Researchers Find Fresh Fodder for IoT Attack Cannons
Google meets renewable energy goal for global operations
December 6, 2016Supreme Court rules for Samsung in smartphone fight with Apple
December 6, 2016
New research published this week could provide plenty of fresh fodder for Mirai, a malware strain that enslaves poorly-secured Internet of Things (IoT) devices for use in powerful online attacks. Researchers in Austria have unearthed a pair of backdoor accounts in more than 80 different IP camera models made by Sony Corp. Separately, Israeli security experts have discovered trivially exploitable weaknesses in nearly a half-million white-labeled IP camera models that are not currently sought out by Mirai.

A Sony IPELA camera. Image: Sony.
In a blog post published today, Austrian security firm SEC Consult said it found two apparent backdoor accounts in Sony IPELA Engine IP Cameras — devices mainly used by enterprises and authorities. According to SEC Consult, the two previously undocumented user accounts — named “primana” and “debug” — could be used by remote attackers to commandeer the Web server built into these devices, and then to enable “telnet” on them.
Telnet — a protocol that allows remote logons over the Internet — is the very same communications method abused by Mirai, which constantly scours the Web for IoT devices with telnet enabled and protected by factory-default passwords.
“We believe that this backdoor was introduced by Sony developers on purpose (maybe as a way to debug the device during development or factory functional testing) and not an ‘unauthorized third party’ like in other cases (e.g. the Juniper ScreenOS Backdoor, CVE-2015-7755),” SEC Consult wrote.
It’s unclear precisely how many Sony IP cameras may be vulnerable, but a scan of the Web using Censys.io indicates there are at least 4,250 that are currently reachable over the Internet.
“Those Sony IPELA ENGINE IP camera devices are definitely reachable on the Internet and a potential target for Mirai-like botnets, but of course it depends on the network/firewall configuration,” said Johannes Greil, head of SEC Consult Vulnerability Lab. “From our point of view, this is only the tip of the iceberg because it’s only one search string fro the device we have.”
Greil said there are other undocumented functionalities in the Sony IP cameras that could be maliciously used by malware or miscreants, such as commands that can be invoked to distort images and/or video recorded by the cameras, or a camera heating feature that could be abused to overheat the devices.
Sony did not respond to multiple requests for comment. But the researchers said said Sony has quietly made available to its users an update that disables the backdoor accounts on the affected devices. However, users still need to manually update the firmware using a program called SNC Toolbox.
Greil said it seems likely that the backdoor accounts have been present in Sony cameras for at least four years, as there are signs that someone may have discovered the hidden accounts back in 2012 and attempted to crack the passwords then. SEC Consult’s writeup on their findings is available here.
In other news, researchers at security firm Cybereason say they’ve found at least two previously unknown security flaws in dozens of IP camera families that are white-labeled under a number of different brands (and some without brands at all) that are available for purchase via places like eBay and Amazon. The devices are all administered with the password “888888,” and may be remotely accessible over the Internet if they are not protected behind a firewall. KrebsOnSecurity has confirmed that while the Mirai botnet currently includes this password in the combinations it tries, the username for this password is not part of Mirai’s current configuration.
But Cybereason’s team found that they could easily exploit these devices even if they were set up behind a firewall. That’s because all of these cameras ship with a factory-default peer-to-peer (P2P) communications capability that enables remote “cloud” access to the devices via the manufacturer’s Web site — provided a customer visits the site and provides the unique camera ID stamped on the bottom of the devices.
Although it may seem that attackers would need physical access to the vulnerable devices in order to derive those unique camera IDs, Cybereason’s principal security researcher Amit Serper said the company figured out a simple way to enumerate all possible camera IDs using the manufacturer’s Web site.
“We reverse engineered these cameras so that we can use the manufacturer’s own infrastructure to access them and do whatever we want,” Serper said. “We can use the company’s own cloud network and from there jump onto the customer’s network.”
Lior Div, co-founder and CEO at Cybereason, said a review of the code built into these devices shows the manufacturer does not appear to have made security a priority, and that people using these devices should simply toss them in the trash.
“There is no firmware update mechanism built into these cameras, so there’s no way to patch them,” Div said. “The version of Linux running on these devices was in some cases 14 years old, and the other code libraries on the devices are just as ancient. These devices are so hopelessly broken from a security perspective that it’s hard to really understand what’s going on in the minds of people putting them together.”
Cybereason said it is not disclosing full technical details of the flaws because it would enable any attacker to compromise them for use in online attacks. But it has published a few tips that should help customers determine whether they have a vulnerable device. For example, the camera’s password (888888) is printed on a sticker on the bottom of the devices, and the UID — also printed on the sticker — starts with one of these text strings:
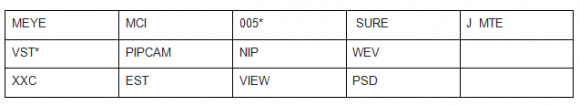

The sticker on the bottom of the camera will tell you if the device is affected by the vulnerability. Image: Cybereason.
“People tend to look down on IoT research and call it junk hacking,” Cybereason’s Yoav Orat wrote in a blog post about its findings. “But that isn’t the right approach if researchers hope to prevent future Mirai botnet attacks. A smart (insert device here) is still a computer, regardless of its size. It has a processor, software and hardware and is vulnerable to malware just like a laptop or desktop. Whether the device records The Walking Dead or lets you watch your cat while you’re at work, attackers can still own it. Researchers should work on junk hacking because these efforts can improve device security (and consumer security in the process), keep consumer products out of the garbage heap and prevent them from being used to carry out DDoS attacks.”
The discoveries by SEC Consult and Cybereason come as policymakers in Washington, D.C. are grappling with what to do about the existing and dawning surge in poorly-secured IoT devices. A blue-ribbon panel commissioned by President Obama issued a 90-page report last week full of cybersecurity policy recommendations for the 45th President of the United States, and IoT concerns and addressing distributed denial-of-service (DDoS) attacks emerged as top concerns in that report.
Meanwhile, Morning Consult reports that U.S. Federal Communications Commission Chairman Tom Wheeler has laid out an unexpected roadmap through which the agency could regulate the security of IoT devices. The proposed certification process was laid out in a response to a letter sent by Sen. Mark Warner (D-Va.) shortly after the IoT-based attacks in October that targeted Internet infrastructure company Dyn and knocked offline a number of the Web’s top destinations for the better part of a day.
Morning Consult’s Brendan Bordelon notes that while Wheeler is set to step down as chairman on Jan. 20, “the new framework could be used to support legislation enhancing the FCC’s ability to regulate IoT devices.”
Tags: 888888, Amit Serper, CVE-2015-7755, Cybereason, internet of things, IoT, Johannes Greil, Juniper ScreenOS Backdoor, Lior Div, mirai, SEC Consult, SNC Toolbox, Sony IPELA Engine IP Cameras
This entry was posted on Tuesday, December 6th, 2016 at 10:22 am and is filed under Other. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.
