Carbanak Gang Tied to Russian Security Firm?
Nintendo shares up more than 10 percent in early trade
July 18, 2016Baidu investor criticizes sale of video unit to CEO
July 18, 2016Among the more plunderous cybercrime gangs is a group known as “Carbanak,” Eastern European hackers blamed for stealing more than a billion dollars from banks. Today we’ll examine some compelling clues that point to a connection between the Carbanak gang’s staging grounds and a Russian security firm that claims to work with some of the world’s largest brands in cybersecurity.
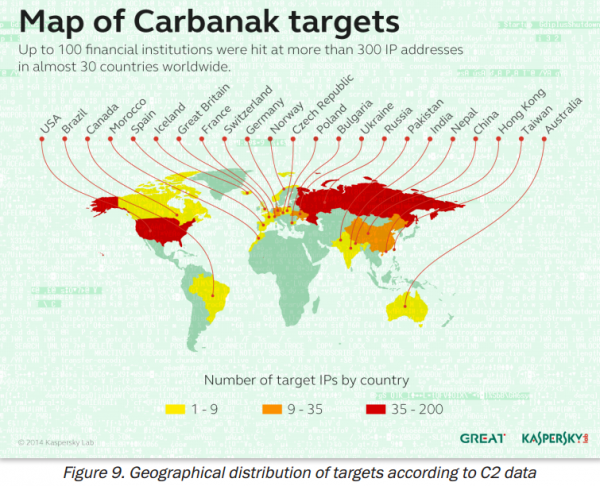
The Carbanak gang derives its name from the banking malware used in countless high-dollar cyberheists. The gang is perhaps best known for hacking directly into bank networks using poisoned Microsoft Office files, and then using that access to force bank ATMs into dispensing cash. Russian security firm Kaspersky Lab estimates that the Carbanak Gang has likely stolen upwards of USD $1 billion — but mostly from Russian banks.
I recently heard from security researcher Ron Guilmette, an anti-spam crusader whose sleuthing has been featured on several occasions on this site and in the blog I wrote for The Washington Post. Guilmette said he’d found some interesting commonalities in the original Web site registration records for a slew of sites that all have been previously responsible for pushing malware known to be used by the Carbanak gang.
For example, the domains “weekend-service[dot]com” “coral-travel[dot]com” and “freemsk-dns[dot]com” all were documented by multiple security firms as distribution hubs for Carbanak crimeware. Historic registration or “WHOIS” records maintained by Domaintools.com for all three domains contain the same phone and fax numbers for what appears to be a Xicheng Co. in China — 1066569215 and 1066549216, each preceded by either a +86 (China’s country code) or +01 (USA). Each domain record also includes the the same contact address: “williamdanielsen@yahoo.com“.
According to data gathered by ThreatConnect, a threat intelligence provider [full disclosure: ThreatConnect is an advertiser on this blog], at least 484 domains were registered by to the williamdanielsen@yahoo.com address or to one of 26 other email addresses that listed the same phone numbers and Chinese company. “At least 304 of these domains have been associated with a malware plugin [that] has previously been attributed to Carbanak activity,” ThreatConnect told KrebsOnSecurity.
Going back to those two phone numbers, 1066569215 and 1066549216; at first glance they appear to be sequential, but closer inspection reveals they differ slightly in the middle. Among the very few domains registered to those Chinese phone numbers that hasn’t been seen launching malware is a Web site called “cubehost[dot]biz,” which according to records was registered in Sept. 2013 to a 28-year-old Artem Tveritinov of Perm, Russia.
Cubehost[dot]biz is a dormant site, but it appears to be the sister property to a Russian security firm called Infocube (also spelled “Infokube”). The InfoKube web site — infokube.ru — is also registered to Mr. Tveritinov of Perm, Russia; there are dozens of records in the WHOIS history for infokube.ru, but only the oldest, original record from 2011 contains the email address atveritinov@gmail.com.
That same email address was used to register a four-year-old profile account at the popular Russian social networking site Vkontakte for Artyom “LioN” Tveritinov from Perm, Russia. The “LioN” bit is an apparent reference to an Infokube anti-virus product by the same name.
Mr. Tveritinov is quoted as “the CEO of InfoKub” in a press release from FalconGaze, a Moscow-based data security firm that partnered with the InfoKube to implement “data protection and employee monitoring” at a Russian commercial research institute. InfoKube’s own press releases say the company also has been hired to develop “a system to protect information from unauthorized access” undertaken for the City of Perm, Russia, and for consulting projects relating to “information security” undertaken for and with the State Ministry of Interior of Russia.
The company’s Web site claims that InfoKube partners with a variety of established security firms — including Symantec and Kaspersky. The latter confirmed InfoKube was “a very minor partner” of Kaspersky’s, mostly involved in systems integration. Zyxel, another partner listed on InfoKube’s partners page, said it had no partners named InfoKube. Slovakia-based security firm ESET said “Infokube is not and has never been a partner of ESET in Russia.”
Presented with Guilmette’s findings, I was keen to ask Mr. Tveritinov how the phone and fax numbers for a Chinese entity whose phone number has become synonymous with cybercrime came to be copied verbatim into Cubehost’s Web site registration records. I sent requests for comment to Mr. Tveritinov via email and through his Vkontakte page.
Initially, I received a friendly reply from Mr. Tveritinov via email expressing curiosity about my inquiry, and asking how I’d discovered his email address. In the midst of composing a more detailed follow-up reply, I noticed that the Vkontakte social networking profile that Tveritinov had maintained regularly since April 2012 was being permanently deleted before my eyes. Tveritinov’s profile page and photos actually disappeared from the screen I had up on one monitor as I was in the process of composing an email to him in the other.
Not long after Tveritinov’s Vkontakte page was deleted, I heard from him via email. Ignoring my question about the sudden disappearance of his social media account, Tveritinov said he never registered cubehost.biz and that his personal information was stolen and used in the registration records for cubehost.biz.
“Our company never did anything illegal, and conducts all activities according to the laws of Russian Federation,” Tveritinov said in an email. “Also, it’s quite stupid to use our own personal data to register domains to be used for crimes, as [we are] specialists in the information security field.”
Turns out, InfoKube/Cubehost also runs an entire swath of Internet addresses managed by Petersburg Internet Network (PIN) Ltd., an ISP in Saint Petersburg, Russia that has a less-than-stellar reputation for online badness.
For example, many of the aforementioned domain names that security firms have conclusively tied to Carbanak distribution (e.g., freemsk-dns[dot].com) are hosted in Internet address space assigned to Cubehost. A search of the RIPE registration records for the block of addresses at 146.185.239.0/24 turns up a physical address in Ras al Khaimah, an emirate of the United Arab Emirates (UAE) that has sought to build a reputation as a tax shelter and a place where it is easy to create completely anonymous offshore companies. The same listing says abuse complaints about Internet addresses in that address block should be sent to “info@cubehost.biz.”
This PIN hosting provider in St. Petersburg has achieved a degree of notoriety in its own right and is probably worthy of additional scrutiny given its reputation as a haven for all kinds of online ne’er-do-wells. In fact, Doug Madory, director of Internet analysis at Internet performance management firm Dyn, has referred to the company as “…perhaps the leading contender for being named the Mos Eisley of the Internet” (a clever reference to the spaceport full of alien outlaws in the 1977 movie Star Wars).
Madory explained that PIN’s hard-won bad reputation stems from the ISP’s documented propensity for absconding with huge chunks of Internet address blocks that don’t actually belong to it, and then re-leasing that purloined Internet address space to spammers and other Internet miscreants.
For his part, Guilmette points to a decade’s worth of other nefarious activity going on at the Internet address space apparently assigned to Tveritinov and his company. For example, in 2013 Microsoft seized a bunch of domains parked there that were used as controllers for Citadel online banking malware, and all of those domains had the same “Xicheng Co.” data in their WHOIS records. A Sept. 2011 report on the security blog dynamoo.com notes several domains with that Xicheng Co. WHOIS information showing up in online banking heists powered by the Sinowal banking Trojan way back in 2006.
“If Mr. Tveritinov, has either knowledge of, or direct involvement in even a fraction of the criminal goings-on within his address block, then the possibility that he may perhaps also have a role in other and additional criminal enterprises… including perhaps even the Carbanak cyber banking heists… becomes all the more plausible and probable,” Guilmette said.
It remains unclear to what extent the Carbanak gang is still active. Last month, authorities in Russia arrested 50 people allegedlyl tied to the organized cybercrime group, whose members reportedly hail from Russia, China, Ukraine and other parts of Europe. The action was billed as the biggest ever crackdown on financial hackers in Russia.
Tags: 146.185.239.0/24, Artem Tveritinov, atveritinov@gmail.com, Carbanak, DomainTools.com, Doug Madory, FalconGaze, info@cubehost.biz, infokube.ru, Kaspersky Lab, Petersburg Internet Network, Ron Guilmette, ThreatConnect, vkontakte, williamdanielsen@yahoo.com
This entry was posted on Monday, July 18th, 2016 at 11:49 pm and is filed under A Little Sunshine, Breadcrumbs. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.