Justice Dept. Claws Back $2.3M Paid by Colonial Pipeline to Ransomware Gang
Adventures in Contacting the Russian FSB
June 7, 2021Microsoft Patches Six Zero-Day Security Holes
June 8, 2021The U.S. Department of Justice said today it has recovered $2.3 million worth of Bitcoin that Colonial Pipeline paid to ransomware extortionists last month. The funds had been sent to DarkSide, a ransomware-as-a-service syndicate that disbanded after a May 14 farewell message to affiliates saying its Internet servers and cryptocurrency stash were seized by unknown law enforcement entities.

On May 7, the DarkSide ransomware gang sprang its attack against Colonial, which ultimately paid 75 Bitcoin (~$4.4 million) to its tormentors. The company said the attackers only hit its business IT networks — not its pipeline security and safety systems — but that it shut the pipeline down anyway as a precaution [several publications noted Colonial shut down its pipeline because its billing system was impacted, and it had no way to get paid].
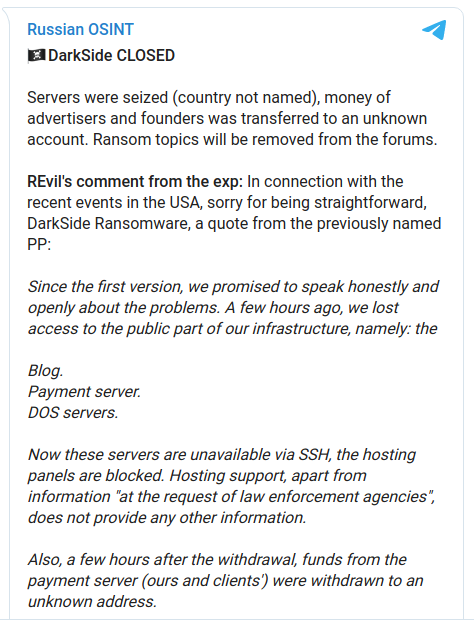
On or around May 14, the DarkSide representative on several Russian-language cybercrime forums posted a message saying the group was calling it quits.
“Servers were seized, money of advertisers and founders was transferred to an unknown account,” read the farewell message. “Hosting support, apart from information ‘at the request of law enforcement agencies,’ does not provide any other information.”
A message from the DarkSide and REvil ransomware-as-a-service cybercrime affiliate programs.
Many security experts said they suspected DarkSide was just laying low for a while thanks to the heat from the Colonial attack, and that the group would re-emerge under a new banner in the coming months. And while that may be true, the seizure announced today by the DOJ certainly supports the DarkSide administrator’s claims that their closure was involuntary.
Security firms have suspected for months that the DarkSide gang shares some leadership with that of REvil, a.k.a. Sodinokibi, another ransomware-as-a-service platform that closed up shop in 2019 after bragging that it had extorted more than $2 billion from victims. That suspicion was solidified further when the REvil administrator added his comments to the announcement about DarkSide’s closure (see screenshot above).
First surfacing on Russian language hacking forums in August 2020, DarkSide is a ransomware-as-a-service platform that vetted cybercriminals can use to infect companies with ransomware and carry out negotiations and payments with victims. DarkSide says it targets only big companies, and forbids affiliates from dropping ransomware on organizations in several industries, including healthcare, funeral services, education, public sector and non-profits.
According to an analysis published May 18 by cryptocurrency security firm Elliptic, 47 cybercrime victims paid DarkSide a total of $90 million in Bitcoin, putting the average ransom payment of DarkSide victims at just shy of $2 million.
HOW DID THEY DO IT?
The DoJ’s announcement left open the question of how exactly it was able to recover a portion of the payment made by Colonial, which shut down its Houston to New England fuel pipeline for a week and prompted long lines, price hikes and gas shortages at filling stations across the nation.
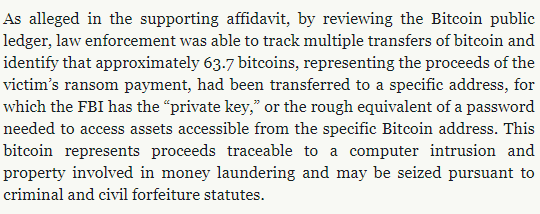
The DOJ said law enforcement was able to track multiple transfers of bitcoin and identify that approximately 63.7 bitcoins (~$3.77 million on May 8), “representing the proceeds of the victim’s ransom payment, had been transferred to a specific address, for which the FBI has the ‘private key,’ or the rough equivalent of a password needed to access assets accessible from the specific Bitcoin address.”
A passage from the DOJ’s press release today.
How it came to have that private key is the key question. Nicholas Weaver, a lecturer at the computer science department at University of California, Berkeley, said the most likely explanation is that law enforcements agent seized money from a specific DarkSide affiliate responsible for bringing the crime gang the initial access to Colonial’s systems.
“The ‘obtained the private key’ part of their statement is doing a lot of work,” Weaver said, point out that the amount the FBI recovered was less than the full amount Colonial paid.
“It is ONLY the Colonial Pipeline ransom, and it looks to be only the affiliate’s take.”
Experts at Elliptic came to the same conclusion.
“Any ransom payment made by a victim is then split between the affiliate and the developer,” writes Elliptic’s co-founder Tom Robinson. “In the case of the Colonial Pipeline ransom payment, 85% (63.75 BTC) went to the affiliate and 15% went to the DarkSide developer.”
The Biden administration is under increasing pressure to do something about the epidemic of ransomware attacks. In conjunction with today’s action, the DOJ called attention to the wins of its Ransomware and Digital Extortion Task Force, which have included successful prosecutions of crooks behind such threats as the Netwalker and SamSam ransomware strains.
The DOJ also released a June 3 memo from Deputy Attorney General Lisa O. Monaco instructing all federal prosecutors to adhere to new guidelines that seek centralize reporting about ransomware victims.
Having a central place for law enforcement and intelligence agencies to gather and act on ransomware threats was one of the key recommendations of a ransomware task force being led by some of the world’s top tech firms. In an 81-page report, the industry led task force called for an international coalition to combat ransomware criminals, and for a global network of investigation hubs. Their recommendations focus mainly on disrupting cybercriminal ransomware gangs by limiting their ability to get paid, and targeting the individuals and finances of the organized thieves behind these crimes.
