Sprint, T-Mobile iPhone pre-orders boost Apple shares
September 13, 2016NY issues cyber regulations for banks, insurers
September 13, 2016The U.S. Secret Service is warning banks and ATM owners about a new technological advance in cash machine skimming known as “periscope skimming,” which involves a specialized skimming probe that connects directly to the ATM’s internal circuit board to steal card data.
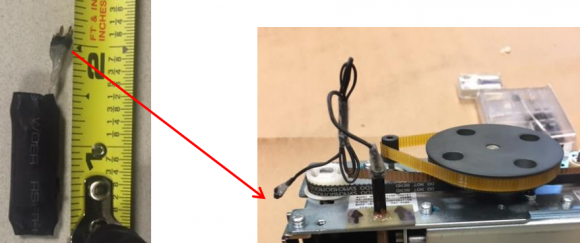
At left, the skimming control device. Pictured right is the skimming control device with wires protruding from the periscope. These were recovered from a cash machine in Connecticut.
According to a non-public alert released to bank industry sources by a financial crimes task force in Connecticut, this is thought to be the first time periscope skimming devices have been detected in the United States. The task force warned that the devices may have the capability to remain powered within the ATM for up to 14 days and can store up to 32,000 card numbers before exhausting the skimmer’s battery strength and data storage capacity.
The alert documents the first known case of periscope skimming in the United States, discovered Aug. 19, 2016 at an ATM in Greenwich, Conn. A second periscope skimmer was reportedly found hidden inside a cash machine in Pennsylvania on Sept. 3.
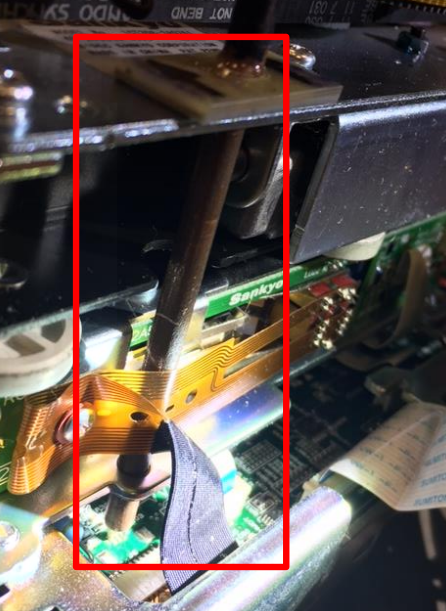
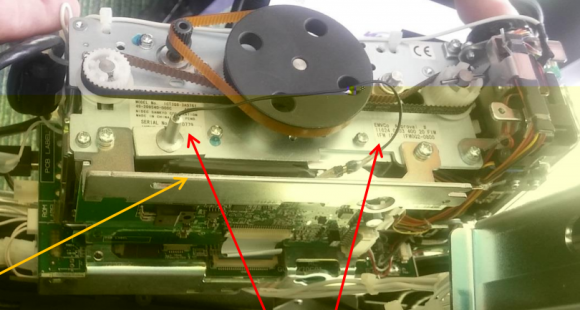
The task force alert notes that in both cases the crooks were able to gain direct access to the insides of the ATMs (referred to as “top-hat” entry) with a key. The suspects then installed two devices connected together by wiring. The first device — the periscope skimming probe — is installed through a pre-existing hole on the frame of the motorized card reader.
The probe is set in place to connect to the circuit board and directly onto the pad that transfers cardholder data stored on the magnetic stripe on the backs of customer payment cards. The probe is then held in place with fast-drying superglue to the card reader frame.
According to the Secret Service, the only visible part of this skimming device once the top-hat is opened will be the wire extending from the periscope probe that leads to the second part of this skimmer — called a “skimming control device.” This second device contains the battery source and data storage unit, and looks similar to a small external hard drive.
As I’ve noted in previous stories in my series All About Skimmers, the emergence of this type of skimming attack is thought to be response to the widespread availability of third party anti-skimming technology which is successful at preventing the operation of a traditional skimmer placed on the outside of the ATM.
The Connecticut task task force notes that authorities there did not find hidden cameras or other methods of capturing customer PINs at the ATMs compromised by periscope skimmers, suggesting these attacks involved mere prototypes and that the thieves responsible are in the process of refining their technology.
Nevertheless, crooks who are serious about this type of crime eventually will want to capture your PIN so they can later drain your debit account at another ATM. So it’s important to remember that covering the PIN pad with your hand defeats the hidden camera from capturing your PIN. Occasionally, skimmer thieves will use PIN pad overlays, but these are comparatively rare and quite a bit more expensive; hidden cameras are used on the vast majority of the more than three dozen ATM skimming incidents that I’ve documented here.
Shockingly, few people bother to take this simple, effective step, as detailed in this skimmer tale from 2012, wherein I obtained hours worth of video seized from two ATM skimming operations and saw customer after customer walk up, insert their cards and punch in their digits — all in the clear.
Many readers have asked whether the incidence of such skimming scams will decrease as more banks begin issuing more secure chip-based payment cards. The answer is probably not. That’s because even after most U.S. banks put in place chip-capable ATMs, the magnetic stripe will still be needed because it’s an integral part of the way ATMs work: Most ATMs in use today require a magnetic stripe for the card to be accepted into the machine.
The principal reason for this is to ensure that customers are putting the card into the slot correctly, as embossed letters and numbers running across odd spots in the card reader can take their toll on the machines over time. As long as the cardholder’s data remains stored on a chip card’s magnetic stripe, thieves will continue building and placing these types of skimmers.
Also, the thieves conducting these periscope skimming attacks don’t necessarily need a key to access the ATMs. As I’ve noted in past skimming stories, crooks who specialize in compromising ATMs with malicious software often target stand-alone cash machines that may be easier to access from the top-hat. My advice? Stick to ATMs that are installed in the wall at a bank or otherwise not exposed from the top.
Most importantly, watch out for your own physical safety while using an ATM. Keep your wits about you as you transact in and leave the area, and try to be keenly aware of your immediate surroundings. Use only machines in public, well-lit areas, and avoid ATMs in secluded spots.