Feds Charge Two In Lizard Squad Investigation
Deutsche Post van signals new entrant threat to auto industry
October 6, 2016FCC to vote on revised broadband privacy regulations
October 6, 2016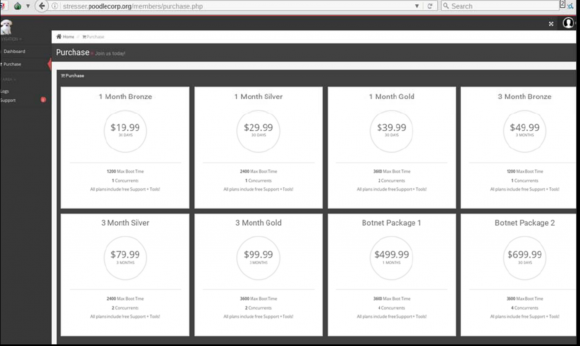
The U.S. Justice Department has charged two 19-year-old men alleged to be core members of the hacking groups Lizard Squad and PoodleCorp. The pair are charged with credit card theft and operating so-called “booter”or “stresser” services that allowed paying customers to launch powerful attacks designed to knock Web sites offline.

The PoodleCorp/PoodleStresser attack-for-hire service. Image: USDOJ.
Federal investigators charged Zachary Buchta of Fallston, Md., and Bradley Jan Willem Van Rooy of Leiden, the Netherlands with conspiring to cause damage to protected computers.
According to a statement from the U.S. Attorney’s Office for the Northern District of Illinois, Buchta, “who used the online screen names “@fbiarelosers,” “pein,” “xotehpoodle” and “lizard,” and van Rooy, who used the names “Uchiha,” “@UchihaLS,” “dragon” and “fox,” also conspired with other members of Lizard Squad to operate websites that provided cyber-attack-for-hire services, facilitating thousands of denial-of-service attacks, and to traffic stolen payment card account information for thousands of victims.”
The PoodleCorp’s “Poodlestresser” attack-for-hire service appears to have drawn much of its firepower using an application programming interface (API) set up by the proprietors of vDOS — a similar attack service that went offline last month following the arrest of two 18-year-old Israeli men who allegedly ran vDOS.
vDOS was hacked earlier this summer, and a copy of the user database was shared with KrebsOnSecurity. The database indicates that Poodlestresser was among vDOS’s biggest clients, and that KrebsOnSecurity was a frequent target of the attack-for-hire services.
Federal investigators allege that van Rooy and Buchta also operated a service called phonebomber[dot]net, a site that enabled paying customers to select victims to receive repeated harassing and threatening phone calls from spoofed phone numbers. The service, which cost $20 per month, would call the target number once per hour with pre-recorded messages. Here’s one of those messages, according to the Justice Department:
“When you walk the fucking streets, Motherfucker, you better look over your fucking back because I don’t flying fuck if we have to burn your fucking house down, if we have to fucking track your goddamned family down, we will fuck your shit up motherfuck.”
According to a complaint (PDF) filed by the United States Attorney for the Northern District of Illinois, at least one incarnation of the attack-for-hire services included a section where customers could purchase stolen credit cards. The government alleges that the card shop contained approximately 347 pages of payment card data available for purchase with each page appearing to contain approximately ten records per page.
Buchta was arrested last month in Maryland and was slated to make an initial court appears in Chicago on Wednesday. Authorities in the Netherlands arrested van Rooy last month and he remains in custody there. The conspiracy charge carries a maximum sentence of ten years in prison.
Tags: Bradley Jan Willem Van Rooy, Lizard Squad, pein, PoodleCorp, PoodleStresser, uchiha, xotehpoodle, Zachary Buchta
This entry was posted on Thursday, October 6th, 2016 at 11:24 am and is filed under Other. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.
