Malicious Office 365 Apps Are the Ultimate Insiders
The Wages of Password Re-use: Your Money or Your Life
May 4, 2021Investment Scammer John Davies Reinvents Himself?
May 7, 2021Phishers targeting Microsoft Office 365 users increasingly are turning to specialized links that take users to their organization’s own email login page. After a user logs in, the link prompts them to install a malicious but innocuously-named app that gives the attacker persistent, password-free access to any of the user’s emails and files, both of which are then plundered to launch malware and phishing scams against others.
These attacks begin with an emailed link that when clicked loads not a phishing site but the user’s actual Office 365 login page — whether that be at microsoft.com or their employer’s domain. After logging in, the user might see a prompt that looks something like this:
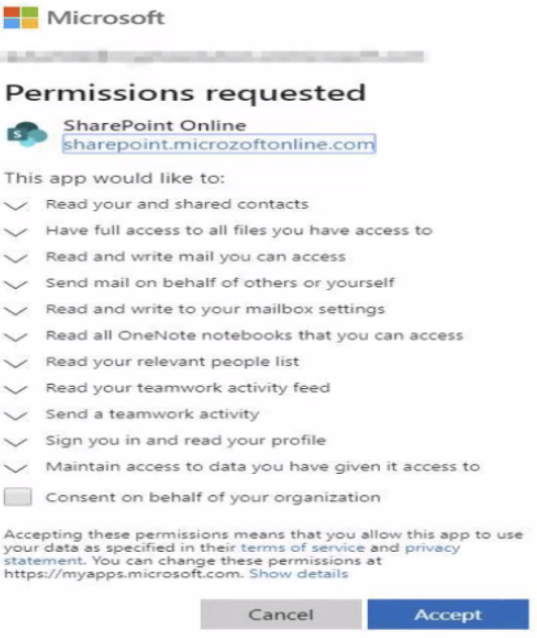
These malicious apps allow attackers to bypass multi-factor authentication, because they are approved by the user after that user has already logged in. Also, the apps will persist in a user’s Office 365 account indefinitely until removed, and will survive even after an account password reset.
This week, messaging security vendor Proofpoint published some new data on the rise of these malicious Office 365 apps, noting that a high percentage of Office users will fall for this scheme [full disclosure: Proofpoint is an advertiser on this website].
Ryan Kalember, Proofpoint’s executive vice president of cybersecurity strategy, said 55 percent of the company’s customers have faced these malicious app attacks at one point or another.
“Of those who got attacked, about 22 percent — or one in five — were successfully compromised,” Kalember said.
Kalember said Microsoft last year sought to limit the spread of these malicious Office apps by creating an app publisher verification system, which requires the publisher to be a valid Microsoft Partner Network member.
That approval process is cumbersome for attackers, so they’ve devised a simple work around. “Now, they’re compromising accounts in credible tenants first,” Proofpoint explains. “Then, they’re creating, hosting and spreading cloud malware from within.”
The attackers responsible for deploying these malicious Office apps aren’t after passwords, and in this scenario they can’t even see them. Rather, they’re hoping that after logging in users will click yes to a approve the installation of a malicious but innocuously-named app into their Office365 account.
Kalember said the crooks behind these malicious apps typically use any compromised email accounts to conduct “business email compromise” or BEC fraud, which involves spoofing an email from someone in authority at an organization and requesting the payment of a fictitious invoice. Other uses have included the sending of malware-laced emails from the victim’s email account.
Last year, Proofpoint wrote about a service in the cybercriminal underground where customers could access various Office 365 accounts without a username or password. The service also advertised the ability to extract and filter emails and files based on selected keywords, as well as attach malicious macros to all documents in a user’s Microsoft OneDrive.
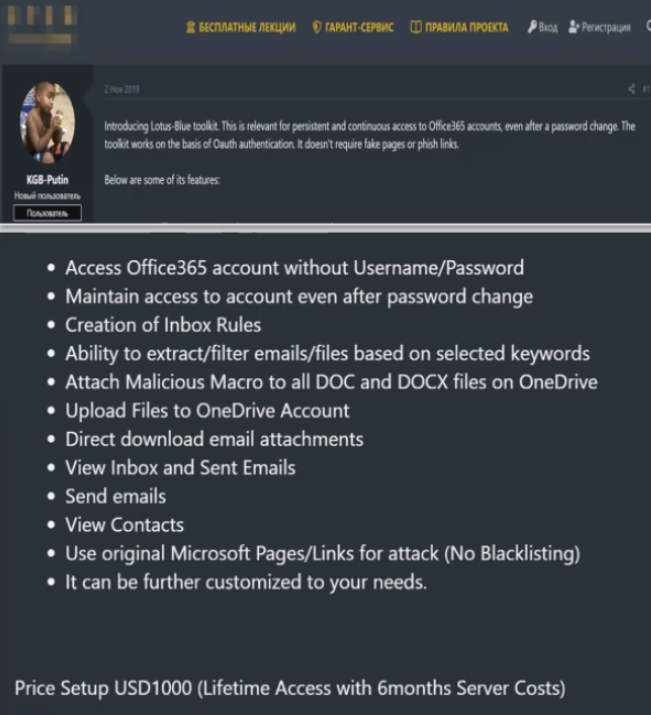
A cybercriminal service advertising the sale of access to hacked Office365 accounts. Image: Proofpoint.
“You don’t need a botnet if you have Office 365, and you don’t need malware if you have these [malicious] apps,” Kalember said. “It’s just easier, and it’s a good way to bypass multi-factor authentication.”
KrebsOnSecurity first warned about this trend in January 2020. That story cited Microsoft saying that while organizations running Office 365 could restrict users from installing apps, doing so was a “drastic step” that “severely impairs your users’ ability to be productive with third-party applications.”
Since then, Microsoft added a policy that allows Office 365 administrators to block users from consenting to an application from a non-verified publisher. Also, applications published after November 8, 2020, are coupled with a consent screen warning in case the publisher is not verified, and the tenant policy allows the consent.
Proofpoint says O365 administrators should limit or block which non-administrators can create applications, and enable Microsoft’s verified publisher policy — as a majority of cloud malware is still coming from Office 365 tenants that are not part of Microsoft’s partner network.
