How Google Took on Mirai, KrebsOnSecurity
Lacking voting rights, Snap IPO to test fund governance talk
February 3, 2017Google sells satellite imaging business Terra Bella to Planet Labs
February 3, 2017
The third week of September 2016 was a dark and stormy one for KrebsOnSecurity. Wave after wave of huge denial-of-service attacks flooded this site, forcing me to pull the plug on it until I could secure protection from further assault. The site resurfaced three days later under the aegis of Google’s Project Shield, an initiative which seeks to protect journalists and news sites from being censored by these crippling digital sieges.
Damian Menscher, a Google security engineer with whom I worked very closely on the migration to Project Shield, spoke this week about the unique challenges involved in protecting a small site like this one from very large, sustained and constantly morphing attacks.
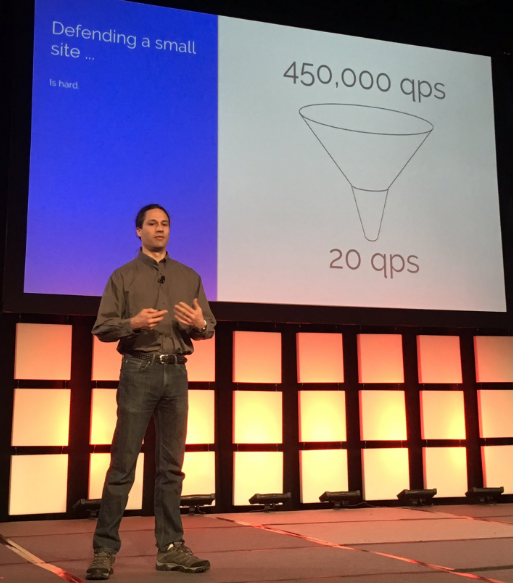
Google Security Reliability Engineer Damian Menscher speaking at the Enigma conference this week. Photo: @mrisher
Addressing the Enigma 2017 security conference in Oakland, Calif., Menscher said his team only briefly considered whether it was such a good idea to invite a news site that takes frequent swings at the DDoS-for-hire industry.
“What happens if this botnet actually takes down google.com and we lose all of our revenue?” Menscher recalled. “But we considered [that] if the botnet can take us down, we’re probably already at risk anyway. There’s nothing stopping them from attacking us at any time. So we really had nothing to lose here.”
Ars Technica’s Dan Goodin was at the Engima conference and filed this report:
“It took only about an hour for Menscher’s team to arrive at the decision to help Krebs. A much more lengthy process involved actually admitting KrebsOnSecurity into Project Shield…A key requirement for admittance is that the person requesting service proves they have control over the site. Because KrebsOnSecurity was down at that moment, Krebs was unable to satisfy this requirement.
Making matters worse, the domain-name system settings KrebsOnSecurity used had been locked to thwart the attempted domain hijacking attacks that regularly targeted the site. That prevented Krebs from showing he had control of the site’s DNS settings.
Once Project Shield ultimately got KrebsOnSecurity back online, it took just 14 minutes for the attacks to resume.”
For more, check out Dan Goodin’s excellent piece, How Google Fought Back Against a Crippling IoT-Powered Botnet and Won. And a rolling thanks to Damian (a true mensch) and to Project Shield for deflecting the evil bits.
For more background on the botnet responsible for knocking this site offline, see Who is Anna-Senpai, the Mirai Worm Author?
Tags: anna-senpai, Ars Technica, Damian Menscher, Dan Goodin, DDoS, denial-of-service attacks, google, IoT, Mirai worm, Project Shield
This entry was posted on Friday, February 3rd, 2017 at 3:57 pm and is filed under Other. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.
