Adobe Fined $1M in Multistate Suit Over 2013 Breach; No Jail for Spamhaus Attacker
Twitter CEO apologizes for allowing white supremacist ad
November 17, 2016Google, an Obama ally, may face policy setbacks under Trump
November 17, 2016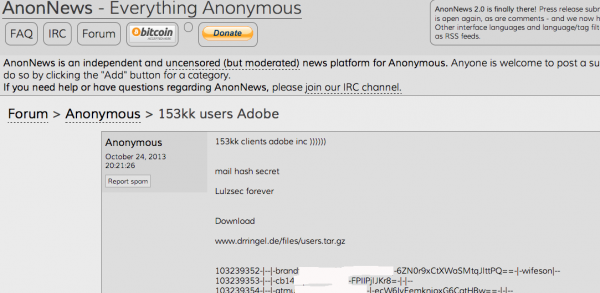
Adobe will pay just $1 million to settle a lawsuit filed by 15 state attorneys general over its huge 2013 data breach that exposed payment records on approximately 38 million people. In other news, the 39-year-old Dutchman responsible for coordinating an epic, weeks-long distributed denial-of-service attack against anti-spam provider Spamhaus in 2013 will avoid any jail time for his crimes thanks to a court ruling in Amsterdam this week.
On Oct. 3, 2013, KrebsOnSecurity broke the story that Adobe had just suffered a breach in which hackers siphoned usernames, passwords and payment card data on 38 million customers. The intruders also made off with digital truckloads of source code for some of Adobe’s most valuable software properties — including Adobe Acrobat and Reader, Photoshop and ColdFusion.
On Monday, Nov. 11, North Carolina Attorney General Roy Cooper joined his counterparts in 14 other states in announcing a $1 million settlement with Adobe over the 2013 breach. According to Cooper, the hacked Adobe servers contained the personal information of approximately 552,000 residents of the participating 15 states. That works out to about $1.80 per victim across all 15 states.
According to a statement by Massachusetts Attorney General Maura Healey, “an investigation by the states revealed that in September 2013, Adobe received an alert that the hard drive for one of its application servers was nearing capacity. In responding to the alert, Adobe learned that an unauthorized attempt was being made to decrypt customer payment card numbers maintained on the server.”
“Adobe discovered that one or more unauthorized intruder(s) had compromised a public-facing web server and used it to access other servers on Adobe’s network, including areas where Adobe stored consumer data,” the statement from Healey’s office reads. “The intruder(s) ultimately stole consumer data from Adobe’s servers, including encrypted payment card numbers and expiration dates, names, addresses, telephone numbers, e-mail addresses, usernames (Adobe IDs), and passwords associated with the usernames.”
When I think of the Adobe breach I’m reminded of that scene out of the 1982 Spielberg horror classic “Poltergeist,” when Craig T. Nelson as “Steve Freeling” seizes the horrified neighborhood developer Mr. Teague by his coat collars and screams, “You son of a bitch! You moved the cemetery but you left the bodies, didn’t ya?! You left left the bodies and you only moved the headstones!! Why?!?!?! Whyyyyyyeeeiee??!?!?”

A scene from Poltergeist. Image: IMDB.
Likewise, Adobe had various storefronts for its various software products, but it eventually began to centralized many store operations. The main trouble was the company left copies of their customer records in multiple internal network locations that were no longer as protected as Adobe’s globally centralized storefront.
North Carolina’s Cooper said in a statement on the settlement that businesses and government must do more to protect consumer data. But if this settlement was meant as a deterrent to dissuade other companies from hosting customer payment data on public-facing Web servers, the fine might be more effective if it were more commensurate with the company’s size and the number of customers impacted.
As Digital Trends notes, such a breach under the new General Data Protection Regulation going into effect in 2018, would be quite a bit more costly. “Adobe could face fines of up to four percent of its annual global turnover,” wrote Jonathan Keane for DT. “Last we checked, Adobe’s previous quarterly earnings were $1.4 billion.”
Keane also notes that Adobe had previously settled a similar case in California where it settled for an undisclosed amount and $1.1 million in legal fees.
One interesting nugget tucked in at the end of the statement from the North Carolina AG’s office is this bit: More than 3,700 breaches impacting nearly 10 million North Carolinians have been reported since the state’s data breach notification law took effect in 2005, including 677 breaches reported so far in 2016. According to the United States Census Bureau, there were just over 10 million residents in North Carolina as of July 2015.
That means just about everyone in North Carolina was impacted by at least one data breach over the past 12 years. I’d wager this is true for just about every state in the Union, and probably many times over for some. A handful of lucky states have had single breaches that affected all citizens at once.
In 2012, a phishing attack against an employee of the South Carolina Department of Revenue allowed intruders to make off with Social Security numbers and other personal data on 3.8 million electronic tax filers, as well as 1.9 million of their dependents. Also in that breach, nearly 700,000 businesses, 3.3 million bank accounts and 5,000 expired credit cards were compromised. As of July 2015, South Carolina had fewer than five million residents, according to the Census Bureau.
SVEN OLAF KAMPHUIS — A.K.A. “Prince of Cyberbunker Republic”
In March 2013, a coalition of spammers and spam-friendly hosting firms pooled their resources to launch what would become the largest distributed denial-of-service (DDoS) attack the Internet had ever witnessed. The assault briefly knocked offline the world’s largest anti-spam organization, and caused a great deal of collateral damage to innocent bystanders in the process. Here’s a never-before-seen look at how that attack unfolded, and a rare glimpse into the shadowy cybercrime forces that orchestrated it.
That paragraph above was the lead for a story I published in August 2016, “Inside the Attack that Almost Broke the Internet“. It’s starring member was a colorful Dutchman named Sven Olaf Kamphuis who ran a technology services company called CB3ROB. This CB3ROB in turn provided services for a Dutch company called “Cyberbunker,” so named because the organization was allegedly housed in a five-story NATO bunker and because it had advertised its services as a bulletproof hosting provider.
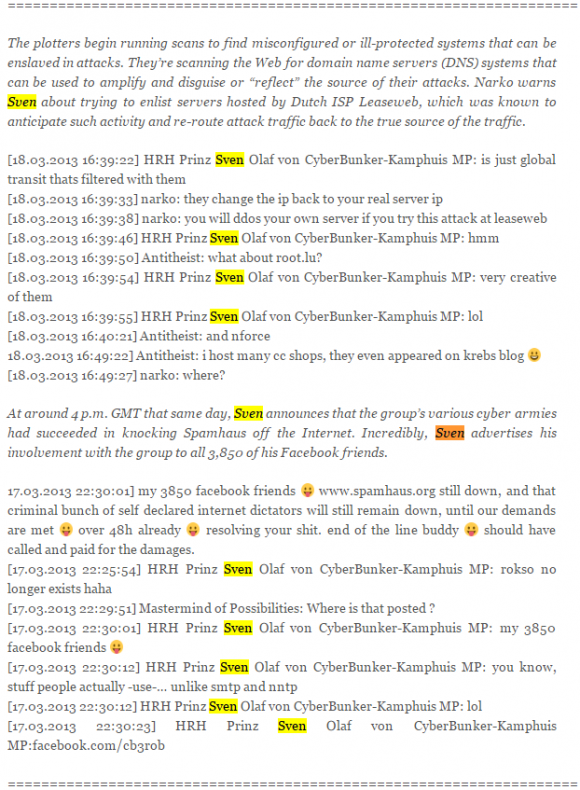
A snippet from a very long chat log published here detailing the extended DDoS campaigns waged against Spamhaus.
Kamphuis seemed to honestly believe his Cyberbunker was sovereign territory, even signing his emails “Prince of Cyberbunker Republic.” Arrested in Spain in April 2013 in connection with the attack on Spamhaus, Kamphuis was later extradited to The Netherlands to stand trial. He has publicly denied being part of the attacks, but the chat logs with him coordinating the attack with co-conspirators are fairly damning considering he didn’t even use an alias in the discussions and live-posted his campaign of terror to his Facebook account.
Nevertheless, a judge in Amsterdam this week sentenced Kamphuis to a total of 240 days in jail. However, the judge also counted the 55 days Kamphuis spent awaiting extradition from Spain, and suspended the remaining 185-day sentence. No jail time for Kamphuis.
Spamhaus founder Steve Linford said the organization was disappointed in the sentence, and it warned Kamphuis about any thoughts of retaliation.
“We had hoped for a longer jail sentence to send the message that organising and conducting DDoS attacks is a crime not acceptable to law courts or society, however the ease with which Kamphuis was arrested and extradited, and the two months already served in jail will hopefully have delivered the message to him that there is no escape from the law should he attempt any attacks in the future,” Linford wrote in a email. “Since the remainder of the term is a suspended sentence, any actions or threats made to Spamhaus during the term would be filed with the court as a violation of the conditions of the suspended sentence.”

Facebook profile picture of Sven Olaf Kamphuis
The only other person charged in connection with the largest attack the Internet had ever seen at the time was Sean Nolan McDonough, a.k.a. “narko” in the chat logs referenced in the snippet pictured above.
Narko was a juvenile when he was arrested by the U.K.’s National Crime Agency (NCA); when the NCA raided Narko’s home, they found his computer still logged in to crime forums, and they seized £70,000 from his bank account (believed to be payments for DDoS attacks). Narko later pleaded guilty to coordinating the attacks and was sentenced to 240 hours of community service, but because of his age and in return for cooperating with the NCA he avoided a jail term.
This sentence sends the wrong message and misses the mark by a mile. The message we as a society of Internet users continue to send by our unwillingness to punish people for these crimes is, “Hey, if you’re involved in heavily disrupting networks and commerce through botnet attacks, you don’t have to worry because you’ll either never be prosecuted…or if you are the sentence will be community service or nothing.”
Neither of the two 18-year-old Israeli men arrested in September for their role in selling the massively profitable vDOS attack-for-hire service to knock Web sites offline have been indicted by the Israeli, British or American governments. The hammer has yet to fall on those responsible for lobbing the record 620 Gpbs attack on my site, or the individual(s) involved in the attack on Dyn that disrupted service for some of the Web’s top destinations. I’m afraid the wheels of justice still creak forward far too slowly in Internet time for the threat of prosecution to be much of an immediate deterrent against online hooliganism in the here-and-now.
Tags: adobe, CB3ROB, Cyberbunker, Jonathan Keane, Maura Healey, Narko, National Crime Agency, Poltergeist, Roy Cooper, Sean Nolan McDonough, spamhaus, Steve Linford, Sven Olaf Kamphuis, vDos
This entry was posted on Thursday, November 17th, 2016 at 4:04 pm and is filed under Other. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.
