments Fri, 26 Aug 2016 16:58:03 +0000
http://krebsonsecurity.com/?p=35925